- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: R80.40 NAT Usage/Utilisation request - any cha...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
R80.40 NAT Usage/Utilisation request - any chances for the useful "extract"?
hi guys
quick one
I've got a MTO customer who due to the migration process is required to provide following data:
1. NAT usage/utilisation on each of the DC firewalls (4000/5000 series of HA's) - bear in mind that NAT rules are per-gateway.
2. NAT differentiations (Machine NAT, Network NAT, Static NAT, Hide NAT etc.)
Question:
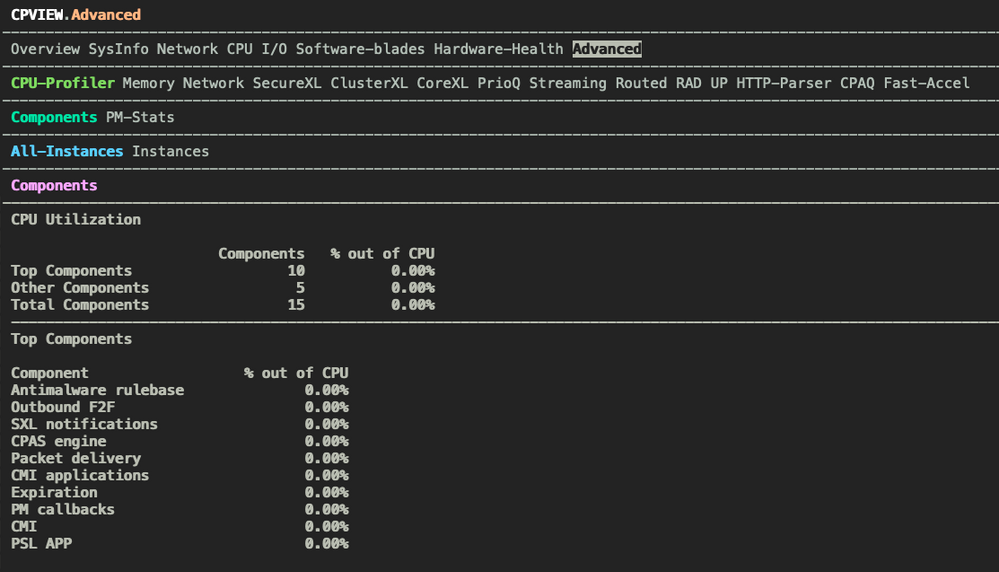
how they can get that information by the most convinient way from the Gateways (SMS) should they NOT have CPVIEW capability on R80.40 which shows lots on Advance tab, should they have expert/admin access to each device but so much decapacitated due to the age of the Gaia build? All they need is the stats of the usage of their NAT policies (there is roughly around 150-200 NAT policies only with mixture mentioned above.
T.files - yes, but in HEX - any other clues?
Any hints? They'd much appreciate it.
Cheers
Jerry
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume the reason cpview doesn’t show information in versions prior to R81 is because the infrastructure to track NAT rule utilization simply doesn’t exist in earlier versions.
The only other way to do this is analyzing the logs, which has its own issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can try poking around in the NAT cache to get some idea of the most commonly hit NAT rules. This was mentioned in my Max Power book which was written before the extra NAT cpview screens were added:
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi
yes I know that FAQ and there is nothing related to my topic I'm afraid, did you understand what my customer is after?
There are no issues with NAT except ... CP Build - R80.40 (as this cannot be upgraded at this time) hence our hands are tight as we do not have much tools (including CCC) which shows NAT rules utilisation. None of the links you've provided leads to any conclusions though nor to any useful information sorry. Am I blind then or I'm missing something here?
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CPVIEW by R80.40 does not show NAT at all hence my reiteration on that. Due to this missing bit (it isn't there simply until R81) they've got no other option to see utilisation/usage of their NAT rules. FAQ has nothing to do with it as PORT USAGE is not what I was asking about.
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
NAT:
2376649/0 forw, 2897027/0 bckw, 69484456 tcpudp,
340322 icmp, 32985755-16777499 alloc
*** not really of use so much ***
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
is that seriously R80.40? it seems to me that this isn't really that one, instead R81. See Dameon's post here. There was no facilty in CPVIEW code to gather NAT's in Adcance-NAT pattern.
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Perhaps it’s related to the JHF level.
Having said that, there’s no obvious mention in the R80.40 JHF notes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All lovely but unfortunately still it does not help my Customer who by running R80.40 cannot effectively assess which of their NAT rules should be considered as priority for the MTO.
As a unlucky factor they also noted that by not using any 3rd party policies orchestartion nor any SIEM they've shoot themselves in the foot now when the time has come for the MTO preparations and migartions off CP. They plan to eliminate "anything CP" within the next year as most of their stuff runs out of support and many are already EOL H/W wise so I believe you can guess which vendor they decided to go for instead hence now the priority is to assess whatever possible (on gaia, smartconsole) and take this forward with us (MSP) towards another architecture.
shame we cannot assess other than by the logs, which NAT rules are used and/or completely unused.
any hints/tips highly welcomed as always chaps.
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume the reason cpview doesn’t show information in versions prior to R81 is because the infrastructure to track NAT rule utilization simply doesn’t exist in earlier versions.
The only other way to do this is analyzing the logs, which has its own issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nobody will risk an upgrade process on already outdated H/W so knowing that R80.40 is the latest supported build for their 4000/5000 gear would make no sense I'm afirad 😞
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do read english and have no issues with that mate 🙂 I'm happy you've corrected your post so quickly but emails shows your complete ignorance of the fact that I have wrote above one little line: "nobody will risk an upgrade process" - that INCLUDE take/jhf install. so now who's english lacks? 😛
anyway, that's not the place for arguments hence I was hoping I'm making myself clear enough, looks like many bi-lingual ppl here still struggle, fair enough so let's make sure we're on the same page.
Customer is not willing to touch their builds just to see NAT page on CPVIEW. Period.
Hope that this is indeed clarified 4ever now.
Reg. the issue itself - I presume R80.40 JHF 139 as it stands does NOT support NAT details by CPVIEW. Am I correct?
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Jerry & @G_W_Albrecht, please refrain from personal attacks in this forum. We expect all the members to behave professionally.
Thanks,
admin team
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi Val, ABSOLUTELY AGREE, I never ever intend to do anything like that but unfortunatelly I've just defended myself. It's not me who started, see below:
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please stop, both of you. Or else 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can try poking around in the NAT cache to get some idea of the most commonly hit NAT rules. This was mentioned in my Max Power book which was written before the extra NAT cpview screens were added:
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Grand Tim! That's the answer I was waiting for 🙂 excellent and spot on!
Much appreciate it, we'll give it a try with the Customer and update you all due course,
Cheers and thanks to all!
Jerry
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 17 | |
| 7 | |
| 6 | |
| 6 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Wed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter