- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: R80.20 cheat sheet - fw monitor
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.20 cheat sheet - fw monitor
| Introduction |
|---|
This overview gives you an view of the changes in R80.20 fw monitor. All R80.10 and R80.20 changes are contained in this command overview (cheat sheet). You could download the cheat sheet at the end of this article as a PDF file. Unfortunately not all information for R80.20 is included in SK30583 "What is FW Monitor?". Therefore this small overview with the changes. I hope it helps you.
| Cheat Sheet |
|---|
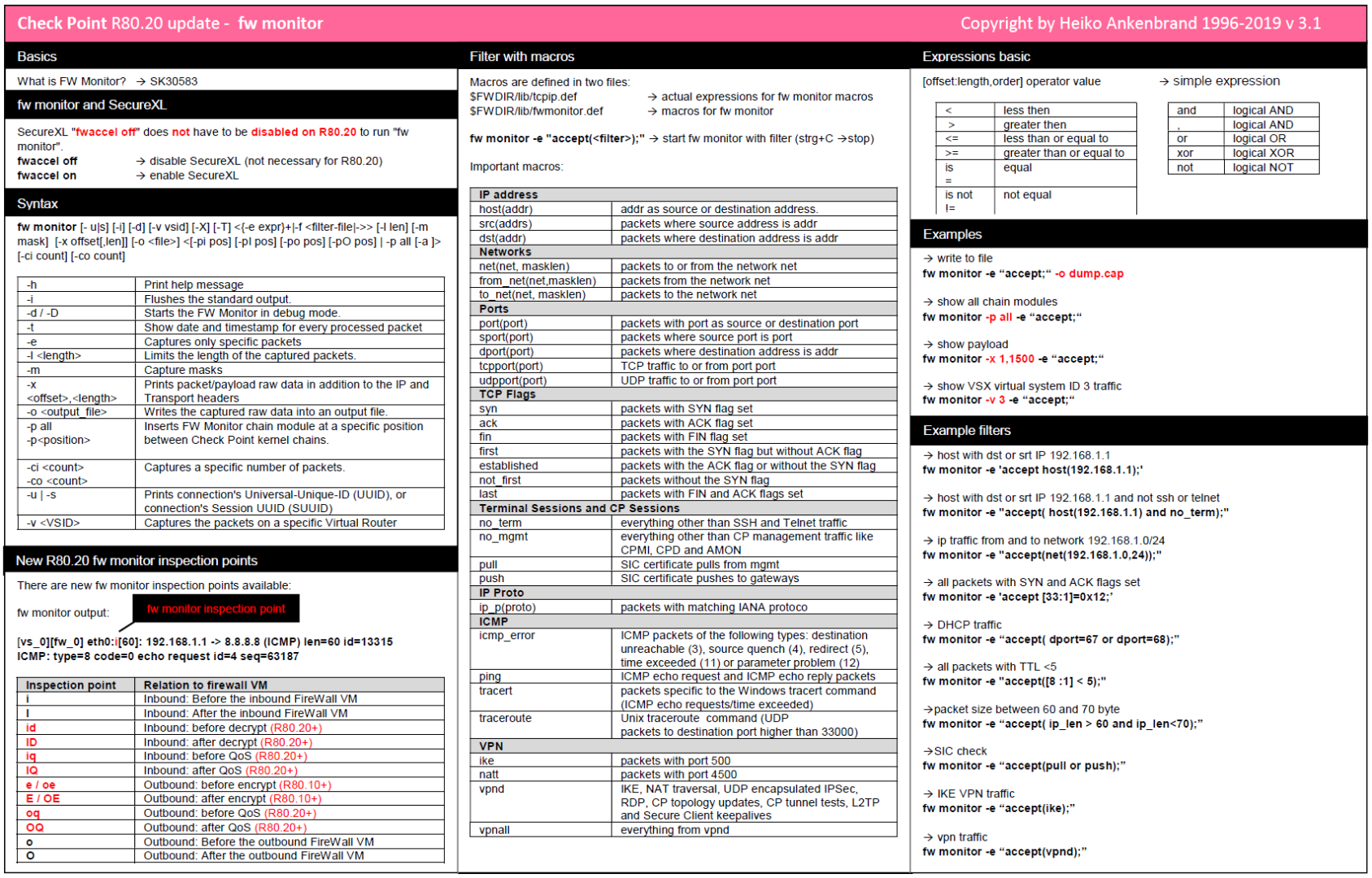
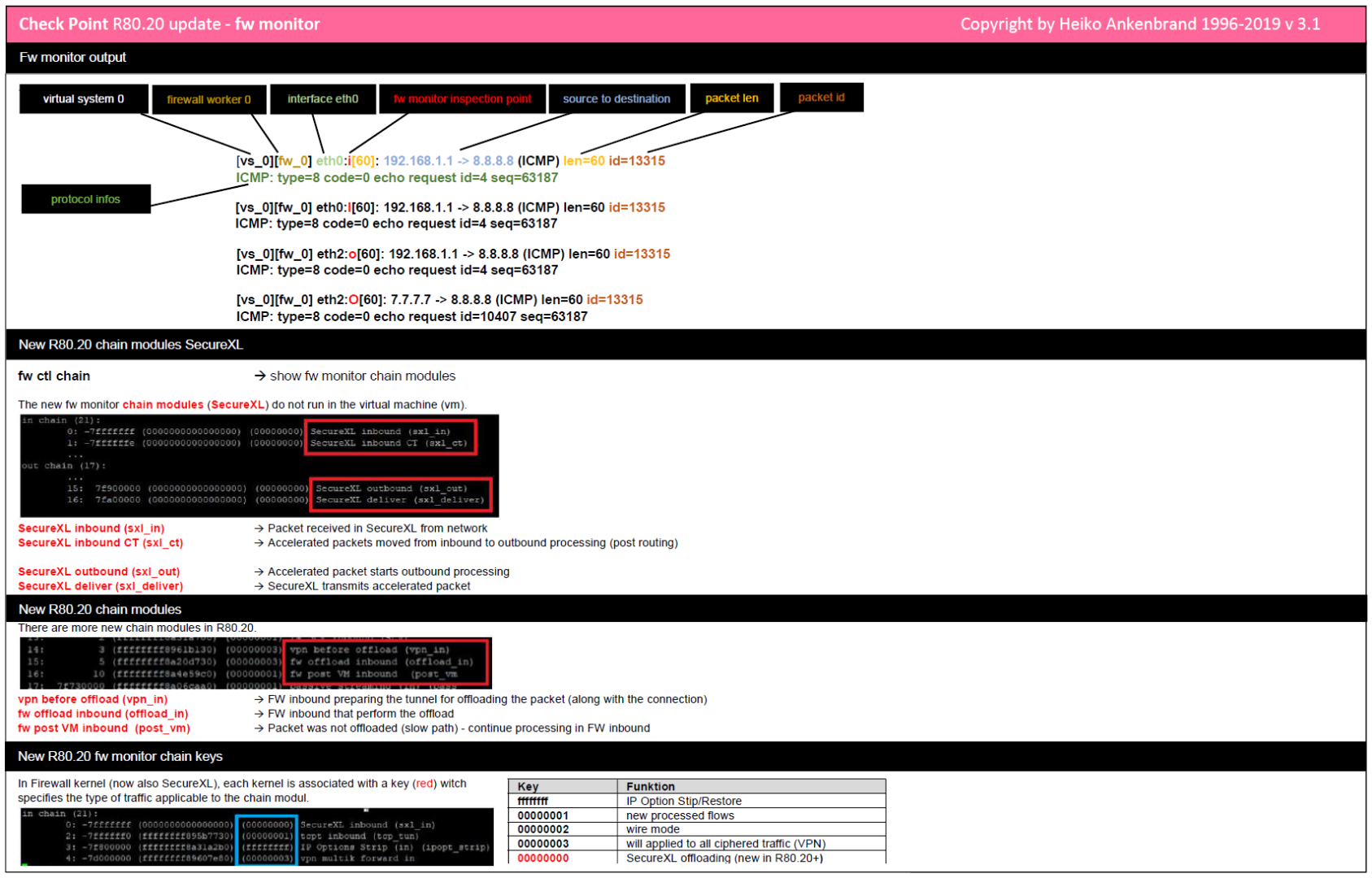
| Download |
|---|
Download: R80.20 fw monitor cheat sheet PDF (new R80.20 version)
| Chapter |
|---|
More interesting articles:
- R80.x Architecture and Performance Tuning - Link Collection
- Article list (Heiko Ankenbrand)
Cheat Sheet:
- R80.x cheat sheet - fw monitor
- R80.x cheat sheet - ClusterXL
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Tags:
- 00000000
- 00000001
- 00000002
- 00000003
- accept
- ack
- chain
- chain key
- cheat sheet
- cli
- command
- dport
- dst
- ffffffff
- fin
- fw ctl chain
- fw monitor
- fw offload inbound
- fw post vm inbound
- fwaccel off
- fwaccel on
- host
- id
- iq
- modules
- oe
- offload_in
- oq
- performance
- post_vm
- r77.30
- r80.10
- r80.20
- reverence
- rst
- securexl deliver
- securexl inbound
- securexl inbound ct
- securexl outbound
- sport
- src
- sxl_ct
- sxl_deliver
- sxl_in
- sxl_out
- syn
- vpn before offload
- vpn_in
- vsx
40 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Copied from sk30583:
Note: Relevant for R80.20 from Jumbo Hotfix Accumulator for R80.20 (Take 73)
[-w whole packet] [-F simple filter "{src IP},{src port},{dst IP},{dst port},{protocol num}"] [-U clear]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-F: any hint how to filter for networks instead of single IP addresses?
10.1.1.0/24 --> doesn't filter at all
10.1.1.0/255.255.255.0 --> "Set operation failed: failed to get parameter simple_debug_filter_saddr_1"
10.1.1.0,24: --> oviously not possible
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check Point's documentation is vague on exactly how the filter should look. They include braces. That looks like JSON. Should the filter be in the form of a JSON object? A list of objects? Can't tell, since they don't include any examples.
I just tested and this exact form worked for me:
[Expert@MyFW ACTIVE]# fw monitor -F "10.20.30.40,0,0,0,0"
FW monitor will record only ip & transport layers in a packet
For capturing the whole packet please do -w
monitor: getting filter (from command line)
monitor: compiling
monitorfilter:
Compiled OK.
monitor: loading
monitor: monitoring (control-C to stop)
[vs_0][fw_0] bond1.2345:i[44]: 10.20.30.40 -> 192.168.128.64 (TCP) len=1000 id=45972
TCP: ***** -> ***** ...PA. seq=******** ack=********
[vs_0][fw_0] bond1.2345:i[40]: 10.20.30.40 -> 192.168.128.64 (TCP) len=40 id=45973
TCP: ***** -> ***** ....A. seq=******** ack=********
[vs_0][fw_0] bond1.2345:i[40]: 10.20.30.40 -> 192.168.128.64 (TCP) len=40 id=45974
TCP: ***** -> ***** ....A. seq=******** ack=********
monitor: caught sig 2
monitor: unloading
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even more vague is the answer to how we can capture traffic post-outbound O without the need to add another filter with the NATted address.
As described in the examples on the bottom of the SK:
fw monitor -F "x.x.x.x,0,y.y.y.y,0,0" -F "y.y.y.y,0, x.x.x.x ,0,0"
Filter 1: source ip: x.x.x.x, source port: any, destination ip: y.y.y.y, destination port: any, protocol: any.
Filter 2: source ip: y.y.y.y, source port: any, destination ip: x.x.x.x, destination port: any, protocol: any.
This does not take into account a (possible) NAT translation and thus will not capture/display it.
Any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Jan_Boonen Use AND expression and include NAT-ed address, if you know it. Alternatively, use source or destination alone for the IP that is not NAT-ed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw monitor is thoroughly described in the CLI admin guide
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Several aspects are described in the CLI reference guide, but not all.
Specifically, there are no examples of filters (either INSPECT or simple).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are adding those "as we speak"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Normally, we can insert inspection points in different parts of the chain (fw ctl chain). But when trying to insert at the very beginning, it complains:
fw monitor -F "x.x.x.x,0,0,0,0" -F "0,0,x.x.x.x,0,0" -pi 0 -ci 10 -co 10
...
monitor: No room for inbound module before SecureXL stateless checkTried -pi 1 and -pi 3 with messages saying
-pi 1 "monitor: No room for inbound module before SecureXL VPN before decryption"
-pi 3 "monitor: position 5 is already occupied by fw offload inbound"
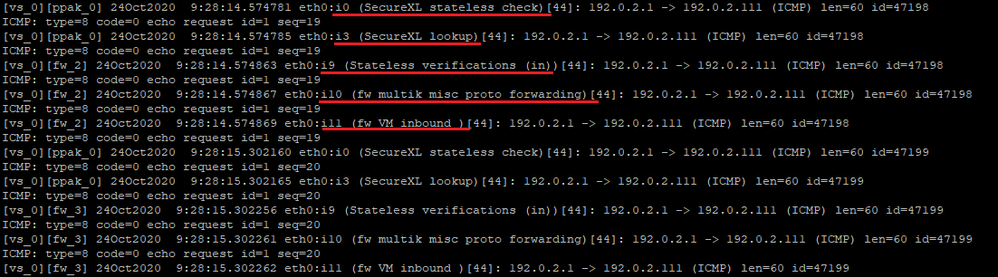
since it is weekend and utilization is low, I was able to use -p all and I was able to get packets from the very beginning of the chain:
[vs_0][ppak_0] eth***.***:i0 (SecureXL stateless check)[44]: *.*.*.* -> **.**.**.** (TCP) len=60 id=32469
TCP: 35344 -> 443 .S.... seq=e4948974 ack=00000000
[vs_0][ppak_0] eth***.***:i3 (SecureXL lookup)[44]: *.*.*.* -> **.**.**.** (TCP) len=60 id=32469
TCP: 35344 -> 443 .S.... seq=e4948974 ack=00000000
...However, in R80.40 CLI Reference Guide, it says: The chain module position parameters "-p{i | I| o | O} ..." parameters do not apply to the accelerated traffic, which is still
monitored at the default inbound and outbound positions.
So, if accelerated traffic is not displayed at chain position 0, are we seeing all packets that came in? Is it possible that SecureXL is processing something (possibly dropping it) without us ever knowing it?
Thank you.
BTW, it was done on R80.20 with JHF take 160.
- Tags:
- fw monitor chain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can't specify a chain position in combination with -F. When using -e you are basically writing inspection code that is inserted as new chain modules into the chain sequence of modules in the F2F path to grab the traffic; in that case you can most definitely specify chain positions. However all the -F option is doing is setting a kernel debug in the SecureXL Implementation Module (sim) to grab packets matching the -F criteria as they go by, whether they are accelerated or not. All inbound traffic must pass through SIM first no matter the processing path (SXL, PSLXL, F2F, etc.) or whether it gets dropped somewhere later, so you should see everything with -F. Unfortunately you don't have the full suite of INSPECT capabilities for what is essentially a kernel debug via -F, which is why the matching criteria is so restrictive with that fw monitor option.
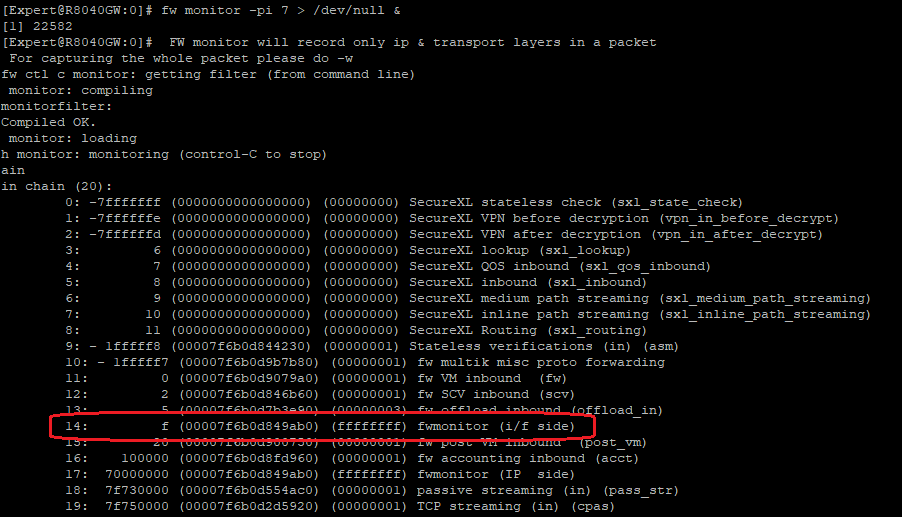
I was initially certain that using fw monitor -p all (DON'T RUN THIS ON A PRODUCTION FIREWALL) would only show traffic in the F2F path, but it looks like that is not the case on R80.40:
So next I tried stepping through with commands fw monitor -pi 1, fw monitor -pi 2, etc. trying to see the earliest point a successful insertion could occur without getting a "no room" message as reported by @Srdjan_B. It seemed to succeed with fw monitor -pi 7 which is still located inside the SecureXL sequences, but in reality it just stuffed the fwmonitor module at the equivalent of "i" (module #14) in the F2F path:
So once again it is not possible to use the INSPECT filters in fw monitor with anything other than -e, and -F with its restrictive syntax must be used if traffic is not F2F. The lone exception seems to be fw monitor -p all (DON'T RUN THIS ON A PRODUCTION FIREWALL) which is somehow getting its hooks into the early SecureXL chain sequences on the Firewall Worker, but there doesn't seem to be any further granularity available for insertion points that early.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please add the -F parameter.
- « Previous
-
- 1
- 2
- Next »
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 26 | |
| 20 | |
| 16 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter