- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- Firewall and Security Management
- :
- Questions on upgrading from R80.10 to R80.40 or R8...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Questions on upgrading from R80.10 to R80.40 or R81
Hi Everyone,
First off, thanks for reading my post and what a great community CheckMates has here. I hope you all are safe and have a Merry Christmas/Happy New Year! I have only been using CheckPoint for about 5 months now, please bear with me while I learn. If this is the wrong area, sorry for posting it in the wrong place!
I was hoping I could get some guidance on upgrading them from R80.10 to R80.40 or R81, with little or no downtime, if possible. If I am not mistaken, I can upgrade the Gateways from R80.10 to R81, but the Smart-1 210 hardware or “SMS” will need a two-step upgrade - R80.40 then R81.
Hardware: (1) Smart-1 210 R80.10 build 031 and (2) 5600 SG R80.10 build 124. SGs are setup as High Availability/ClusterXL.
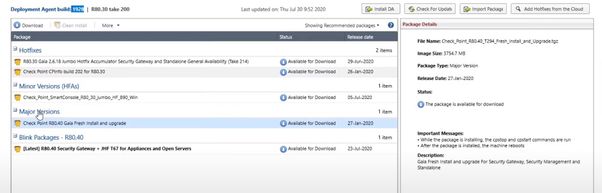
Should I be installing any hotfixes, minor versions, Blink Packages prior? These are what I have currently recommended: Hotfixes - R80.10 Jumbo Hotfix Accumulator General Availability (Take 287), Minor Versions- R80.10 SmartConsole Build 183, Blink Packages – R80.40 Security Management + JHF T89 for Appliances and Open Servers, Major versions (will do this) - R80.40 Gaia Fresh Install and Upgrade.
Here is what I believe the steps should be:
- Backup SMS and the two SGs.
- Verify/Update CPUSE – SMS and Gateways currently on Deployment Agent build 1999 R80.10 take 479. I believe this is latest, so we are good.
- On Smart-1 210/SMS update via Web GUI -> Upgrades (CPUSE) Status and Actions -> Major Versions -> select “R80.40…” Download and assuming Install will be the next option.
- Upgrade SmartConsole on my PC. Download via SMS WebGUI or CheckPoint
- Upgrade Security Gateways using this procedure. I am assuming it’s like #3.
--- I'm reading there are several ways to upgrade, “connectivity upgrade” and “multi-version cluster upgrade”, but then also read from a post that SGs can be updated via SmartConsole on R81. So I'm a bit confused here trying to find out the best method. - Post-upgrade checks (I’ll need to do more research on what else needs to be done here).
I am sure I am missing a lot of things to check or do. Please feel free to add anything you think I should be aware of.
Also if R80.40 is more stable, I'd be fine with at least upgrading to that version.
Thank you,
4 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi r1der,
Please also note that the Smart-1 210 is no longer supported to run R81 software as it's spec is too low
"Note: R81 is not supported on Smart-1 205 and 210"
It may be time to look at something like Smart-1 cloud or a newer appliance to take full advantage of all the latest features
thanks
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes upgrade the DA.
Current is 2019, so download from this one.
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Click "install DA" point to the file and then the deployment agent will be upgraded.
Can be done anytime.
It dosn´t look like you have any packages to download.
Maybe that fixes itself after the DA is updated.
But then you would have new packages to download including major upgrade.
Select the version you want to go to and download it.
Then mark the file and select verify.
After that you can take your snapshot/backup.
Then you can do the upgrade 🙂
Keep in mind that you mgmt station need to support R80.40 GW aswell.
Regards,
Magnus
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a lot, much appriciate!
I'll run this in a LAB environment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi again,
I have just completed the upgrade process successfully in a LAB environment.
the gateways were running R80.10 and I have added some OSPF neighbors.
it turns out that the MVC process document was exactly what I was doing besides adding this command 'set cluster member mvc on' on the upgraded module just before the policy installation.
On my LAB, I could reproduce the OSPF issue but immediately after applying the command, OSPF came up and the cluster got synced.
Cheers!
31 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The link that you providing is to single gateway, make sure to use the cluster procedure. (its the same document just little bit more below)
R80.40 GA with latest GA hotfix is the recommended version.
Regarding upgrading mgmt server, check that you have no locks in sessions etc.
Publish or discard them. Also verify that everything is working correctly before you start.
Meaning that you do get logs, able to push policy etc.
Also write down any special configuration that you have made in files, such as user.def file or similar 🙂
If you would go for R81 mgmt server, i would use the inbuilt new upgrade tool within R81 from the dashboard for gateway upgrade.
Its built on CDT and seams to work really good. have tried a few times now 🙂
Not sure if i would go to R81 for gw just yet.
To view this video, you must Accept and consent to the use of cookies.
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OMG, Magnus! What an honor to get a reply from you. 😁 I've been watching your videos, and watched this one yesterday! Thank you so much for all your videos!
Thanks for pointing out I posted the wrong section. I will update my notes.
It sounds like I can run R81 for SMS and R80.40 on both GWs. Is that correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hehe thank you, there are alot of ppl in the forum that knows there stuff 🙂
Sure you can have R81 mgmt and then run gateways with lower version.
Check this list for ref: https://dl3.checkpoint.com/paid/6d/6df941bffcb69413bff2adb395504eee/CheckPoint_R7x_R8x_R81_BCMaps_Oc...
You will not get all benefits from R81 (such as hit counts on nat rules) as some features requires you to have R81 on the GW aswell.
I normally uses this approach myself as its less impact if there are issues with the mgmt server then the gw.
So on GW i do really try to use a very stable release .
Regards
Magnus
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Magnus,()
Would upgrading from R80.10 to R80.40 be as easy as uploading the R80.40(Check_Point_R80.40_T294_Fresh_Install_and_Upgrade.tgz) file to the Gaia and then rebooting?Our 2200 box died after installing R80.40 using Blink,this time i want to avoid using Blink but cant find any documentation on how to do it the "Standard way".Also during the failed upgrade of 2200,what we found that it wanted to revert back to R77 instead of its existing R80.10 image. Is there any equivalent of cisco "boot flash image= o.s name" for Checkpoint so we can hardcode it so if an new upgrade fails,the box reverts to R80.10 and not to the original factory one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
not sure what you are upgrading for type of things, gateway, mgmt server...
But my generic answer would be.
Make sure that everything works correctly first, meaning receive logs, push policy etc.
- Verify that your box supports the new version. if its an appliance it would be listed in https://www.checkpoint.com/support-services/support-life-cycle-policy/
- Use CPUSE for the upgrade, make sure to upgrade the DA (deployment agent)
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Run the verification on the packet you want to upgrade to.
- Take a snapshot (this would allow you do a easy rollback, (more complicated if VSX) )
Image can be chosen during reboot. including the snapshot.
- After reboot etc is done, update obejct in the smartconsole, install database, push policy
check that you get logs etc.
If you check the release notes there are step by step guide on how to do the upgrades.
I also have a few videos regarding versus upgrades scenario.
In regards to blink, i normally do the normal upgrade first and then add the GA HFA after.
regards,
magnus
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Mangus,
Thanks for your input and apologies,should have clearly stated what we are intending to upgrade.Its a security Gateway.
Looking at what you suggested,the box is back on R80.10 but if i want to use CPUSE instead of Blink,i cant see the "Verifier" option under "More".
If im getting this right,what you are recommending is:
a)Verify the package.
b)Take a snapshot and a backup.(which i already have).
c)Uprade
d)Reboot and Update the object.(have knowledge as i did them in the failed attempt at the upgrade)
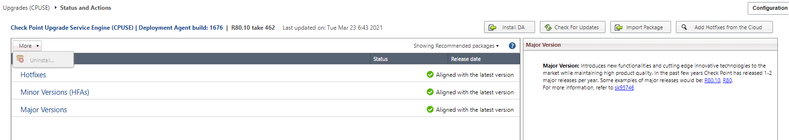
Looking at that we have,do i need to upgrade the DA first?Is build 1676 the reason i cant see the " Verify" under More as its old?
Just FYI,im logged on as Admin.
Thanks for looking into this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes upgrade the DA.
Current is 2019, so download from this one.
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Click "install DA" point to the file and then the deployment agent will be upgraded.
Can be done anytime.
It dosn´t look like you have any packages to download.
Maybe that fixes itself after the DA is updated.
But then you would have new packages to download including major upgrade.
Select the version you want to go to and download it.
Then mark the file and select verify.
After that you can take your snapshot/backup.
Then you can do the upgrade 🙂
Keep in mind that you mgmt station need to support R80.40 GW aswell.
Regards,
Magnus
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have already asked this question in a separate post. Try not to do this again, please.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The tool you're looking for is called ISOmorphic (sk65205). You can use it to completely reimage a device. Feed it the R80.10 ISO image and a USB drive, then boot the firewall from that USB drive. It completely flattens the internal drive and sets the system up to "factory restore" to the version of the ISO you gave it. It then performs the "factory restore" to that version.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi r1der,
Please also note that the Smart-1 210 is no longer supported to run R81 software as it's spec is too low
"Note: R81 is not supported on Smart-1 205 and 210"
It may be time to look at something like Smart-1 cloud or a newer appliance to take full advantage of all the latest features
thanks
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right - Smart-1 210 came in May 2014 and Engineering Support did end last September. It will be supported until September 2022 with R80.40 as the most current version. 5600 from April 2010 will be supported until December 2025 - but a hint: USFW is not enabled on this appliance...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Another option would be to replace the Smart-1 appliance using an Open Server running on VMware ESX, if already present (or maybe Hyper-V, what is supported as well).
and now to something completely different - CCVS, CCAS, CCTE, CCCS, CCSM elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, we'll keep this in mind after upgrade to R80.40 at the very least.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Peter, I completely missed that part! In that case, we will upgrade to R80.40, but are going to start looking into upgrading the appliance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
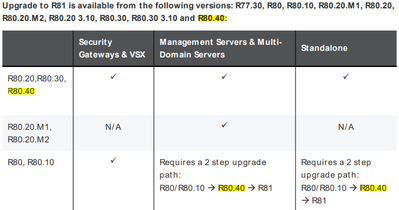
If your goal is R81, it will be a two-step upgrade process (first to R80.40, then R81).
That’s independent of the Smart-1 210 not supporting R81, FYI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @PhoneBoy, thanks for the comment and those webinars you host! I think at this point we will go with R80.40 on gateways and SMS.
Just so I don't feel crazy, and make sure I am reading documentation correctly. I thought this table below states its a direct jump from R80.10 to R81, just not for Management Servers/MDS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think it’s easier if you check this map 🙂
Or use check point upgrade wizard.
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doShowupgradewizard
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The reason Pre-R80.20 management requires a two-step upgrade was we made a fairly significant change in the upgrade infrastructure that was only backported as far as R80.20.
An externally-managed gateway doesn’t have that issue, so it makes sense you can upgrade an R80.10 gateway straight to R81.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed, only the mgmt itself have different upgrade from r80.20 (and therefore two-steps). There is no restriction with gw upgrade
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R1der,
For mgmt, you could consider their cloud managment solution.
Regarding upgrading gateways, I found the Central Deployment Tool (CDT) to be extremely useful. You only have one cluster, so that may be overkill, but using the CDT could still simplify your upgrade after you learn how to use it.
Also, if you're using OSPF, always be mindful that upgrades can cause OSPF to malfunction. One gateway may have the right OSPF routes but the other may not. The quick fix is to reboot the active firewall then the standby. You may see a hiccup of routing. The standby should take the full load and routing.
Regards,
Luis
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you plan to upgrade anyway to R81, notice that after you upgrade the management, the easiest way to upgrade the GWs is using the Smart Console (actions->version upgrade)
If you need assistance please let me know
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the response, everyone :). We have upgraded to R80.40, since the SMART hardware does not support R81.
The process was much more straightforward than I had thought.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's great. Mind to share the steps that you did for sms server and gateway? i currently have 80.10 and plan to upgrade to 80.40...We have a VSX gateways
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry for the late response! For what its worth the process went something like this below. It was a two day process, so we could let GW2 run for a bit to see whether we should update GW1.
- Update SMS from R80.10 to R80.40
- Update GW2 (standby fw)
- Admin Failover to GW2, and update GW1.
- Admin Failover to GW1.
We had zero downtime with this setup.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I am upgrading from R80.10 to R80.40, it's a ClusterXL and I just completed the standby module (5900 appliances). the upgrade went well and it came up with R80.40 but OSPF does not come up on that module. The active module is fine (which still runs R80.10). I can see that OSPF settings are different on R80.40 than R80.10 and I was wondering if this is normal behavior or an issue - on the R80.40 gateway which is the standby I do not see any OSPF neighbors while on the active R80.10 gateway I do...
while both were R80.10 I could see on both OSPF neighbors...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you using the Multi-Version Cluster (MVC) cluster upgrade method that was introduced in R80.40? You need to for your dynamic routing scenario: sk164212: Multi-Version Cluster (MVC) replaces Connectivity Upgrade (CU) in R80.40
New Book: "Max Power 2026" Coming Soon
Check Point Firewall Performance Optimization
Check Point Firewall Performance Optimization
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No... I am not familiar with that, I used CPUSE...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
MVC will sync Dynamic Routing between members. CPUSE is part of the MVC upgrade process, just pick up at the proper step in this list:
New Book: "Max Power 2026" Coming Soon
Check Point Firewall Performance Optimization
Check Point Firewall Performance Optimization
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 38 | |
| 22 | |
| 15 | |
| 10 | |
| 8 | |
| 8 | |
| 6 | |
| 6 | |
| 6 | |
| 6 |
Upcoming Events
Tue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáTue 24 Mar 2026 @ 06:00 PM (COT)
San Pedro Sula: Spark Firewall y AI-Powered Security ManagementAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter