- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Quantum - HyperFlow, Now in EA!
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Quantum - HyperFlow, Now in EA!
We are very excited to share that HyperFlow Early Available program is now open for registration.
In today’s fast changing environment, with a growing demand to address different traffic volumes per connection, HyperFlow is designed to automatically tackle such challenges.
Integrated with additional existing gateway performance features like Dynamic Balancing, HyperFlow allows seamless gateway tuning and optimization in the way we utilize the hardware providing Check Point unprecedented security.
See it in action - Demo & Overview of the new advancements:
HyperFlow EA is mainly for NGTP customers with appliance models of 8 cores and above.
Customer’s benefits:
- Influence – Ability to shape Check Point’s cyber security upcoming products
- Full technical support provided by EA & RnD through the entire process
- Upgrade from EA to GA once available
57 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We need at minimum 8 cores. OK.
What if we have several elephant flows. VMware data replication, NFS connections IBM TSM backups run in parallel in the night. Can we have multiple "Hyper Flow" processes running if we have enough CPUs?
What about support for 64k Scalable Plattform running R80.20SP (or newer) Will this be supported, too?
What about so called "complex protocols" like CIFS, NFS. Is this supported because it was not 2 years ago.
Or perhaps tell us the protocols which are NOT supported by HyperFlow.
Will it work for UDP Streams, too? Like Cisco with their WLAN Tunneling Protocol called CAPWAP which establishes one single connections, based on UDP to ransfer all traffic from one WLAN AP to the other (Foreign Controller, Anchor Controller).
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All good questions Alexander - but please keep in mind this baby step 1.
In my option the solution is only for high end deployments and I would not be surprised if somewhere down the line the NVidia cards will also play a part.
I think Checkpoint have a very long way to go to resolving what I actually feel is a vendor independent challenge; until a solution is available in the lower end devices ie. 4 cores this is somewhat of a DC type resolution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, 8 cores or more. With 4 cores there is not enough CPUs to balance around
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good questions. Let's tag @Chen_Muchtar here 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HyperFlow processes amount is dynamically adjusted according to the load (EF load and overall system load).
HyperFlow will be supported on Cluster, VSX and Maestro platforms starting R81.20. Any demand to support older versions (R80.40 and above) will be evaluated individually.
Protocols:
- NFS is supported.
- CIFS/SMB is currently not supported, but targeted to be in Q2 timeframe for early availability (dev in advanced progress)
- Other known protocols, which are currently not supported are: LDAP, VOIP, SSH/sftp/scp, UDP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
in the Demo we can see a http web traffic via curl with 50MB/s (400 MBit/s) which can be increased up to ~200MB/s (1.600 Mbit/s).
My question is, why is it not possible to reach e.g. 10 Gbit/s in a Single Stream with enough CPU Cores?
I assume that the traffic needs to match specific criteria to get faster transferred with HyperFLow. e.g. Protocol Inspection or other "deep inspection" which then can be offloaded to the different other CPU cores.
What will happen if you run the same download traffic for a rules configured in "fw ctl fast_accel" ? I assume HypeFlow will only improve speed for non-fully-accelerated traffic.
So in other words:
If I run a tcp stream for a backup from src: 10.10.10.10 to 20.20.20.20 using port 80 AND using such a rule
"fw ctl fast_accel add 10.10.10.10/32 20.20.20.20/32 80 6"
Will I have any benefits from HyperFlow in this specific scenario? I assume not because nothing to offload from one CoreXL to another. Everything is done within the SND.
Are there plans to split a TCP stream to different SNDs so fully accelerated traffic can be offloaded? Or is this not possible because SND is pretty close to network card and many things already offloaded to the NIC itself?
Thank you very much for clarification in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fast_accel bypasses certain traffic's medium path and accelerates it through SXL exclusively. You can only do that for 100% trusted traffic. HyperFlow allows medium path inspection but utilises more than a single core for it, hence it can also apply to not so trusted heavy connections.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do not put this security benefit into question. But my internal backup traffic is trusted and I want to compare "fast_accel" with "HyperFlow" only focussing on throughput. So will HyperFlow help me with fully accelerated traffic to speed it up more than without HyperFlow?
Are there plans to use more than one SND for a single connection or is this technically not possible?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The answer is no, HyperFlow will not add any benefit if your traffic is already going though fast_accel. In fact, depending on your multi-queue settings, more than a single SND is involved in forwarding the traffic, on the interfaces sides
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the answer according HyperFlow/fast_accel.
The Multi-Queue answer is not suiteable for my question. I am interested in if there are plans and techniques to split/distribute ONE SINGLE TCP Connection to different SNDs. At the moment a single connection sticks exactly on one SND or on two if two interfaces are used.
So the limit for fast_accel and the limit for HyperFlow in ONE SINGLE connection is still limited by one SND / CPU Core. So to be honest - HyperFlow for Backups - if you already trust it - will not give any benefit. I am repeating the "backup" every time because this is mentioned in the video as a good scenario for HyperFlow.
From my perspective HyperFlow is more useful for daily business where Inspections are active, where users browse the web, or download files which we do not trust.
On the other hand hyperFlow is still no solution for elephant flows which happen in the night - so called backups.
So again, any plans to distribute ONE SINGLE TCP STREAM to different SNDs ? Or technically not possible? THIS would increase throughput for already trusted backups.
PS:
I am ware of lightspeed cards which will solve this issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is an off-topic question here, I am afraid, totally unrelated to HyperFlow and CoreXL. That said, let me check if I could find an answer.
My personal opinion, that would be very problematic to achieve though. SecureXL code is minimalistic, and any parallel processing requires a load-balanced of sorts to form the correct sequence of operations. SND has this functionality for FWKs, but putting another dispatching instance inside SND population seems very hard to do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The intention of HyperFlow was to solve the issue with Elephant Flows. Elephant Flows are trusted, high volume, high throughput traffic inside DataCenters. Like Backups.
But HyperFlow will not address this problem. It will not improve these trusted, high volume, high throughput sessions in the night.
Improving trusted, high volume, high throughput traffic in the night like backups the only solution CheckPoint can offer is Lightspeed Cards with its known limitations. HyperFlow does not address this issue even if marketing wants to belive us that it will.
Sorry to say that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Alexander_Wilke I think you are getting upset here and jumping to incorrect conclusions, so let's start from the beginning.
HyperFlow is designed to resolve an obvious bottleneck with Heavy Connections going through Medium Path.
This is how we define "Heavy Connections" (Quoting from sk164215😞
Heavy connection flow system definition:
- Specific instance CPU is over 60%
- Suspected connection lasts more than 5 seconds
- Suspected connection utilizes more than 50% of the total work the instance does
- In other words, connection CPU utilization must be > 30%
Mind by "instance" SK talks about FWK instance. Fully accelerated connections, as in your case, are something else completely. We have never said HyperFlow would address performance for 100% accelerated flows.
Hence your statement "HyperFlow does not address this issue even if marketing wants to believe us that it will" is... well... inaccurate. If indeed someone else tried to state that, please provide me with more details in a private message, so we could address this internally, to avoid any misunderstandings in the future.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In terms of "available" in r81.20 are we still talking 8 core's minimum?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@skandshus Yes, it does not make sense when you have less than 8
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is Hyperflow supported on open hardware or VMWare with at least 8 cores? Based on my lab work with R81.20 in VWWare it appears the answer is no.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, only CP appliances
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Chen_Muchtar a few questions:
Zero Phishing is shown as being boosted by Hyperflow (along with IPS/AV/ABOT) in SK178070 but nowhere else I can find including here at CheckMates, is that really correct? If so what specific ZPH operation is boosted? PM, MD5?
Threat Emulation & Threat Extraction are not boosted by Hyperflow, but connections subject to TE/TX inspection will not stop boosting from occurring for the other supported blades, correct?
Does use of any blades other than Content Awareness and DLP block boosting?
Are the Dynamic Dispatcher and Priority Queues required to be enabled for Hyperflow to boost? I would assume at least the latter would be required for the Evaluator/Eviluator elephant flow identifier to trigger boosting.
Can Lightspeed and Hyperflow be used together on the same system? Not completely sure here but it looks like Lightspeed requires UPPAK (usim) but Hyperflow requires KPPAK (sim)? Thanks!
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Regarding Zero Phishing, Threat Emulation & Threat Extractions:
Small correction (also updated in the SK), Threat Emulation & Threat Extraction, can be boosted by HyperFlow, since they require the MD5 result of files, Zero Phishing on the other hand, does not need it, and hence is not being boosted, nevertheless, connections subject to it, will not stop boosting from occurring for the other supported blades.
Regarding Content Awareness and DLP:
It may be more precise to say, that they potentially decrease the boost, rather than blocking it, the reason is that these blades add more synchronous work to the FW instance, which results in a smaller portion of the work that can be sent to HyperFlow. We are currently not aware of other such blades.
Regarding Dynamic Dispatcher and Priority Queues:
Dynamic Dispatcher is required for Dynamic Balancing to be enabled, and Dynamic Balancing is required for HyperFlow to be enabled.
Disabling Priority Queues does not affect the Evaluator/Eviluator, so it will continue to work regardless.
Regarding Lightspeed and HyperFlow:
Lightspeed is currently supported on R81.10 JHF, while HyperFlow on R81.20.
On R82, and future R81.20 JHF, yes, they will be able to operate together on the same system.
Is there a specific place implying that HyperFlow requires KPPAK? We would want to change it if so.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Chen_Muchtar that answered all my questions exactly!
As far as KPPAK being required for Hyperflow I saw that in the thread below, but reading through the response again it is unclear to me now what Amit is referring to.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What I meant there, is that currently Dynamic Balancing is not supported in UPPAK/LS in R81.10 JHF, it will be supported in R82 and future R81.20 or R81.10 JHF.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is Hyperflow supported on Cloud Guard instances or is this just a Check Point appliance only feature?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not supported at this time, please refer sk178070.
If we're talking Quantum series appliance then it is 6700 and higher.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sort of a related question @Chen_Muchtar: Is there any user-tunable way to increase the 24 hour period of heavy connections reported by fw ctl multik print_heavy_conn? I poked around in the config of CPdiag but didn't see anything.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Will Hyper Flow enable itself automatically on an R81.10 or R81.20 Maestro gateway? If so, how can I tell if it's enabled?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HyperFlow is only supported starting R81.20.
It should be automatically enabled, if the conditions allow (e.g. UserSpace FW).
You can check if it is enabled via CPView -> HyperFlow (if the tab exists), or by running the command "connection_pipelining status".
You can refer to sk178070 for more details.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you. The reason I asked is I'm slightly concerned with the issue discussed here: R81.20 T26 - Traffic disruption during policy inst... - Check Point CheckMates. The issue is fixed in Jumbo Hotfix Take 54, but Take 54 isn't recommended yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
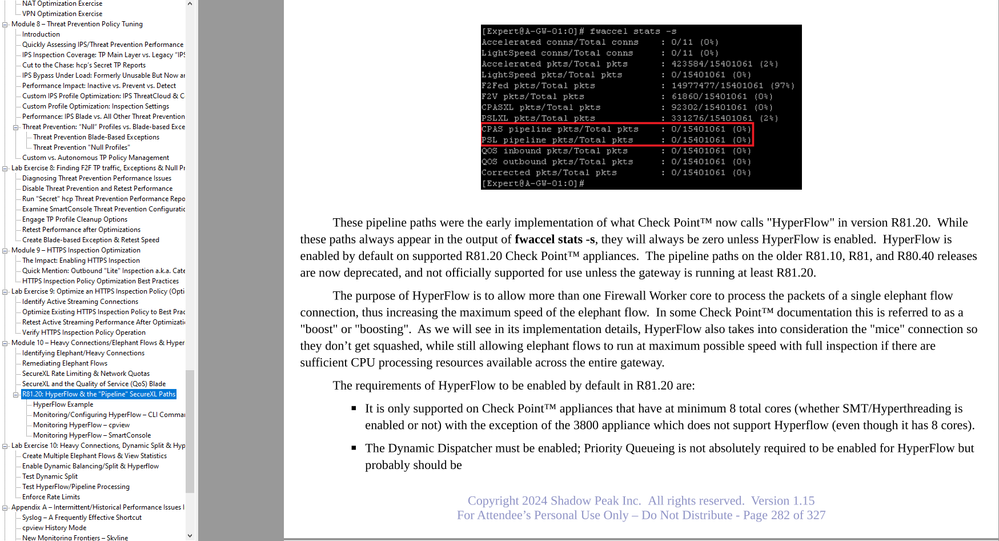
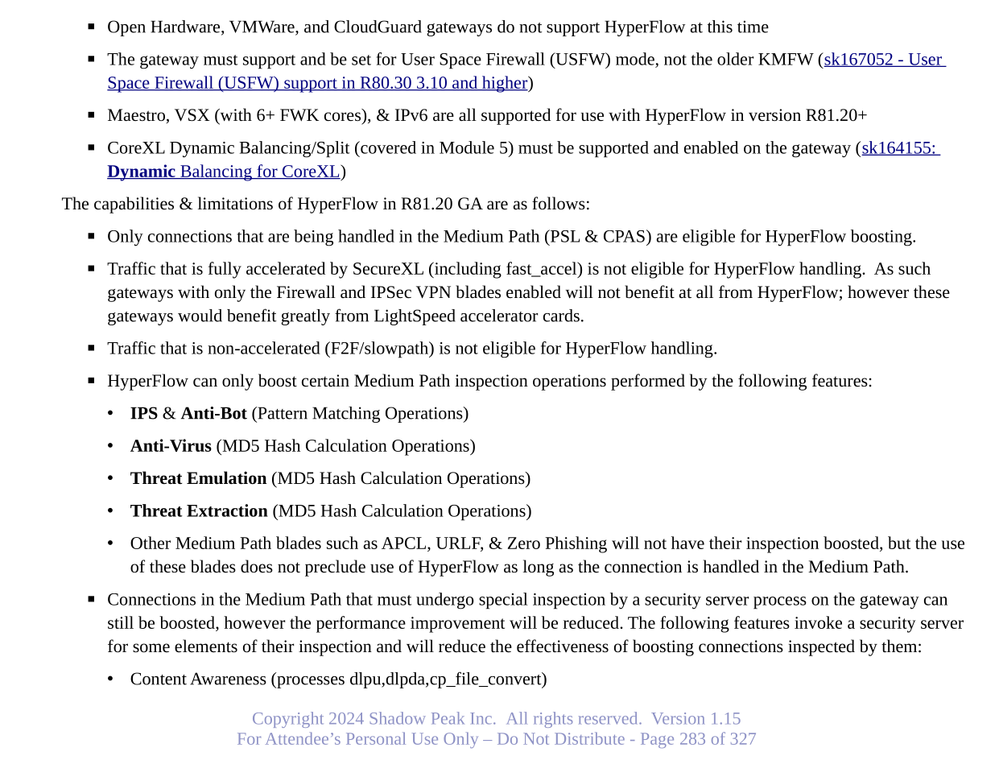
Hyperflow will be enabled by default on systems that support it, are running R81.20, and have met some other requirements. Here is the list of requirements taken from my Gateway Performance Optimization Course, where we work with Hyperflow in the labs; this course is offered monthly (next one is April 24-25, 2024):
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- « Previous
-
- 1
- 2
- Next »
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 9 | |
| 8 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter