- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Phase 2 Site-to-site VPN error
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Phase 2 Site-to-site VPN error
Hello
I have a Site-to-site VPN configured between checkpoint and cisco ASA.
When I check through SmartView Monitor, I see that my tunnel is up.
But when I start communication, the first phase goes well, but on the second phase I receive a message
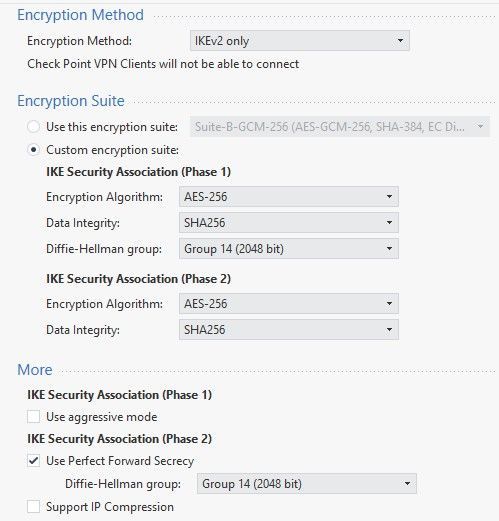
Child SA exchange: Received notification from peer: No proposal chosen MyMethods Phase2: AES-256 + HMAC-SHA2-256, No IPComp, No ESN, Group 14
Please tell me what this means.
Because on my part exactly the same parameters are set.
Thank you!
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The cisco engineer found the solution, an odd one. TAC is reviewing this but unchecking this specific config to sent VTI ip address to the peers fixed it.
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Log message and the screenshot you posted here both shows us the configuration on Check Point side.
You have to compare it with the configuration on Cisco side.
Either ask the Cisco admin on the other side what is configured there or better check it yourself by checking the debug logs.
If you can force the Cisco side to initiate the connection, the debug logs on Check Point side will show you what the ASA is trying to do:
- Start debug on Expert Shell: # vpn debug trunc
- Let's the Cisco side initiate the tunnel (verify in Check Point Log that they really did try it).
- Stop debug on Expert Shell: # vpn debug off; vpn debug ikeoff
- Look at $FWDIR/log/ikev2.xmll with IKEView
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
When you mention that reading “start the connection” once you have placed the debug commands, this way for the peer to start the connection, can it be through a VPN restart from your FW?
I assume so, or am I mistaken?
Or does starting a connection refer only to traffic from Phase 2 selectors?
In a VSX, where is the debug result hosted? Is it kept in the same path as a traditional FW?
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like @Tobias_Moritz has already mentioned. This points to the proposal on phase 2 to not be equal on the Check Point side as on the CISCO side.
We know from the logs that Check Point is proposing:
AES-256 + HMAC-SHA2-256, PFS Group 14.
We don't know what the CISCO firewall on the other end has configured for phase 2. There seems to be a mismatch here.
By doing the debug that @Tobias_Moritz suggested you will most likely see whatever the CISCO is trying to use for its phase 2 negotiating and you will most likely see that something is off and you will have to correct it so both sides are on terms when it comes to whatever settings are being used for phase 2.
If you are communicating with whoever is controlling the CISCO firewall you could always ask them for details on what they have configured for phase 2 / IP-sec encryption. Might it be that they are not using PFS? Might they be using different algorithms?
Certifications: CCSA, CCSE, CCSM, CCSM ELITE, CCTA, CCTE, CCVS, CCME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have the same issue, it's been solved? And if so how?
I know it's old post but i'm ensure the same issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You should start a new thread with all of your details so we can provide better context. No proposal chosen is generally both sides are not agreeing on the same security ciphers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No Proposal chosen means that both GWs cannot agree on the Phase 2 encryption algorithm and hence cannot set a symmetric key. It usually means that the Phase 2 settings list different algorithms.
However, I agree with a suggestion to open a different thread for your specific issue, so we could dig into the root cause properly in an independent discussion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm having a similar issue and it's Turning out the cisco is proposing several groups, 21, 20, and 14. That being said JHF99 was handling that ok, JHF118 is not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Really? Never heard of that before...Cisco asa or something else?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
3120, we are hobbling along though we just re-negotiate every 2 minutes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know every time I dealt with Cisco TAC, they would always change those settings via ssh, never ASDM. Not sure if there is something in newer versions thats different, but when I dealt with Cisco VPNs 7-8 years ago, I never encountered that problem.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The cisco engineer found the solution, an odd one. TAC is reviewing this but unchecking this specific config to sent VTI ip address to the peers fixed it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great!
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 17 | |
| 11 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter