- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Notify when certificate expired
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Notify when certificate expired
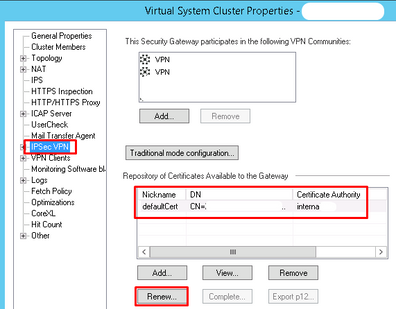
Yesterday I had an incident with my IPSEC tunnels with branches (they are established by certificate) because the virtual firewall certificate expired.
Attached the image of the Gw, had to renew the certificate to restore the service
The question is: The Firewall can send a notification warning that a certificate is about to expire?, ¿What configuration is required for the Firewall could send the notification?
thanks for your help
3 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
...and sk31539 tells us that
The Security Management server generates a report, per Security Gateway, warning about those certificates that will expire within 60 days time from the current date. This functionality is always enabled and the 60 days is a fixed warning period.
...
- Certificate expiration warning messages are not recorded in any log by the Security Management server.
- Warnings are generated and presented anew with each Policy installation.
You could check on CLI using sk104400:
# cpca_client lscert -stat Valid -kind IKE
Operation succeeded. rc=0.
1 certs found.
Subject = CN=cpmodule VPN Certificate,O=Example_Management_Server.checkpoint.com.d2hitj
Status = Valid Kind = IKE Serial = 91912 DP = 1
Not_Before: Wed Jan 14 14:19:02 2015 Not_After: Tue Jan 14 14:19:02 2020
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @raquinog , @Peter_Baumann , @Anthony_Vita
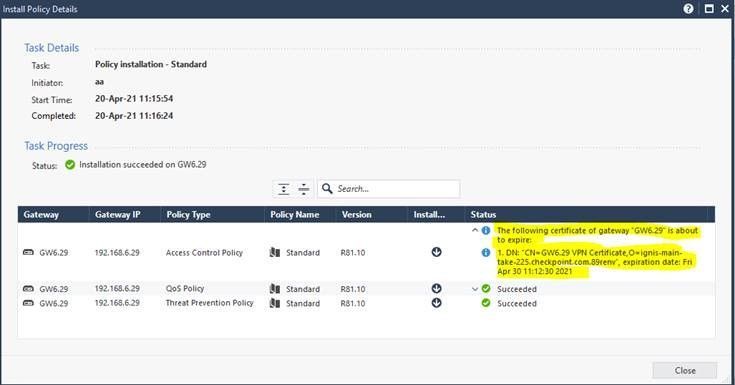
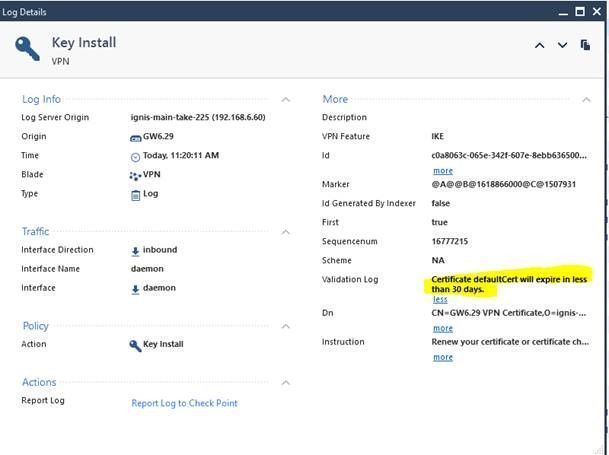
Nowadays the firewall is sending notification that a certificate is about to expire in two places
1. 'info' status as part of policy installation:
2. In VPN log:
As @G_W_Albrecht mentioned, You can also monitor VPN certificates of all Virtual systems / Security gateways from Security Management via single CLI command:
cpca_client search "VPN certificate"
We are about to Improve the alert during Policy installation – to Changing from ‘info’ to ‘warning‘
The improvement will be released in R81.20 and also be ported to all R8X.XX JHFs
We are looking for other ways to alert about VPN certificate expiry, such as red “X” for the Gateway object when the VPN certificate is expired / Yellow Warning sign when the certificate is about to expire soon (e.g 60 days or less)
Thanks,
Matan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I made this simple script for crontab. It may be usefull for you
#!/bin/sh
source /etc/profile.d/CP.sh
CERTIFICATE=`cpca_client lscert -stat Valid -dn <SubString>`
#get string with expiration date from certificate info
CERT_INFO=`cpca_client lscert -stat Valid -dn <SubString> | grep Not_After`
#make list with expiration date, month and year
EXPIRED=$(python -c "lst='$CERT_INFO'.split('Not_After:'); print(lst[1].split())")
#get expiration day
EXPIRED_DATE=$( python -c "print($EXPIRED[2])" )
#get expiration month
EXPIRED_MONTH=$( python -c "print($EXPIRED[1])" )
#get expiration year
EXPIRED_YEAR=$( python -c "print($EXPIRED[-1])" )
DIFF=$(python -c "from datetime import (date, datetime); print date(2023, datetime.strptime('$EXPIRED_MONTH','%b').month, 11).toordinal() - date.today().toordinal()")
if [ $DIFF -lt 30 ];
then
echo -e "Subject: CheckPoint VPN certificate expiration\r\n\r\nVPN certificate will be expired in $DIFF days.\r\n\n\n $CERTIFICATE.\r\n " | sendmail --domain=<domain name> -f <from_email> -v <to_email> --host=<smtp_server>
fi
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Acording to SK102092, gateway does not alert about certificates expiration without installing a Security policy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
...and sk31539 tells us that
The Security Management server generates a report, per Security Gateway, warning about those certificates that will expire within 60 days time from the current date. This functionality is always enabled and the 60 days is a fixed warning period.
...
- Certificate expiration warning messages are not recorded in any log by the Security Management server.
- Warnings are generated and presented anew with each Policy installation.
You could check on CLI using sk104400:
# cpca_client lscert -stat Valid -kind IKE
Operation succeeded. rc=0.
1 certs found.
Subject = CN=cpmodule VPN Certificate,O=Example_Management_Server.checkpoint.com.d2hitj
Status = Valid Kind = IKE Serial = 91912 DP = 1
Not_Before: Wed Jan 14 14:19:02 2015 Not_After: Tue Jan 14 14:19:02 2020
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is an interesting topic on CheckMates with a lot of valuable information about this: Third Parties Certificate details
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @raquinog ,
A customer of us had the same problem, no indication when instaling the policy about the expired certificate.
The feature should be always activated but it seems that it is not working.
Nobody knows why, so we will open a case for it.
Thanks,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just had the same issue. We're you able to figure out why the feature doesn't work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Anthony_Vita ,
We opened a case and there was a lot of troubleshooting involved. Unfortunately it leads not to a solution and was closed by check point/customer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @raquinog , @Peter_Baumann , @Anthony_Vita
Nowadays the firewall is sending notification that a certificate is about to expire in two places
1. 'info' status as part of policy installation:
2. In VPN log:
As @G_W_Albrecht mentioned, You can also monitor VPN certificates of all Virtual systems / Security gateways from Security Management via single CLI command:
cpca_client search "VPN certificate"
We are about to Improve the alert during Policy installation – to Changing from ‘info’ to ‘warning‘
The improvement will be released in R81.20 and also be ported to all R8X.XX JHFs
We are looking for other ways to alert about VPN certificate expiry, such as red “X” for the Gateway object when the VPN certificate is expired / Yellow Warning sign when the certificate is about to expire soon (e.g 60 days or less)
Thanks,
Matan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry to resurrect such an old post but we are running R81.10 mgmt/gateway, which I see in the screenshots, and I'm not seeing any of these expiring cert messages in my logs on the key installs. We should have some recently because we had a VPN cert expire this weekend which went un-noticed. I'd like to incorporate these logs into an alerting mechanism in our SIEM.
Do you know when this became available or did this get pushed to R81.20?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Heath
Sorry for the inconvenient.
By checking the code, it seems that the log exist at least since R80.30.
In case you can't find it, you may open a ticket to Check Point support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I made this simple script for crontab. It may be usefull for you
#!/bin/sh
source /etc/profile.d/CP.sh
CERTIFICATE=`cpca_client lscert -stat Valid -dn <SubString>`
#get string with expiration date from certificate info
CERT_INFO=`cpca_client lscert -stat Valid -dn <SubString> | grep Not_After`
#make list with expiration date, month and year
EXPIRED=$(python -c "lst='$CERT_INFO'.split('Not_After:'); print(lst[1].split())")
#get expiration day
EXPIRED_DATE=$( python -c "print($EXPIRED[2])" )
#get expiration month
EXPIRED_MONTH=$( python -c "print($EXPIRED[1])" )
#get expiration year
EXPIRED_YEAR=$( python -c "print($EXPIRED[-1])" )
DIFF=$(python -c "from datetime import (date, datetime); print date(2023, datetime.strptime('$EXPIRED_MONTH','%b').month, 11).toordinal() - date.today().toordinal()")
if [ $DIFF -lt 30 ];
then
echo -e "Subject: CheckPoint VPN certificate expiration\r\n\r\nVPN certificate will be expired in $DIFF days.\r\n\n\n $CERTIFICATE.\r\n " | sendmail --domain=<domain name> -f <from_email> -v <to_email> --host=<smtp_server>
fi
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 8 | |
| 8 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter