- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Introduction to Lakera:
Securing the AI Frontier!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Not substituted certificate in browser Https I...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Not substituted certificate in browser Https Inspection
Hello everyone!
I have Gaia R80.40 distributed deployment (management + clusterXL). I trying enable Https inspection the other day, created self-signed certificate, install this in "trusted root authorities" in Windows machine, but when i open any https site, certificate not substituted in browser.
Please tell me why this can happen?
With Regards, Herman
- Tags:
- https inspection
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just a quick update.
Mohammad and I did remote session, ended up changing below as per settings I pointed out and I also had him create another ordered layer with urlf + appc blades enabled, we blocked social networking category and after this, facebook showed blocked with right block page. We also added all 3 certs in trusted root (https cert, mgmt one and gw cert), so does not show cert warnings.
Andy
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Wolfgang
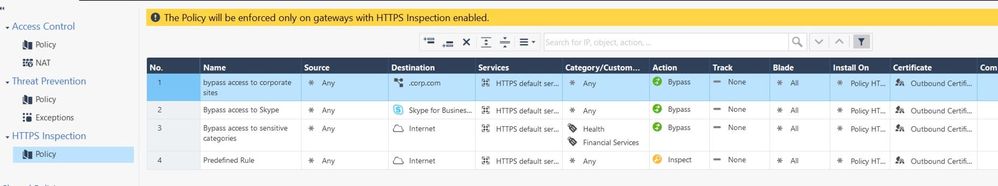
only default predefined rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you install the policy after enabling HTTPS Inspection in the FW object? 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
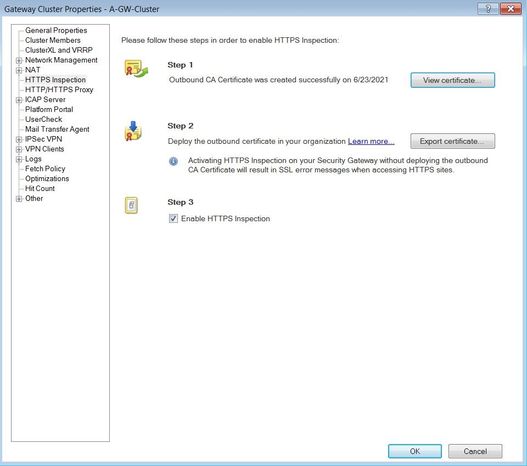
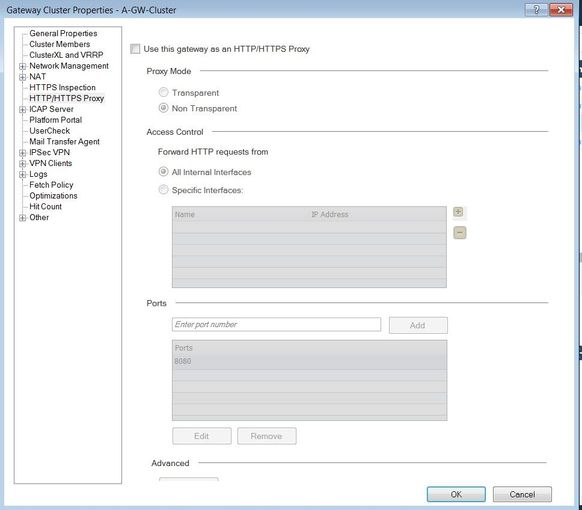
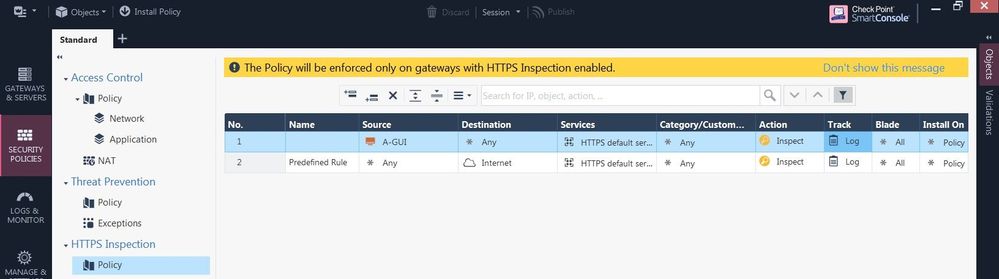
I'm new in checkpoint environment 😁, but if you mean it (see screenshot) then yes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you use the gateway as a proxy or transparent proxy? Is the gateway inline en route to the internet? I think the object "Internet" is based on the topology, is your topology correct (edit cluster -> network management -> the interface leading to the WAN should be marked as external) ?
You can set your ssl inspect rule to "log" and create another rule like this below it "Source: any Destination:any Service:any Action:bypass Track:log".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No proxy not used, if i right you understand
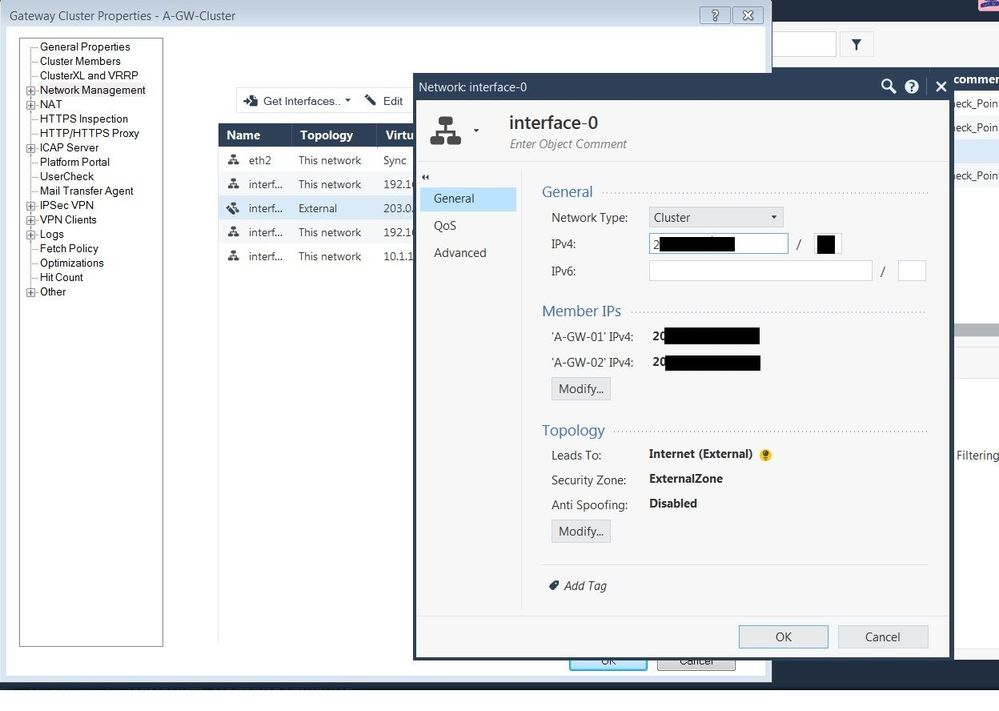
Yes, gateway inline en route to the internet. Checked Network topology, and External interface set as External zone (it's has not been mark as External zone), install policy, but it's did not affect
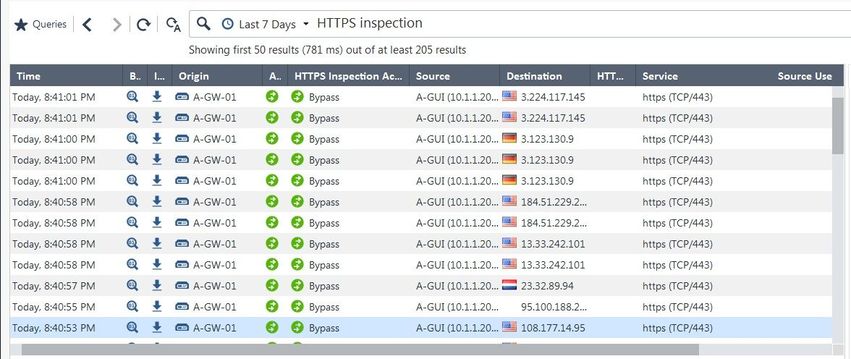
Not sure that right understand, but create bypass "test rule" and enable log tracking:
And now in logs & monitor tab if set filter as HTTPS Inspection may be view this:
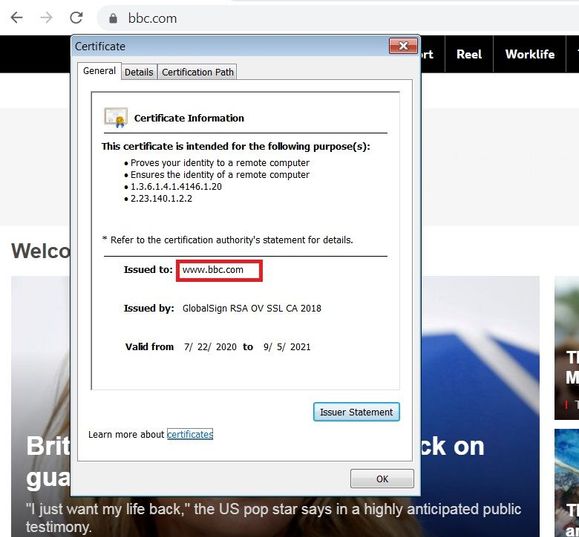
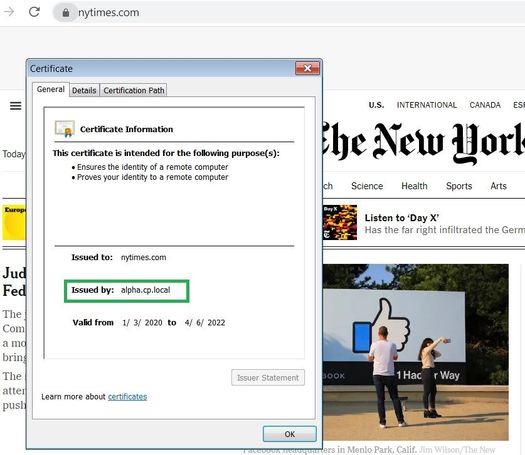
But unfortunately certificate not substituted after that
--------
PS English is not my native language, so please be kind to my mistakes )))
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You might wanna redact the public IPs next time and don't worry about your english 🙂 Your Interface names look strange to me, do they match the names as configured on the gateway OS? Can you switch the HTTPS Inspection rules around?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
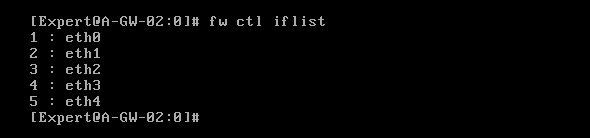
In gateway OS interface have this names, they don't match with names in SmartConsole:
With inspections rules, i try some experiments
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This looks good. HTTPS inspection catches the traffic, but it‘s bypassed regarding your rule. Something with defining the „internet“ as destination in your second rule does work like you want. Have a look at @Danny great post Properly defining the Internet within a security policy
You can try to define another rule first with your client as source and destination any with action „inspect“ to see if this connection will be intercepted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
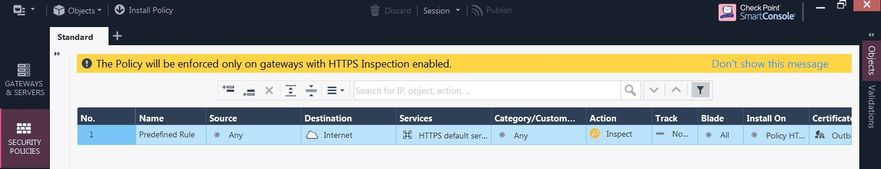
I'm try to define first rule with destination any instead "Internet" for my client machine, but in logs not showing record with "inspect" action for Https inspection. Of course 😀 after create rule and install policy, tried to open some https sites in Chrome
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By the way, your last rule in the HTTPS Inspection policy should be any any bypass.
Without that, you very likely will have performance issues
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's another topic but to me in newer versions of the Smart Console it should be the default behaviour with a warning message if it doesn't exist, similar to the message if an inline layer is missing a cleanup rule. It doesn't make sense to have Tech Talks explaining that it's best practices to have any/any/bypass to prevent performance issues due to undefined sessions and have the system out of the box doing the exact opposite, causing issues to unsuspecting customers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agree cold heartedly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know this may sound like a silly question, but did you make sure that windows machine is actually going through CP firewall? If you do tcpdump -nni host x.x.x.x (with x.x.x.x as windows machine IP address), what do you see? Have you tried another machine or just one? From screenshots you pasted, config looks okay to me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello everyone!
I fixed this, just add new layer with Application & URL filtering blade in Access Control Policy. Than added three rules and it's work fine
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have tried all of this stuff but I still cannot figure out by the https inspection is not inspecting. it shows bypassing logs but no inspection logs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
See if my post below helps, if not, we can do remote. I have perfectly working ssl inspection lab.
Andy
https://community.checkpoint.com/t5/Security-Gateways/Https-inspection-tip/m-p/219139
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi Andy, Thank you very much for you help. yes a remote session would be very helpful. here is what I did to configure https inspection and let me know if there something that I missed :
I tried in my lab it does not seem to "inspect" traffic. when I set the https policy to inspect I do not see any logs of inspection but when I set it to bypass I see the logs of bypassing.
1. I enbaled application and url filtering blade
2. enabled https inspection. created the certificate and exported it and isntalled it on the client machine. I checked the browser certificate repository to make sure taht the certificate was installed and it was.
3. enabled the application and url filtering on the access policy
4. set the https policy to any any inspect and log
5. installed access policy
when I visit https website and I try to check the logs to see the inspection, I don't see anything. and on the browser when I click to which certificate is being used I don't see the one that I created.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just came back from long bike ride, saw your update 🙂
Anyway, since Im on call with work for this and next weekend, I usually do some labs on Sundays anyway, so let me know, happy to do remote and help you.
Just message me directly, we can do zoom. I have my private gmail one, as my company uses teams, but its good for 40 mins and if we need another one, we just wait 10 mins and "fire up" next session.
Let me know.
Best,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the remote session Andy that was very helpful as you have managed to find the solution.
as I may believe the solution was to create another layer with application and url filtering enabled but you also mentioned that such could be accomplished on the same layer but its perefable to do it on another layer. and also to have the "fail mode" on "fail close block all requests"
thank you very luch again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Its pleasure to help man, any time. Now, I will go eat some "home made" Mcdonalds fries 🤣🤣
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just a quick update.
Mohammad and I did remote session, ended up changing below as per settings I pointed out and I also had him create another ordered layer with urlf + appc blades enabled, we blocked social networking category and after this, facebook showed blocked with right block page. We also added all 3 certs in trusted root (https cert, mgmt one and gw cert), so does not show cert warnings.
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 12 | |
| 8 | |
| 7 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Wed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter