- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Necessity of using HTTPS Inspection
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Necessity of using HTTPS Inspection
Hello, team.
One question,
Is it really necessary to use HTTPs Inspection, when I activate the APPC+URLF+Content Awareness blades?
My question is based on the fact that I only have these blades active now, and I am "exploiting" the virtues of APPC+URLF basically, but for some reason, the traffic does not "behave" as we want.
For example, we have created a rule to block the page cnn.com, this we have done with a "Custom Application/Site", where we put the domain like this:
*.cnn.com*
But for some reason, the Firewall, does not block the page, and continues to allow it.
Other particular pages have the same behavior (they should be blocked, and they are not blocked).
That's where I wonder "why" this is happening.
Is it a problem of the blades?
Is HTTPS Inspection really necessary here?
Can someone clarify the doubt, please.
Regards
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bro, this was already answered many times before ; - )
No, its NOT mandatory, but additional filtering/inspection wont be performed through TP blades. Now, here is the thing. As fas as blocking pages, they should be blocked, but you would never see the actual block page as https inspection is not enabled, so user may see page is reset or page cant be displayed error. I actually verified this in my lab many times.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Then,
To be us (as administrators) 100% sure that the pages are being blocked, based on our created rules, is it necessary to enable the HTTPS Inspection, and install this certificate on the PCs of the users of our network?
Indeed, based on your comment, the pages are still showing as allowed, and from time to time, we observe that the page "refreshes" itself, and leaves us many doubts. LOL
Cheers 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, thats right, for pages to be blocked PROPERLY, you need https inspection.
Btw, IF inspection is off, pages should still be inaccessible(thats if url filtering is blocking right categories), so you may need to look into that why they are allowed.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Friend,
Does it offer any advantage, to block domains of web pages, using "DOMAIN" objects, instead of using "Custom Applications/Sites"?
I understand according to the theory, that the DOMAIN object, pulls up to 10 subdomains, and only depends on the Firewall blade, right?
I can in any case, migrate a rule, to stop using DOMAIN object, and use the "CUSTOM APPLICATION/SITE" (which I understand, works with the APPC+URLF blades).
Is it feasible to perform this practice?
Cheers 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, not sure I understand what you mean, apologies. blade has absolutely nothing to do with domain/custom site difference, but everything to do how traffic is inspected.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I guess I didn't know how to explain.
We have a website which is: *.gob.pe
This website, currently, the client has it working on a firewall rule, but using FQDN (Object Domain), and I wonder, if using it this way, offers 100% efficiency, to control the access of users to this particular domain?
Or in your experience, would you rather use the Custom Application/Site to be able to "leverage" the APPC+URLF blades that are already enabled in the Firewall.
I hope now my doubt is clearer. 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you send a screenshot of how you have it configured? Personally, I ALWAYS use custom app group, find it works 100% of the time.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
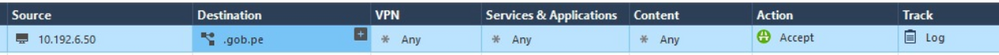
It is something like this.
This GW, has already enabled the APPC+URLF blades.
So, I think it would be better to start using the "Custom Application/Site" option, right?
Because as the rule stands, the page (main domain and subdomains) that involve ".gob.pe", are still blocked, and what we are looking for, is to "allow" the consumption of those pages.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That works, but I ONLY use that if I know fqdn, then its fine, otherwise, I stick with custom site. Makes sense?
Either way, you got it bro 🙂
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I spent some time earlier this year figuring out the right way to build the matching expressions for Custom Application/Site objects. You may find the results useful.
HTTPS Inspection is absolutely needed for deep inspection like IPS. The firewall can't inspect what it can't see. TLSv1.3 also adds the ability to negotiate anonymous encryption before authenticating the site, so you may need HTTPS Inspection to be able to filter TLSv1.3 traffic with URL Filtering.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Super helpful @Bob_Zimmerman 🙌
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 23 | |
| 17 | |
| 11 | |
| 8 | |
| 7 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter