- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Monitoring of Anti-Spoofing traffic
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Monitoring of Anti-Spoofing traffic
Hello guys,
Is there any way how to monitor anti-spoofing traffic in R77.30 ? I know that I can choose Alert, Log or None in spoofing properties for specific interface. But does someone know how to send for example syslog event in case gateway recognize spoofing traffic ? Or send mail ...
Searching all logs to found "spoofing" word in Information isnt good approach... There must be something on CLI how to check if interface faced spoofing traffic (as it issue log event towards log server).
Thanks for every suggestion in advance.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Tags:
- spoofing
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One place you can see anti-spoofing drop packets (albeit not on a specific interface) is cpview.

If you want Alerts to run a script, you can set that in Global Properties (but will apply for anything with Log type set to Alert):
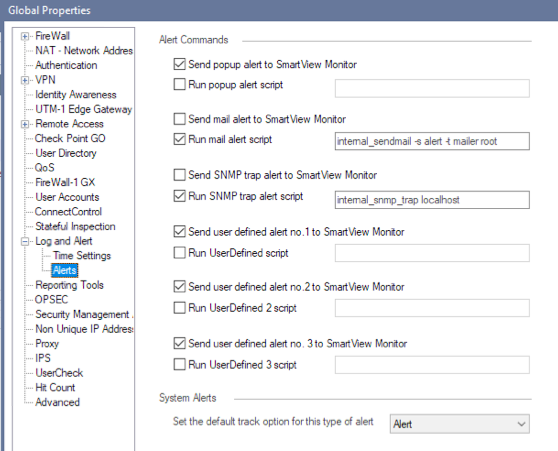
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, I will check that.
What is default path of that UserDefined script? Or can I use full path of script, like: /var/tmp/testing.sh ?
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can use full path.
Offhand I am not sure what the default path is for this screen.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was not managed to get it work ![]()
First, I want to test it via specific rule, so I have created new rule with Track: "Alert". My understanding is that the script located in /var/log/test.sh should be executed every time this specific rule is matched.
My settings in Global Properties:

According logs, the specific traffic is matched and I also see Alert in logs. The only problem is that it didnt activate the script.
I also tried to set Track as "UserDefined" and with this setup, the script was executed.
Is there any way how to do the same just for Alert (as in Anti-spoofing in R77.30 there are only following options available):

Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As far as I know both of these things should operate exactly the same.
I would open a TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Isnt some stats included in $FWDIR/state/local/FW1/local.set ? How cpview (SecureXL) knows how many packets were dropped because of anti-spoofing ?
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Look into sk56701, there are some ideas how to make it work. The fact script is not working means there is something wrong with it. Most probably variables.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Valeri,
The script is working in case I choose "UserDefined" in Track option for the particular rule.
In case I want to do the same for "Alert", it will not work.
My script looks like:

My rule looks like (it will not execute script):

This rule will execute the script:

And my Alert settings looks like:

Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That must be true. "Run popup alert script" means the binary is under $FWDIR/bin. If it is not, it is qualified as a "User defined alert"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dameon Welch Abernathy Valeri Loukine issue solved with following configuration of Alerts in Global Properties:
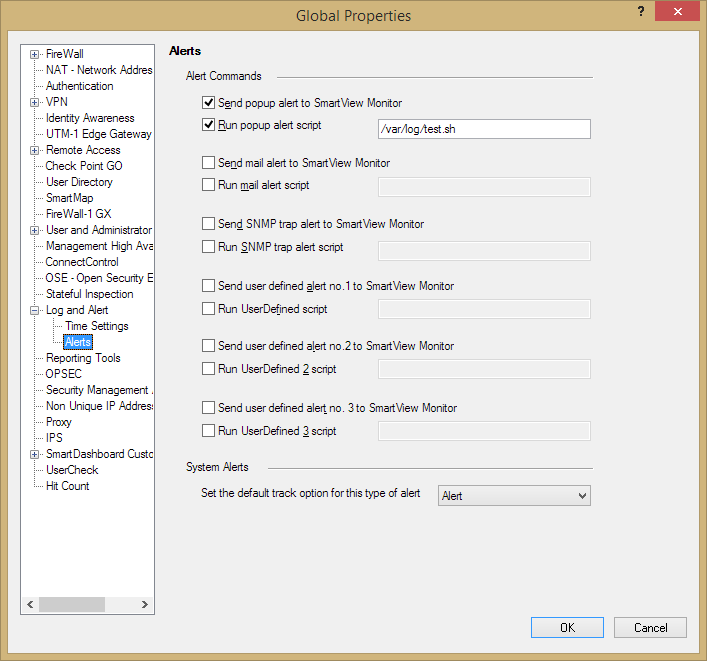
So now my final question is:
How can I simulate Address Spoofing for interface eth1.50 with subnet 10.20.30.0/24 to see if this is really working in case I will select Alert in Anti-Spoofing Tracking option ?
NOTE: I am running internal LAB in VMware, so I can do (almost) everything ![]()
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Create a VM with the desired address and try to ping "through" the firewall?
You'll probably have to muck with the routing/ARP tables to make it work right.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
easy, configure anti-spoofing manually and exclude some parts of your network attached to this interface. Link, instead of /24 do less than that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Jozko,
Was you able to perform this. Even I want to perform anti spoofing lab in vmware. Don't know howto do it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, I was not able to simulate antispoofing traffic 😕
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 18 | |
| 11 | |
| 8 | |
| 7 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


