- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Many TCP First-Packet-isn't-SYN drops after u...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Many TCP First-Packet-isn't-SYN drops after upgrade to R81.10
Hi,
After upgrading from R80.20 to R81.10 we see many many TCP drops in the logs from many servers.
Drops are First Packet Isn't SYN with TCP flags are mostly FIN-ACK, ACK.
No performance or other issue with these servers.
We've never had these drops on R80.20 from these servers, and we haven't changed any topology when upgraded.
I suspect it's just cosmetic or a new logging feature issue, but not sure...
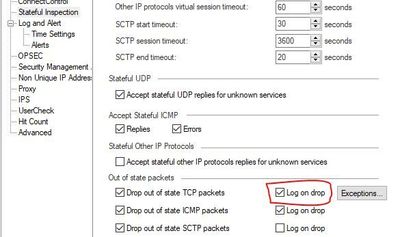
I've noticed a checkbox under Global Properties -> Stateful Inspection -> "Log on drop". I don't know if it was checked before the upgrade, maybe it explains the issue?
One thing to mention, not sure it's related - upgrade is not finished yet, we have one member upgraded and the other one is still running R80.20 but is not functioning (cpstop), so the cluster is actually broken at the moment.
Thanks
Labels
- Labels:
-
ClusterXL
-
Gaia
-
Open Server
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would advise completing the upgrade and seeing if the issue persists with Jumbo T45 or later applied.
There have been situations where similar symptoms were reported and linked to:
|
PRJ-30820, |
SecureXL |
In a rare scenario, after an upgrade, HTTPS traffic may be dropped. |
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Chris,
I'm on the latest JHF (take 66). We don't have HTTPS inspection of this traffic, and also it happens on other services and ports other than 443.
I will wait however until we finish with the upgrade, probably next Sunday, and will update if it's resolved.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Noted. There are other possible causes for these messages as the other discussion suggests. 😃
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
So upgrade is all finished, but issue is the same.
Only noticable change is that 99% of the logs now have TCP Flag: RST-ACK, which I know is generally normal to see. I just don't understand how come we never saw it prior to the upgrade and how to stop seeing it in logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
seeing the same thing "all of the sudden" No solution so far.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI,
Check this sk: sk137672 - How to change the 'TCP Half Closed timer' value.
with this solution we can improve the TCP close session processus.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have upgraded R80.40 ot R81.10 10 days ago, and we are monitoring large number of First Packet Isn't SYN drops, mainly with packets with tcp flag RST-ACK.
For a monitored connections between selected hosts, the increase of dropped packets is with 15% compared with the day before upgrade. Also some application issues are reported after upgrade and seems related to the drops.
I am not sure how solution in sk137672 is supposed to control.
Any suggestions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It appears that in my case, the connection is being expired after 15 seconds when the firewall sees the DEST-FIN. The client (Chrome/Edge) continues to send Keep-Alive packets for about 5 minutes, which are all dropped out of state. The client then sends several FIN-ACK packets, which are also dropped out of state. This is what the connection looks like before DST-FIN:
<00000000, 0a7a1550, 0000d333, ac1c2015, 00000050, 00000006; 0001c001, 40044080, 00000038, 000001cf, 00000000, 6387085d, 00000008, 13e3b1d3, d7e5c551, 00000003, ffffffff, ffffffff, ffffffff, 0000e800, 00000000, 80000000, 00000000, 00000000, ac442808, 00007f8e, 00000000, 02101801, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000; 3603/3615>
and after the DEST-FIN
<00000000, 0a7a1550, 0000d330, ac1c2015, 00000050, 00000006; 0001e001, 40044080, 00000038, 000001cf, 00000000, 6387085d, 00000000, 13e3b1d3, d7e5c551, 00000003, ffffffff, ffffffff, ffffffff, 0000e800, 00000000, 80000000, 00000000, 00000000, b8fd9088, 00007f8e, 00000000, 06ce0001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000; 14/15>
After the server sends the FIN-ACK to the client, the connection is updated with this 15 second timeout. The client (Chrome/Edge) sends the first Keep-Alive packets after 45 seconds and several more Keep-Alive packets at 45 second intervals, These Keep-Alive packets are all dropped out of state, as well as subsequent FIN-ACK packets. I'm not sure where the 15 second timeout is coming from; the TCP end session timeout is 5 seconds. Disabling SecureXL resolves the issue. I have a case open, but not getting anywhere quickly unfortunately. I'm not sure if this is impacting user experience, other than causing Chrome and Edge to use more sockets than necessary and generating lots of unnecessary logs. It seems to be that there is an issue with SecureXL expiring half-closed connections too early and would like to get to the bottom of it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Jonne_Hannon , do you have any solution about the problem ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please review sk180364 and see if it helps
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Might also be this from R81.10 Take 82.
PRJ-42445, | SecureXL | The Security Gateway may prematurely expire half-closed TCP connections and drop VoIP and HTTPS packets with "First packet isn't SYN". |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dilian,
sk137672 - How to change the 'TCP Half Closed timer' value is most helpful for me. I am still investigating the hotfix from sk180364, because that hotfix seems to remove the half-closed DST-FIN connection from the SecureXL connections table, but the firewall half-closed DST-FIN connection still has the 15 second timeout resulting is many "First packet isn't SYN" drops. I also note that sk137672 was recently updated with the following added information:
"Some of the Half closed connections ( DST-FIN ) by default will have 15 seconds timeout starting from the versions mentioned above.
To increase the default timeout to 3600 seconds for all Half closed connections please proceed with the procedure described above."
This seems to imply that the 15 second timeout is a change in behaviour. I'm not sure what the rationale is behind expiring the half-closed DST-FIN connections so quickly. Other than generating lots of "First packet isn't SYN" logs, I'm not sure if the user experience is impacted by expiring half-closed DST-FIN connections after 15 seconds. Maybe a Check Point employee can explain the rationale behind this change?
Thanks,
Jonne.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 13 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter