- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Management Plane Separation - mdps_tun connect...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Management Plane Separation - mdps_tun connected route
Hi all.
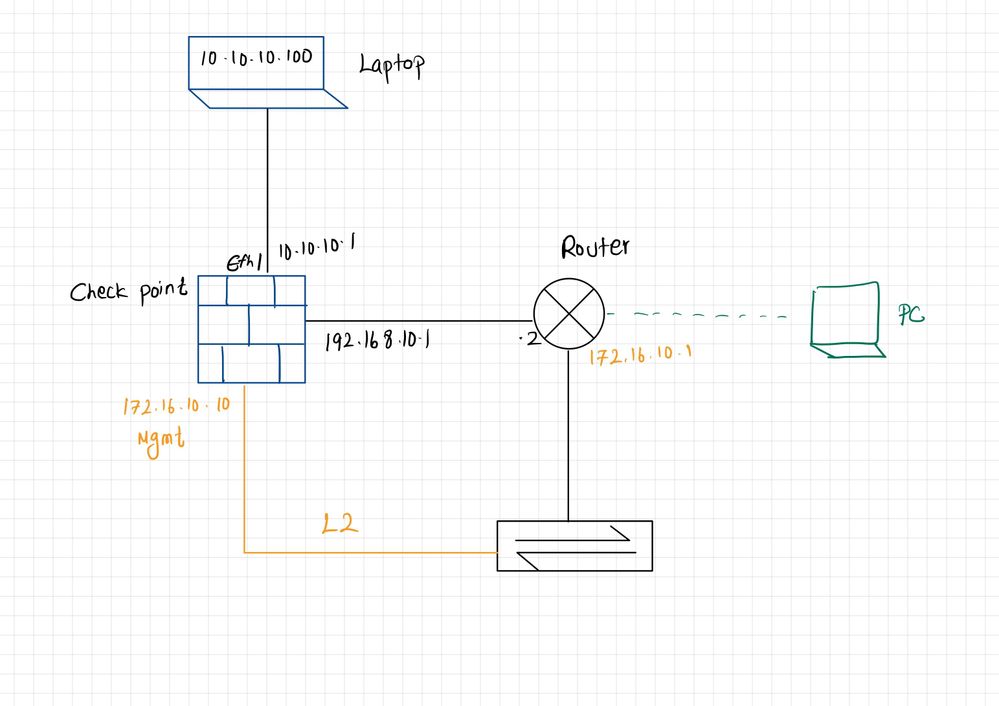
I recently made the change to enable management plane separation following sk138672. After the change, I noticed something I don't understand. Attached you will find a diagram that represents the network.
If I connect (ssh, https) from the PC (green) the traffic goes to the check point management interface directly and no issues. The traffic goes directly into the management interface and doesn't have to traverse the check point data plane.
If I, however, connect from the laptop (shown as black on top of the diagram) from a different network, I'm getting a connection refused from the firewall. My understanding is that the data plane and management plane are totally isolated so, the traffic should follow the following path.
Laptop > check point (eth1) > Router > check point management interface. However, it doesn't work at the moment. I already have a firewall policy to allow the connections. (Check point has a static route for 172.16.10.0/24 pointing to the Router)
If I check the data plane routing table, it has an entry for 172.16.10.10/32 shown as mdps_tun. Does that mean the traffic is not forwarded to the router?
C 172.16.10.10/32 is directly connected, mdps_tun
Thanks in advance.
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is the expected behaviour if you enabled the management plane. Any your question is?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the response. When you say expected behaviour, does that mean the firewall 'won't' allow traffic crossing from the data plane to the management plane even via a different path? (not directly crossing between the planes)
My question is, why the check point just doesn't send the traffic to the next hop which is the router?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, it does not mean that. You need to run some traces to see if the traffic from production plane to MGMT interface is dropped, and go from there. It is not enough info here to say why it happens.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, I will get in touch with the support to investigate further.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That would be a good idea
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI vsurresh, have you opened a case? I have also different problem with the mplane when it need to reach a network via the dplane.
the flow is blocked by the ANti Spoofing because it detect this is a local ip address. I have disabled the local antispoofing but the log is not anymore presented but the mplane don't get any response.
and I have another problematic to manage the NAT, because the Nat configuration is global and not by plane.
I think the better way to have a plan separation is to use the VSX.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Were u able to resolve this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there,
I have the same issue. The configuration is very similar and on dataplane I have the route to the network where Mgmt interface (on mplane) is connected.
If I ping the IP of MGMT from Laptop: traffic access on dataplane but don't go out from it. Strange behavior is that it works.
If i try ssh to the IP of MGMT from Laptop traffic follow the same path but I have a reset maybe because sshd is on mplane binded.
R81.20 JHR 84 for my environment.
Did you solve it in some way?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you ever get a proper solution to this issue? I have a similar topology, and am unable to pass traffic to/from the management interface once the management network's connectivity is handled by the Checkpoint FW itself. (Converting from another FW brand) Mgmt-initiated traffic fails when the first packet hits a dplane interface with an extended anti-spoofing hit. Inbound traffic to Mgmt from elsewhere takes the first packet arriving on a dplane interface thru the back door via that "mdps_tun" route, and then the outbound reply from mplane/Mgmt breaks flow symmetry and dies. Wondering if there's any legitimate reason for mdps_tun to exist at all and if there's any way to get rid of it but keep the rest of MDPS.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 11 | |
| 8 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter