Hi,
Am trying to install som MUH2 clients on jumpgates.
The GW is using VSX on R80.30 HFA 236
I get an error saying
"An error was detected while trying to authenticate against the AD server.
It may be a problem of bad configuration or connectivity.
Please refer to the troubleshooting guide for more help"
So checked the installation guide again.
https://sc1.checkpoint.com/documents/R80.30/WebAdminGuides/EN/CP_R80.30_IdentityAwareness_AdminGuide...
"
To configure Terminal Servers Identity Agents Authentication Settings with all Active Directories:
- Log in to SmartConsole.
- From the left navigation toolbar, click Gateways & Servers.
- Open the Identity Awareness Gateway object.
- In the left tree, go to the Identity Awareness page.
- Near the Terminal Servers, click Settings.
- In the Authentication Settings section, click Settings.
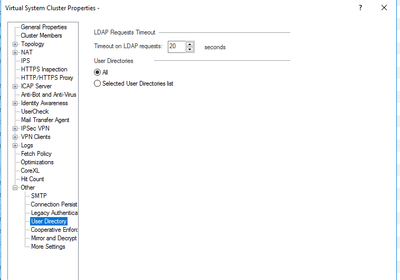
- Select All Gateway's Active Directories (under Security Gateway -> Other - > User Directory).
- Click OK to close the Active Directories window.
- Click OK to close the Terminal Servers window.
- Configure the Account Units Query settings:
- In the left tree of the Security Gateway object, click on the [+] near the Other pane.
- Click the User Directory pane.
- In the Account Units Query section, select All.
- Click OK to close the Gateway Properties window.
- Install the Access Policy.
"
But i honestly dont see the account units query. is the guide incorrect and it should be "user Directories"
the agent itself says connected but the users loged in says not authenticated.
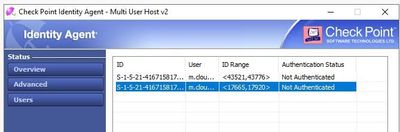
For other identitys we uses the identity collector. so there is ldap account units within the CMA
Regards,
Magnus
https://www.youtube.com/c/MagnusHolmberg-NetSec





