- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- 'Invalid segment retransmission. Packet dropped.'
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
'Invalid segment retransmission. Packet dropped.'
Hi All,
we have a client not able to connect to an FTP server. The connection goes through the internal firewall and then gets dropped by our external CP (80.10). The sync packet is okay, but then it is actually dropped by the same rule that should be allowing it with the 'Invalid segment retransmission. Packet dropped.' comment. Please see the below screen.
We initially thought it was down to the application (FileZilla), but it seems it's the same, for example, from win command line.
Thank you for any comments.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I ended up putting an Exception in the the Inspection Settings for 'Invalid TCP Retransmission' to get this fixed. Not a problem, but don't understand why it was seeing the traffic as a threat in the first place.
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you open one of those log entries, does it reference an SK?
These Inspection Settings may be relevant also:
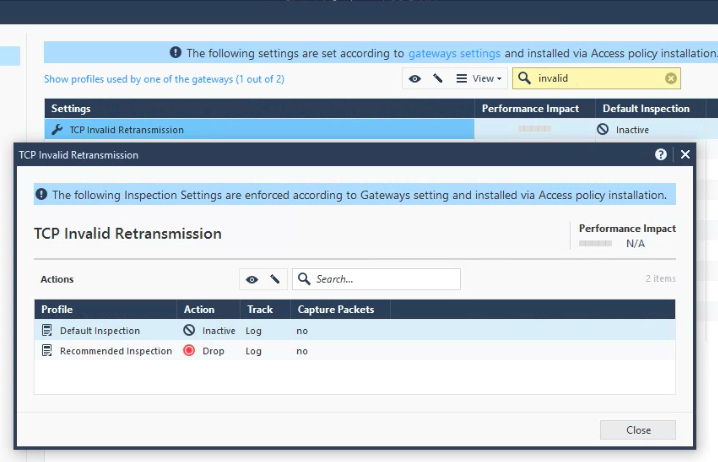

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank Dameon,
sorry about replying late; it got quite hectic I was then off for some time.
No SK, I get:
'SmartDefense Services
An advisory for this issue is yet to be published. The information will be updated soon.'
Looking at the settings, we have this set to 'Drop' on all profiles, as recommended by CP:
This morning I have put a device behind the CP firewall directly on the Internet and had no problems with any FTP commands (FTP passive-mode).
Apparently this was last used back in May, so we don't know when it stopped working. We have since moved from R77.30 to R80.10 but no access rules have been changed.
Thanks, Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I ended up putting an Exception in the the Inspection Settings for 'Invalid TCP Retransmission' to get this fixed. Not a problem, but don't understand why it was seeing the traffic as a threat in the first place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For that we’d probably need a TAC case with packet captures of the relevant traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We got this too, but per sk98081, disabling TCP Invalid Retransmission is something "highly recommended" not to do.
Blocking stuff without any real explanation on why is Check Point's M.O. --
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to clarify, did it drop specific packets but the connectivity remained and some packet still passed? Or from certain point all packets were dropped causing connectivity issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All packets are dropped.. multiple unrelated websites are not loading because of this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Yesterday we migrated one member of one a cluster from R80.10 to R80.30 and an one of the internal applications that has been working for years without issue (Through R77.30 and R80.10) stopped working, no changes were made in the application.
After debugging we found that the packets were dropped by the signature from this post: TCP Invalid Retransmission, we fixed the issue by making an exception in the corresponding signature.
Regards,
____________
https://www.linkedin.com/in/federicomeiners/
https://www.linkedin.com/in/federicomeiners/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We had the same problem upgraded from R80.20 to R80.30 and had application stop working (internal app) TCP Invalid Retransmission.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Had the issue this morning - folks going to Siebel. Worked yesterday on R80.10, upgraded to R80.30 JHF Take 50 and we had issues this morning with all users.
Exception added and problem solved.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, we have the same Problem. After Migration from 77.30 to 80.30 we have "TCP-Retransmission Drops"
One of our internal web application working for years without issues. After this Migration the application is stopped working, no changes were made in the application.
We found…. http://[ip-address]/wording/ is working
http://[ip-address]/wording/?search=word1+word2&initSearch=2&core= is not working
If we delete the "+" sign, it is working. IT seems Checkpoint 80.30 don't like "+" signs.
We don´t use application filtering or other blades - only IPS.
Workaround: We fixed the issue by making an exception in the IPS.
Any idea what's wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have the same problem, TAC said that an upgrade to R80.30 Take >= 214 will resolve this issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am seeing the same issue with the TCP Invalid Retransmission to Library of Congress. Added exceptions didn't help. I tested by making Drop to Accept and works perfectly. We had the ver R80.3 and wonder if anyone else can provide some advise.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did it work for you? We are running R80.3 and keeping getting problem with Library of Congress. Dropped and TCP invalid retransmission. Adding exception didn't do anything. I wonder if anyone has any other thoughts on this problem?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 12 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


