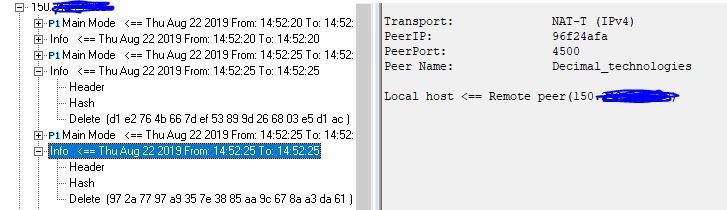
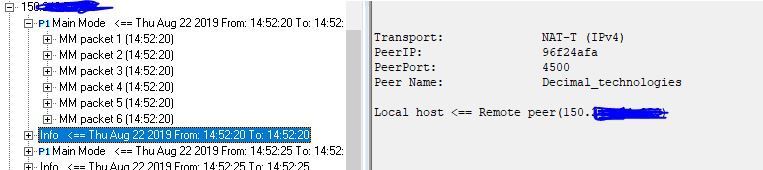
All that means is that you sent an encrypted packet to your peer with an SPI it did not recognize because the tunnel associated with that particular SPI no longer exists on the peer end. In response the peer sends your firewall a "Delete SA" telling your firewall to delete it on that end. So the particular tunnel you tried to send to with a nonexistent SPI is "down", yes. But when some interesting traffic arrives on either end the tunnel should come back up, unless the tunnel can only be initiated in one direction. However Delete SAs don't really work right in an interoperable scenario, so your firewall's SmartView Monitor will show a VPN tunnel as "up" even though the peer thinks it is down.
Any time you set up a new VPN you need to ensure that either peer can successfully initiate a working tunnel from scratch. Due to a subnets/Proxy-ID mismatch it is all too common that the VPN can only be successfully initialized in one direction. So if the interesting traffic arrives at the side that is unable to initiate a working tunnel, the VPN will be down until the other side receives some interesting traffic and tries to bring it up from that end. Once a tunnel is up and working it generally does not matter which side initiated it, the tunnel will be 2-way for purposes of passing traffic.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course