Hi all Checkmates,
This is my first post, so first of all thanks for all the great post and knowledge sharing.
This weekend I change my FW setup from identity sharing to identity collector, for a simpler identity sharing between my firewalls
On the firewall clusters I also disabled "Active directory query" as this would be done on the ID Collector.
Now FWCLUS01/DMZ ignores more than 7 logins
"x.x.x.x with machine: Termial-Server100@domain.xzy, was marked as a multi user host IP. user login events for that IP will be ignored from now on"
It is ingnored when it hit's the native Multi-user host Detection Threshold = 7 . I have tried to change this threshold by using the cli configuration tool "adlogconfig a" and change the "Multi-user host Detection Threshold" to "10" and install policy.
This does not change the behavior.
Do any of you know if this setting is an option when running with Identity collector ?
The Firewall (FWCLUS02/WAN) collecting user from terminal server via MUH Agent is accepting the the increasement of "Multi-user host Detection Threshold" but I guess this is because the MUH Agent config is this FWCLUS02/WAN and it looks at the parameter.
My firewall setup:
The user on the terminal server environment is auth with MUH agent against FWCLUS02/WAN=Blue line
Identity sharing is used on both FWCLUS01/DMZ and FWCLUS02/WAN shown as the = Green line
VDA User A is connecting to the DMZapplicaiton = red
All FW/SMS is running R80.40 Take 118
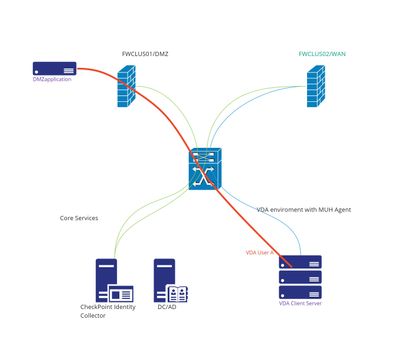
When the VDA user A connects to DMZapplication and FWCLUS01/DMZ looks up the amount of user on the terminal server from identity collector and if it is above 7 it will add into this state "x.x.x.x with machine: Termial-Server100@domain.xzy, was marked as a multi user host IP. user login events for that IP will be ignored from now on"
It looks like when Identity collector is used it looks like i'm missing the parameter to increase "Multi-user host Detection Threshold" to more than 7.
Hope someone in the checkmates community have been through the same and have a solution for it.
/Henrik



