- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Identity awareness blade issue
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Identity awareness blade issue
Hey guys,
I hope someone can clarify this for me. I dont believe it ever worked properly for the customer. So, here is the situation. IA blade is enabled and there are few access roles configured. It does work for the most part, but one thing that fails is this...
So, if same user logs into multiple machines, then ONLY first machine they logged into will give them Internet access, not any sequential ones. So say user joesmith logs into windows box with IP 10.10.10.10, then to another windows with IP 10.10.10.11 and 3rd one 10.10.10.12...well, ONLY 10.10.10.10 IP machine will give them proper external access, not any other ones.
Option on gateway to assume that only one user is connected per machine is not checked, so logically, one would think that would allow same user to get access when connected to multiple machines. The drop we see on fw is that it comes to right layer and then explicit clean up rule drops the traffic, since it does not recognize access role association. We tried revoking IP, user, pdp update all...nothing worked.
Not sure if there is something else Im missing here?
Thanks as always!
Best,
Andy
Andy
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just quick update guys...spoke with TAC and Harry had me do below options (we had checked internal users before, as well as all gateways directories). Once this was done, we pushed policy, but also had to install identity agent on windows machine we tested and then same user worked fine! I will still ask customer to test with few different users.
Best,
Andy
Andy
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81.10 mgmt jumbo 9, R80.40 jumbo 120 gateway cluster
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk115776: Specific user is not identified by Identity Awareness
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a lot G, will check this in a bit.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I really hope this works. I did the changes and will ask customer to test. Funny enough, I went to that gateway setting thats in sk yesterday, but totally omitted the part about "automatically exclude users...". My bad...will let you know for sure if this fixes it. Thanks as always brother, grateful for all the help.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sadly, did not help. I made changes and asked client to test, but same behavior, no access when same user logs into 2nd machine. I will call TAC later and see if we can do some tests, since we already have active case opened for this since the weekend.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
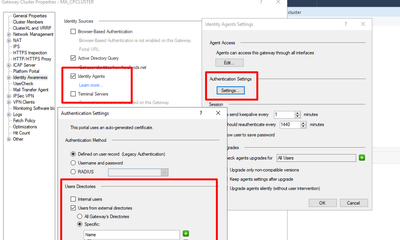
Try enabling any of the above, depending on the source from where your identities are being learned.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I ran it on both cluster members and asked client to test, so will see if any difference. Will keep you posted.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No luck, just tried.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just quick update guys...spoke with TAC and Harry had me do below options (we had checked internal users before, as well as all gateways directories). Once this was done, we pushed policy, but also had to install identity agent on windows machine we tested and then same user worked fine! I will still ask customer to test with few different users.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have had the issue that needed to install the identity agents if users roam quickly between wifi/lan to make sure update correctly.
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I never realized that before, but I guess IA agent is needed on windows in situation like this. Otherwise, if its only 1 user logged into 1 machine at the time, no need for IA agent.
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 14 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter