- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Identity Collector Not Collecting dot1x sessio...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Identity Collector Not Collecting dot1x sessions from Cisco ISE
Hello
We are using 802.1x on our wireless network. We do the verification via Cisco ISE. I collect usernames from Cisco ISE 2.4 with Identity Collector software and send them to Checkpoint. Thus, I can easily record which IP address is used by which user. We will soon start implementing 802.1x on the wired line. I have made my adjustments and I can use it by verifying. I see my own session in sessions on Cisco ISE, but Checkpoint Identity Collector does not collect it from Cisco ISE. So I can't map the wired IP address to the username.
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello,
not sure what guide you followed for ISE pxGrid and CheckPoint Identity Collector set-up, but from ISE you should use SGTs for your interesting traffic and in CheckPoint you create Identities based on those SGT's.
In our implementation, we can clearly identify the machines that ISE authenticate and pass the data further to CheckPoint through IC, but the user is still not identified properly - aka mapped in AD properly....
also the SGT's are properly mapped on the appropriate Identity Groups.
ty,
PS: i think we could get users properly identified, if we would address AD LDAP Global Catalog and not the standard one....
PS2: we do ISE dot1.x on copper (on almost whole network by the end of the year) and wifi (already done)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Getting the usernames is one thing, matching it to information in AD is another, and is the critical piece of making this work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On the wireless line, users are drawn with identity collector. I see the login processes of those connected to the wireless line on the check point. Although the information of those who verify on the wired line is on Cisco, the identity collector does not receive them. In fact, they both have the same scenario, but I don't understand why they pull the sessions on the wireless and not on the wired.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
still you did not say how you "collect usernames from Cisco ISE 2.4 with Identity Collector software and send them to Checkpoint."..... are you using pxGrid, or are you using RADIUS Accounting ?
if you state that you have everything OK from WiFi 802.1x , then replicate that on the cable and you're good to go.
without details we can't suppose stuff or see it in a crystal globe.
ty,
PS: waiting for details and maybe we can guide you properly 😊
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
Cisco ISE does not support Radius Accounting. With the pXGrid service of the Identity Collector, I am getting the validation records over Cisco ISE. Gateways are also connected to the Identity Collector, so the Collector sends them to Checkpoint.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello @sukruozdemir ,
so ISE doesn't send anything to Identity Collector, the IC collects machine and user authentication from ISE via pxGrid.
therefore I don't see why you state that you don't get anything for cable authentications ....
do you have in your IC settings some filtering ? otherwise all authentications (wifi or cable) would be visible in IC via pxGrid.
can you give an example of an authentication that you see it in ISE/IC&GW and one that you don't . (as the ISE details you offered doesn't show anything wrong)
ty,
PS: for the Radius part, I was saying that you can point the network equipment to IC and that would collect the radius accounting data (still I need to look over documents here, but roughly it's like that)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I restored the IC and ISE integration. I regenerated all certificates. After activating the Accounting feature on the switch, session information began to appear on the IC. But this time it does not send it to Checkpoint. The IP and Username of the wireless connections are matched in Checkpoint, but the wired one is not.
I don't use filters.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @sukruozdemir ,
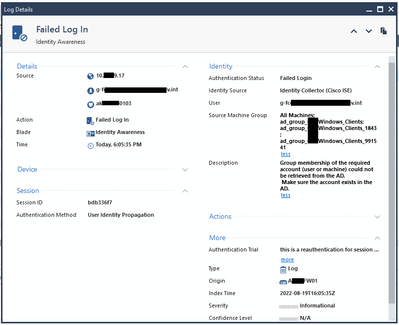
The IC Login Monitor shows AD events, not ISE events....
The ISE ones looks like my first screenshot....
As for the Accounting part, are you sending accounting to IC separately ?
So, an user that authenticates on his laptop, either by cable or by WiFi, will generate an event on AD server that will be captured on the IC. So why are you looking into getting ISE data into IC/Checkpoint, as you already have that data from AD side....
In our cases, we have machines/users that are not AD enrolled, therefore we grab that data from ISE too and identify it.
Thank you,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Users are not using Active Directory. I'm throwing radius validation queries to active directory.
I am doing user authentication and authorization with ISE. With IC, I attract users who have been authenticated on ISE via pxGrid. AD is not attached to IC, ISE is attached!
I don't send accounting to IC separately.
There's no need to over-complicate the subject.
Users verified with wireless 802.1x in ISE can be seen in the IC, they are logged in at checkpoint IA with their IP addresses, and I see the source user as well as the IP address in the logs. With the same logic, wired 802.1x logs in to the ISE, I see the login process and the ip address on the IC, but the IC does not send them to Checkpoint IA.
Thank you,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would suggest to contact TAC to get it resolved...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I didn't change anything and now it started working in an interesting way.
I think there are bugs between versions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@sukruozdemir , weird indeed.
what IC version are you using? as we had some issues with R81.035.000 and the most stable one (and recommended) is R80.119.000 .
ty,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
Actually I was using version R80.119.000. When I had problems with this version, I upgraded to R81.035.000 version and did all the configuration from the beginning. There are definitely bugs in both versions.
It is very difficult to match the moment when there is a problem, as it is said to show us when there is a problem this time if I create support. With TAC, it becomes almost impossible to get a solution.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 23 | |
| 19 | |
| 8 | |
| 6 | |
| 6 | |
| 6 | |
| 6 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter