- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Identity Collector Exclusion List
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Identity Collector Exclusion List
If you leave the excluded and included items blank, are all items sent, or do you have to specify all networks you want to include?
If I add one subnet in the included list, does that mean everything else is excluded, even if not defined in the excluded list?
There's no real documentation I can find for this. The Identity awareness guide just says "Defines IP addresses and networks to include or exclude".
I would just like to test Identity Collector in one subnet, and exclude that subnet from AD Query.
- Tags:
- identity collector
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
19 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You find more information in the Identity Collector R77.30 Release Notes.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
r 77.30 release notes show the same thing as the r80.10. It says you can use it to exclude and include, but no details as to how the exclusions work. (Does include inherently exclude all non included networks?)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Royi Priov - could you help here pls? ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would assume that basic principles of logic do apply ![]() . Main feature here is optimization by excluding unnecessary information, but it makes also possible to strictly limit the collected information by using include.
. Main feature here is optimization by excluding unnecessary information, but it makes also possible to strictly limit the collected information by using include.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's what I would assume as well. The features seem almost mutually exclusive, kinda like a fail open or fail close. I wonder which one is determined first, the exclude or the include?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It does make no sense to use both - this filters the data from Collector before forwarding it to the GWs. As explained in the documentation, this comes handy to filter unnecessary data. The other side would be a kind of whitelist, limiting which data shall be forwarded to the GWs, that can be usefull under special circumstances.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It does make sense to use both. Example:
- Include: 10.105.0.0/16
- Exclude: 10.105.20.0/24
I agree with David, the R80.10 and R80.20 documentation regarding the Identity Collector does not have the right quality.
It looks like it's done on purpose, in order to sell professional services, isn't it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Kris Pellens wrote:
It looks like it's done on purpose, in order to sell professional services, isn't it?
Hi Kris,
I really feel sorry this is your opinion.
Taking this into the constructive side, I will appreciate if you could tell me what you are missing in our documentation.
Thanks,
Royi Priov
Team Leader, Identity Awareness R&D.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Royi,
Thank you for your feedback. We're currently implementing Identity Management (using Microsoft Active Directory and Cisco ISE).
At the moment, we have the following set up:
- A VSX/VSLS cluster (R80.20)
- A Security Management Server (R80.20)
- Identity Collector (sk134312)
- Identity Agent Terminal Server (sk134312), running on Windows 2012
The online documentation (i.e. the Identity Awareness R80.20 Administration Guide) is not reflecting those updates. It would be nice to have the online documentation be aligned with the latest updates.
We're also experiencing connections issues on the terminal servers.
Since the installation of the Terminal Server Agent, sometimes all tcp ports on the server are occupied (port starvation); resulting in connection errors (hence: user frustration). The number of users is less than 20.
Today, we've experienced a TS crash, caused by the agent:
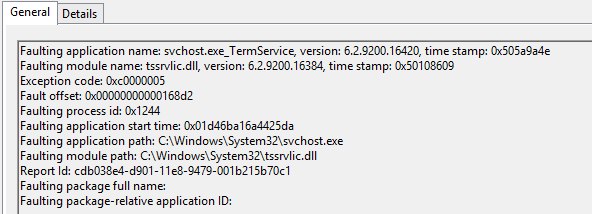
(A TAC case has been opened for that).
The Check Point community is also asking for a best practices and configuration document on how to integrate Check Point Identity with Cisco ISE. Is this something you can provide, because your team did the tests up to ISE 2.4.
Many thanks.
Kind regards,
Kris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please explain what this comment has to do with the topic Identity Collector Exclusion List ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
As written here, when identity is received on the Identity collector, in order to be sent to the gateway, it should pass all filters for both global and local gateway filter (available in our latest version - sk134312).
Therefore, if there are both inclusion and exclusion lists, both filters will be applied.
Thanks,
Royi Priov
Team Leader, Identity Awareness R&D.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So if I have nothing in the inclusion list, everything with pass.
If I have 1 subnet in the inclusion list, only that subnet will pass.
Is that correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
correct.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello All,
I still have a question regarding the Include / Exclude option for identities.
Currently I have an Identity Filter that excludes all service Accounts (regex identity svc*), yet we need to include an account named svcJohnDoe. So I added a new Include entry for that account, but is still not seen by the gateways.
According to your explanation, both should be applied, but it seems to me that the exclusion is overriding the include entry.
Can you please help?
Kind regards,
Nuno Ramalho
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
unfortunately I still can't find any comprehensive documentation which explains how the identity collector manages filters. In the documentation "https://sc1.checkpoint.com/documents/Identity_Awareness_Clients_Admin_Guide/Content/Topics/Identity-... you only document how to use the interface. I guess that should be a given, that an administrator understands the interface.
What's the logic behind the filters?
I have a global filter which is completely empty so everything is allowed.
I have a second filter which excludes certain subnets and includes certain access roles via AD.
Now I would like to add exceptions for the excluded subnets to allow some machines access to the internet.
Which filter has precedens over the other. Are they processed top to bottom, although I can't change the order they are listed in? Can I use includes and excludes per section (network, identity, domain ) within one filter at the same time or do I need separate Filters?
I hope you can update either the documentation or some links:
sc1.checkpoint.com/documents/Identity_Awareness_Clients_Admin_Guide/Content/Topics/Introduction.htm
Best regards
Jürgen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Jürgen,
From what I remember, the filters are applied in one action (both global and local filters). It means, for the identity to be sent to a PDP gateway, it should pass the global and all local filters.
By the way, in Infinity Identity we are about to present a new filtering mechanism, which will support also group filtering and other parameters. I have attached a snippet from our UI.
Send me a private message if you want to get more information about it.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Royi,
Thank you for your reply.
You say that filters are applied in one action, both Global and Local filters, but still there is no reference to how include and exclude filters are applied when used together.
In our case, we have no exclusions at Global level. we only have a local filter that includes both excluded accounts (svc*) and some include filters (e.g. svcTEST), but the account svcTEST is not passed to the gateways. It seems that the exclusion is overlapping the inclusion, but I can't find any information about this, neither a way to address this need.
New feature looks very nice, thank you for sharing. Is this included in new IDC R82, released May 11th?
Thanks in advance,
Nuno Ramalho
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@nmpramalho I think I understand your point.
as the filter applied in once bulk, soon as one of the condition matches, the action is performed. so the svcTEST applies on svc* therefore dropped.
If this is indeed the case, it seems that it is a legit RFE to send with your local SE team.
As for Infinity Identity, it is a new application in Infinity Portal, which communicates with Identity Collector and also with Entra ID, Intune, Defender and Harmony clients.
Check this thread for more details:
The filters page I showed is part of this application. In case you will create the following filters it will work with Infinity Identity:
1. identity "svcTEST" include
2. Identity regex "svc*" exclude
If needed, contact me for more details privately here or at royip@checkpoint.com
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Royi,
thank you for your reply. So from this thread I understand that the first match applies the filter. I will try out this logic for Identity Collector filters in R81.20.
- Go from specific rules to general rules
- Go from top to bottom
- Includes come before Excludes
- once a filter matches - no more processing
If anyone else has tried out a couple of things feel free to share your experience.
Have a nice weekend!
Best regards,
Jürgen
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 13 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


