- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- ISP redundancy
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
ISP redundancy
Hi everyone,
I had some questions about ISP redundancy in R80. I know its not that different than previous versions, but its been awhile since I troubleshot it and was wondering if someone could confirm below.
I have a customer with single R80.30 gateway managed by R80.30 mgmt server and they just set up 2nd ISP link, so they are wanting to implement isp redundancy. BEFORE enabling it in dashboard, can someone answer the following:
-what routing changes would need to be made?
-what about policy routing?
-do any dns changes have to be done via cli or web GUI?
-how would client to site and site to site vpn work when primary isp link fails? Any changes have to be done on the tunnels prior to enabling isp redundancy?
-would it affect any gateways with 3rd party certificates?
Also, I did not really find any good isp redundancy document, aprt paragraph from R80.40 admin guide.
Thanks in advance!
Andy
Best,
Andy
Andy
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
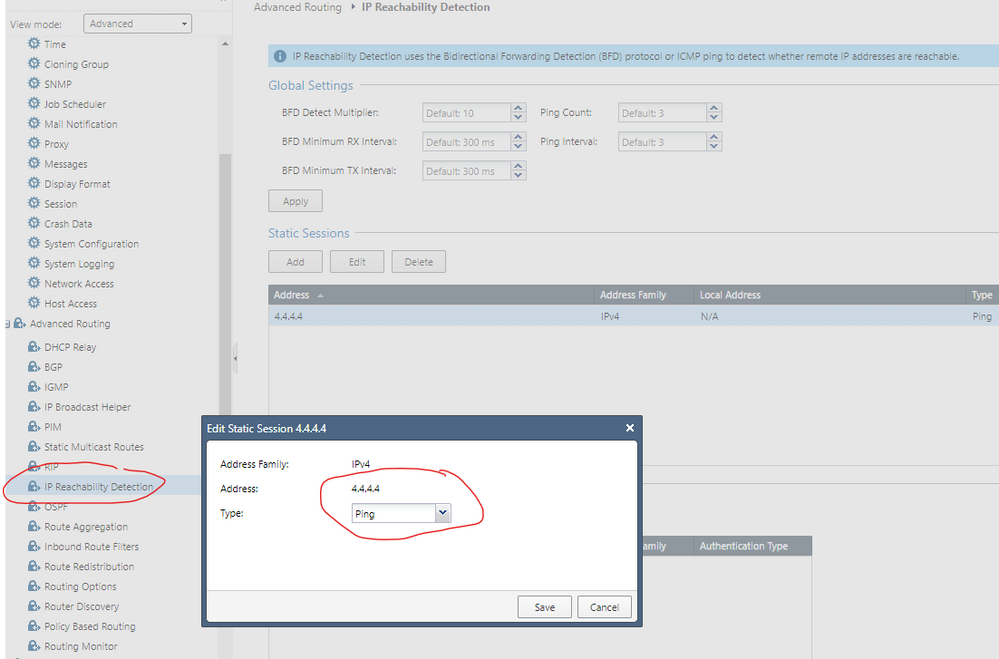
you an configure a host to be "monitored" via ping. You should configure two IPs, each one from one of the ISPs.
And then these IPs can be used to be monitored in your PBR configuration. You have to configure two routes with different priorities.
If a monitored host answeres the ping, this route will be active and used regarding the configured priority. If your primary ISP will fail, the ping test to the monitored host fails too and the second route entry will be used.
Hope, this makes the PBR with more then one ISP understandable.
Wolfgang
PS: snip from the what's new section R80.30
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-what routing changes would need to be made?
Normally nothing, the routing configuration via two default gateways (your ISPs) will be done via SmartConsole.
-what about policy routing?
PBR with ISP redundancy is supported starting from R80.30.
-do any dns changes have to be done via cli or web GUI?
You can rewrite DNS-requests, configuration will be done via SmartConsole (DNS-proxy)
-how would client to site and site to site vpn work when primary isp link fails? Any changes have to be done on the tunnels prior to enabling isp redundancy?
You can use both ISP links for your VPN, in load sharing or HA mode. Settings for these VPN connections are configured via VPN link selection.
-would it affect any gateways with 3rd party certificates?
Can you explain this to understand your needs.
Good documentation will be the old one for R77.30 to understand the concept and configuration
HOW TO CONFIGURE ISP REDUNDANCY IN NGX R65 - R77.30 VERSIONS
and these sk
Advanced configuration options for ISP Redundancy
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a lot for that Wolfgang, appreciated. Just to clarify some poinhts I made (sorry for not being more clear about them). Below are actual questions customer asked me:
-What has to be done in configuration to ensure IPSEC Office Mode Tunnels and the SSL VPN Mobile client will work on both interfaces?
-What additional DNS configuration needs to be done in the Checkpoint Redundancy configuration to ensure the firewall resolves the interfaces with no issue.
-a capture of any other configurations that we have not yet discussed above that need to be changed.
I know for VPN, there is a setting under isp redundancy page in dashboard to "apply settings to vpn", which I read would mean it overrides existing link selection settings, but I believe thats what most customers would want anyway, specially in case like this, where main link is fiber 1 GB connection and backup is only 20 MB. For dns, I dont think they need to change actual dns servers. but the dns proxy setting says its if you have servers that are accepting incoming connections, then needs to be configured.
Dont worry about my certificate question, as Im sure that does not apply to ips redundancy. He was more asking me that if they use 3rd party cert for mobile access or https inspection if that would be affected, but Im pretty sure it would not be.
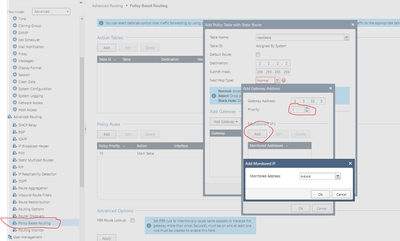
Also, for policy based routing, I do see in my lab it gives you options to set up the routes, but based on priorities and interfaces, NOT actual isp link, but corretc me if Im wrong, you can simply choose interface corresponding to the isp link to reflect that route, correct?
Again, thanks for the response!
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
default configuration in ISP redundancy is HA-mode. One ISP is active and the other in standby. All connections (include site2site and remote access VPN) are sent and received via the active ISP. ISP Redundancy "Apply settings for VPN traffic" is not working with 3rd party vendors shows a good example what means the setting "apply to vpn ...."
Rewriting DNS will be necessary only if you have internal servers they are reachable via external DNS-names. If your main ISP link is failing these DNS names are pointing to not reachable IP-addresses. This has to be changed to addresses for your backup ISP.
IPSEC-Tunnel beetween CheckPoint gateways are no problem with ISP redundancy. They do RDP-probing ( Check Points own probing protocol) to test connectivity to all available interfaces. In HA configuration the active ISP is used first. Same apply to remote access VPN clients.
Policy based routing and ISP-redundancy does not work together. Meaning you can use both together but they don't interact. Configure host probing for your PBR routes to check the availability of the ISP-links.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Wolfgang,
Thanks, but Im still confused about your last point. You said isp redundancy is supported with policy based routing in R80.30, but in sk about pbr on support site it says it not. Which is true??
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also, not sure what host probing you are referring to for PBR...can you elaborate?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
you an configure a host to be "monitored" via ping. You should configure two IPs, each one from one of the ISPs.
And then these IPs can be used to be monitored in your PBR configuration. You have to configure two routes with different priorities.
If a monitored host answeres the ping, this route will be active and used regarding the configured priority. If your primary ISP will fail, the ping test to the monitored host fails too and the second route entry will be used.
Hope, this makes the PBR with more then one ISP understandable.
Wolfgang
PS: snip from the what's new section R80.30
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks!
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Wolfgang
Can you explain more "PBR with ISP redundancy is supported starting from R80.30."
Because in the sk https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
is not supported. And in my tests it did not work (nat hide was not applied correctly for PBR routed connections...)
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good point Eduardo...I was wondering that exact same thing as well.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please check your NAT rules. You have to use an automatic NAT rule with „hide behind gateway“ enabled.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tagging @PhoneBoy to get some clarification.
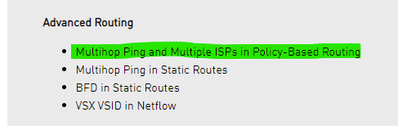
Policy-Based Routing (PBR) on Gaia OS shows ISP redundancy not supported with PBR, up to R80.40.
From R80.30 what’s new “Multihop Ping and Multiple ISPs in Policy-Based Routing“ will be supported. Does this indicate ISP redundancy is supported ?
From a technical view it‘s working, but is it supported ?
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
Yes, NAT rules were checked, and worked if ISP redundancy was off.
Well Wolfgang, probably you will get somekind of ISP redundancy with PBR and using “Multihop Ping and Multiple ISPs in Policy-Based Routing“, but if you enable ISP redundancy in the gw the nat rules will not work . Take a looh ar https://community.checkpoint.com/t5/General-Topics/ISP-Redundancy-with-PBR/m-p/67783
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ISP Redundancy and PBR are mutually exclusive features at the moment.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 12 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter