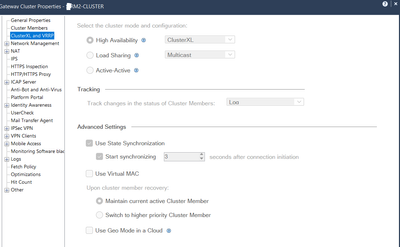
We are using ClsuterXl with 2gateway cp9100 and we have two isp, we have configured isp redundancy but when isp 1 down then we are not able to get internet, we have configured ISP Redundancy from ClusterXL, I have mentioned some output below.
Please provide the output of the following:
- cphaprob -a if
→ To check which interfaces are monitored in ClusterXL and if they failover correctly…find the logs below..
[Expert@RM2-FW02:0]# cphaprob -a if
CCP mode: Manual (Unicast)
Required interfaces: 5
Required secured interfaces: 1
Interface Name: Status:
eth1 UP
eth2 UP
eth3 UP
Sync (S) UP
Mgmt Non-Monitored
bond1 (LS) UP
S - sync, HA/LS - bond type, LM - link monitor, P - probing
Virtual cluster interfaces: 7
eth1 125.17.XX.XX -ISP1
eth2 14.195.XX.XX-ISP2
eth3 10.20.xx.10
bond1 10.199.xx.5
vpnt1 169.254.xx.118
vpnt2 169.254.xx.157
vpnt3 169.254.xx.222
[Expert@RM2-FW02:0]#
- ISP Redundancy Method (Load Sharing or Primary/Backup?)
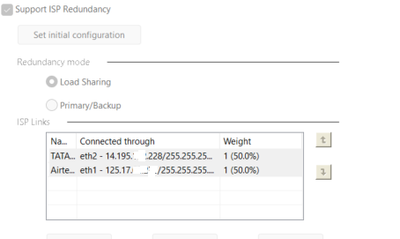
- NAT Rules Overview
→ Are you using "Hide NAT behind gateway" or static NAT? , we are using hide behind gateway NAT. - Show route all.
EMB-SJRM2-FW01> show route all
Codes: C - Connected, S - Static, R - RIP, B - BGP (D - Default),
O - OSPF IntraArea (IA - InterArea, E - External, N - NSSA),
IS - IS-IS (L1 - Level 1, L2 - Level 2, IA - InterArea, E - External),
A - Aggregate, K - Kernel Remnant, H - Hidden, P - Suppressed,
NP - NAT Pool, U - Unreachable, i - Inactive
S 0.0.0.0/0 via 14.195.XX.XX, eth2, cost 0, age 55725
C 1.1.1.0/24 is directly connected, Sync
SYNC
C 10.20.XX.0/28 is directly connected, eth3
Sens ASA
C i 10.20.XX.0/28 is directly connected, eth3
Sensopart ASA
S 10.98.XX.0/23 via 169.254.106.117, vpnt1, cost 0, age 55725
AWS SG Tunnel
S 10.159.XX.0/19 via 169.254.84.157, vpnt2, cost 0, age 55725
BFL AWS Mumbai
S 10.162.XX.0/16 via 169.254.XXX.221, vpnt3, cost 0, age 55725
BFL BFSI AWS Mumbai
C 10.199.XX.0/28 is directly connected, bond1
CORE_SW _1_2-LAN
C i 10.199.XX.0/28 is directly connected, bond1
CORE_SW _1_2-LAN
S i 10.199.XX.0/28 via 10.199.XX.1, bond1, cost 0, age 55725
FIREWALL VLAN 199
ClusterXL snap below.