- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- Firewall and Security Management
- :
- IOC feeds
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IOC feeds
Hey boys and girls,
Happy Friday and weekend 🙂
Just figured would share some IOC feeds I put together in my lab, I counted and there is about 2000 known bad IPs that are blocked via all of them together, so hopefully it can help others.
If anyone has any others to share, please do so. FYI, you do need either AV or AB blades enabled to use IOC feeds and for best results, I recommend R81.20 version, as it also lets you test the feeds from smart console.
I truly believe everyone should do this method, as lets be honest, with ever evolving threats from the Internet, who has the time to manually keep updating bad IPs to be blocked? I will take a wild guess and say probably no one lol
Best,
Andy
[Expert@azurefw:0]# ioc_feeds show
Feed Name: talos_1
Feed is Active
File will be fetched via HTTPS
Resource: https://www.talosintelligence.com/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: sans
Feed is Active
File will be fetched via HTTPS
Resource: https://isc.sans.edu/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: isacs
Feed is Active
File will be fetched via HTTPS
Resource: https://www.nationalisacs.org/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: Imfraguard
Feed is Active
File will be fetched via HTTPS
Resource: https://www.infragard.org/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: virustotal
Feed is Active
File will be fetched via HTTPS
Resource: https://www.virustotal.com/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: Cisa
Feed is Active
File will be fetched via HTTPS
Resource: https://www.cisa.gov/topics/cyber-threats-and-advisories/information-sharing/automated-indicator-sha...
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: googlesafebrowsing
Feed is Active
File will be fetched via HTTPS
Resource: https://safebrowsing.google.com/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: spamhaus
Feed is Active
File will be fetched via HTTPS
Resource: https://www.spamhaus.org/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: abuse.ch
Feed is Active
File will be fetched via HTTPS
Resource: https://abuse.ch/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: virusshare
Feed is Active
File will be fetched via HTTPS
Resource: https://virusshare.com/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: talos
Feed is Active
File will be fetched via HTTP
Resource: http://www.talosintelligence.com/documents/ip-blacklist
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: sslbl
Feed is Active
File will be fetched via HTTPS
Resource: https://sslbl.abuse.ch/blacklist/sslipblacklist.csv
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: cybercrime
Feed is Active
File will be fetched via HTTPS
Resource: https://cybercrime-tracker.net/ccamlist.php
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: reputation
Feed is Active
File will be fetched via HTTP
Resource: http://reputation.alienvault.com/reputation.data
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: ipspamlist
Feed is Active
File will be fetched via HTTP
Resource: http://www.ipspamlist.com/public_feeds.csv
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: botvrij
Feed is Active
File will be fetched via HTTPS
Resource: https://www.botvrij.eu/data/ioclist.hostname.raw
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: Known_bad_IPs
Feed is Active
File will be fetched via HTTPS
Resource: https://www.misp-project.org/feeds/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: github-blocklist
Feed is Active
File will be fetched via HTTPS
Resource: https://github.com/firehol/blocklist-ipsets
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: feodo_tracker
Feed is Active
File will be fetched via HTTPS
Resource: https://feodotracker.abuse.ch/downloads/ipblocklist_recommended.txt
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: emerging_threats
Feed is Active
File will be fetched via HTTP
Resource: http://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: test-feed
Feed is Active
File will be fetched via HTTPS
Resource: https://csp.infoblox.com/
Action: Detect
User Name:
Feed is centrally managed
Total number of feeds: 21
Active feeds: 21
[Expert@azurefw:0]#
Best,
Andy
Andy
89 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for sharing! I have been looking for more of these to add to our current roster.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very welcome, happy to help. Unlike Ed Sheeran's song "Perfect", this is far from it, but its something lol
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I will keep updating as I find more
Andy
Feed Name: ipq
Feed is Active
File will be fetched via HTTPS
Resource: https://www.ipqualityscore.com/
Action: Prevent
User Name:
Feed is centrally managed
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know this is Fortinet, but it has 107 entries
Andy
Feed Name: fortiguard
Feed is Active
File will be fetched via HTTPS
Resource: https://www.fortiguard.com/services/ioc
Action: Prevent
User Name:
Feed is centrally managed
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Microsoft, 269 entries, pretty good
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The BEST I found so far, almost 4000 entries.
Andy
https://www.cisco.com/c/en/us/products/security/ngips/index.html
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Most UPDATED I have so far. But, will keep adding whatever else I find.
Andy
[Expert@azurefw:0]# ioc_feeds show
Feed Name: cisco
Feed is Active
File will be fetched via HTTPS
Resource: https://www.cisco.com/c/en/us/products/security/ngips/index.html
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: cortex
Feed is Active
File will be fetched via HTTPS
Resource: https://xsoar.pan.dev/docs/reference/integrations/cortex-xdr---ioc
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: microsoft
Feed is Active
File will be fetched via HTTPS
Resource: https://www.microsoft.com/en-ca/security/business/siem-and-xdr/microsoft-defender-threat-intelligenc...
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: fortiguard
Feed is Active
File will be fetched via HTTPS
Resource: https://www.fortiguard.com/services/ioc
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: ipq
Feed is Active
File will be fetched via HTTPS
Resource: https://www.ipqualityscore.com/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: talos_1
Feed is Active
File will be fetched via HTTPS
Resource: https://www.talosintelligence.com/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: sans
Feed is Active
File will be fetched via HTTPS
Resource: https://isc.sans.edu/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: isacs
Feed is Active
File will be fetched via HTTPS
Resource: https://www.nationalisacs.org/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: Imfraguard
Feed is Active
File will be fetched via HTTPS
Resource: https://www.infragard.org/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: virustotal
Feed is Active
File will be fetched via HTTPS
Resource: https://www.virustotal.com/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: Cisa
Feed is Active
File will be fetched via HTTPS
Resource: https://www.cisa.gov/topics/cyber-threats-and-advisories/information-sharing/automated-indicator-sha...
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: googlesafebrowsing
Feed is Active
File will be fetched via HTTPS
Resource: https://safebrowsing.google.com/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: spamhaus
Feed is Active
File will be fetched via HTTPS
Resource: https://www.spamhaus.org/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: abuse.ch
Feed is Active
File will be fetched via HTTPS
Resource: https://abuse.ch/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: virusshare
Feed is Active
File will be fetched via HTTPS
Resource: https://virusshare.com/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: talos
Feed is Active
File will be fetched via HTTP
Resource: http://www.talosintelligence.com/documents/ip-blacklist
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: sslbl
Feed is Active
File will be fetched via HTTPS
Resource: https://sslbl.abuse.ch/blacklist/sslipblacklist.csv
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: cybercrime
Feed is Active
File will be fetched via HTTPS
Resource: https://cybercrime-tracker.net/ccamlist.php
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: reputation
Feed is Active
File will be fetched via HTTP
Resource: http://reputation.alienvault.com/reputation.data
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: ipspamlist
Feed is Active
File will be fetched via HTTP
Resource: http://www.ipspamlist.com/public_feeds.csv
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: botvrij
Feed is Active
File will be fetched via HTTPS
Resource: https://www.botvrij.eu/data/ioclist.hostname.raw
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: Known_bad_IPs
Feed is Active
File will be fetched via HTTPS
Resource: https://www.misp-project.org/feeds/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: github-blocklist
Feed is Active
File will be fetched via HTTPS
Resource: https://github.com/firehol/blocklist-ipsets
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: feodo_tracker
Feed is Active
File will be fetched via HTTPS
Resource: https://feodotracker.abuse.ch/downloads/ipblocklist_recommended.txt
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: emerging_threats
Feed is Active
File will be fetched via HTTP
Resource: http://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: test-feed
Feed is Active
File will be fetched via HTTPS
Resource: https://csp.infoblox.com/
Action: Detect
User Name:
Feed is centrally managed
Total number of feeds: 26
Active feeds: 26
[Expert@azurefw:0]#
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Forgot to mention the most important one...duh : - )
Andy
secureupdates.checkpoint.com/IP-list/TOR.txt
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bro,
I understand that to work this feature we need AV/AB enabled, right?
If you have the active blades, you can ‘create’ an indicator with a list that is in a custom .csv extension and that works based on manual IPs that are added?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you need either av or ab enabled. Thats right, .csv extension file works, no issues.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does the .csv file have to have a particular structure to work properly?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
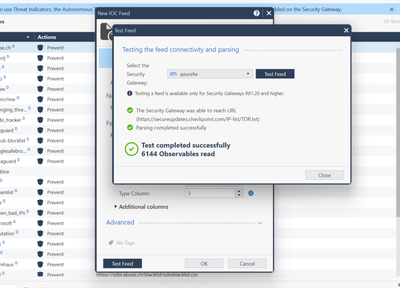
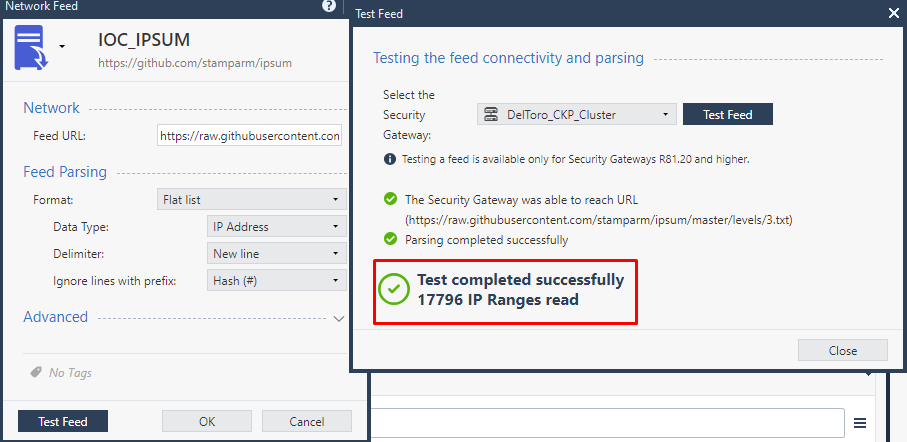
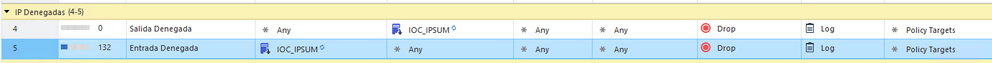
Hello mates, I usually use the following open source project:
https://github.com/stamparm/ipsum
It sumarice malicious IP between different lists. It create lists based on the ocurrence of the IP and categorice en levels.
I have configured this IOC in my lab and it's working fine. The level 3 list has over 17K malicious IPs. From R81.20, the way of using network feeds in the access control policy, for me it is more granular.
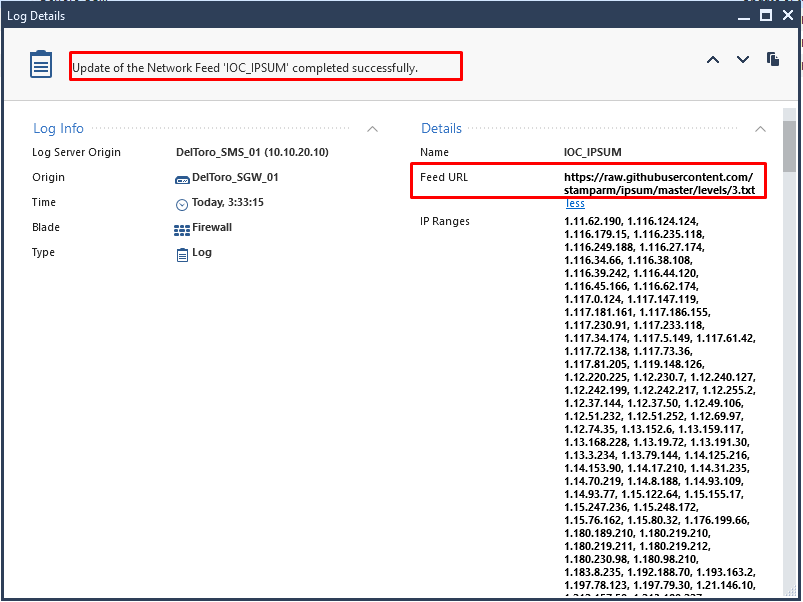
Best regards! 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wow, nice one! Let me test it in the lab later and report back.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just installed policy, so let me give it some time to see if there any hits. Though its just a lab, but it is in Azure, so Im sure it will get some traffic : - )
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Btw, I see the same link but level 2 has almost 35K IP addresses, that is fantastic, thanks for sharing!
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No problem ;). I detect that lvl 1 has some false positives, IP addresses from onedrive or sharepoint service that are legit. For me, the lvl 3 is OK, because the IP must appear at least in 3 lists.
@the_rock , of course, thanks for sharing a lot of materials and resources for IOC. 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
well thank you!!
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
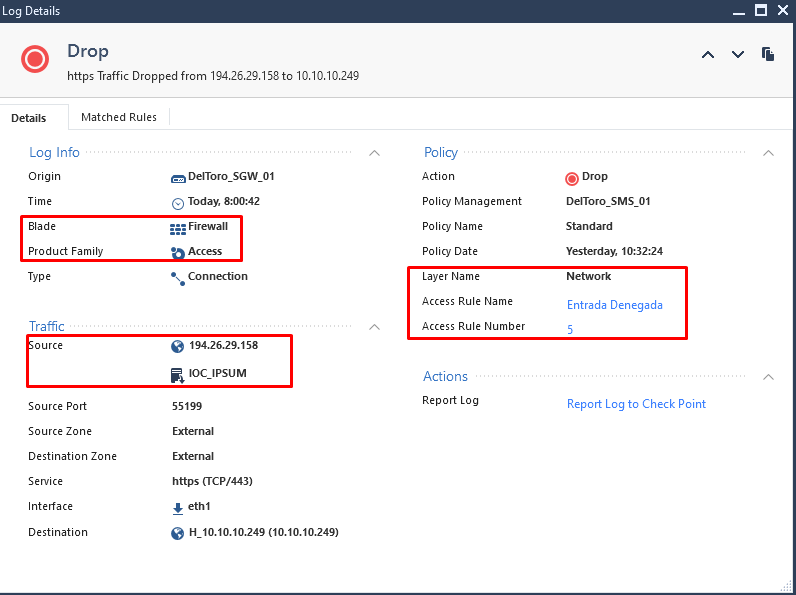
The IPsum (lvl3) seems to be the most effective so far. We've dropped over 750 connections since I added it this morning. No one internally has tried to reach out though, so that's good.
The Emerging Threats one also has had a good amount of hits.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agree, same here!
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see that when using network feeds, you dont technically need to have av or ab blades enabled, so thats definitely a plus right there and works beautifully.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What do you mean level 1, sorry?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In reference to the IOC feed: https://github.com/stamparm/ipsum
Level 1:
https://raw.githubusercontent.com/stamparm/ipsum/master/levels/1.txt
Level 3:
https://raw.githubusercontent.com/stamparm/ipsum/master/levels/3.txt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Duh, sorry, my apologies, did not clue in lol
Yes, I tried all of them, no issues.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For me the best is LVL 3, in the past i had some problems with LVL 1 because was bloking some IP from Office 365 and serveral things did not working.
In terms of performance, I had not any issue.
BR
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What could be the impact of this level 3 feed at the resource level?
Is this feed injected like the iocs_feeds directly into the antivirus blade or do locally loaded iocs work better in terms of performance?
We have a cluster that has suffered a lot from CPU issues so I would be concerned that it will affect us even more.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you're using R81.20 or above, the performance of ioc_feeds will be better since it uses the same infrastructure as Network Feeds, which is designed to handle at least 2 million IoCs.
IOC feeds
Hey boys and girls,
Happy Friday and weekend 🙂
Just figured would share some IOC feeds I put together in my lab, I counted and there is about 2000 known bad IPs that are blocked via all of them together, so hopefully it can help others.
If anyone has any others to share, please do so. FYI, you do need either AV or AB blades enabled to use IOC feeds and for best results, I recommend R81.20 version, as it also lets you test the feeds from smart console.
I truly believe everyone should do this method, as lets be honest, with ever evolving threats from the Internet, who has the time to manually keep updating bad IPs to be blocked? I will take a wild guess and say probably no one lol
Best,
Andy
[Expert@azurefw:0]# ioc_feeds show
Feed Name: talos_1
Feed is Active
File will be fetched via HTTPS
Resource: https://www.talosintelligence.com/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: sans
Feed is Active
File will be fetched via HTTPS
Resource: https://isc.sans.edu/
Action: Prevent
User Name:
Feed is centrally managed
Feed Name: isacs
Feed is Active
File will be fetched via HTTPS
Resource: https://www.nationalisacs.org/
Action: Prevent
User Name:
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 43 | |
| 26 | |
| 14 | |
| 12 | |
| 11 | |
| 8 | |
| 7 | |
| 6 | |
| 6 | |
| 6 |
Upcoming Events
Thu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter