- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Discover the Future of Cyber Security:
What’s New in Check Point’s Quantum R82
Pick the Best of the Best of
CheckMates 2024!
Share your Cyber Security Insights
On-Stage at CPX 2025
Simplifying Zero Trust Security
with Infinity Identity!
Zero Trust Implementation
Help us with the Short-Term Roadmap
CheckMates Go:
What's New in R82
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Re: IKEV1 VPN with AWS Peer (Non VTI) - Incoming t...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IKEV1 VPN with AWS Peer (Non VTI) - Incoming traffic stop working randomly after P2 renegotation
We have a VPN set up against AWS. Normally in this VPN the traffic is bidirectional, but we have noticed that randomly the traffic that is originated from the peer does not arrive or stops passing through the VPN after a P2 renegotiation and begins to arrive when the P2 is renegotiated again. In other words, if P2 was renegotiated at 1:30 p.m., the 3600 second timer expires, and it is regenerated at 2:30 p.m., here it starts working again.
When the traffic stops passing, in our firewall we see these logs:
Log1:
Id: 0abf0bd2-1dcc-2726-64f8-ca1ecb4a022c
Marker: @A@@B@1694024864@C@11152905
Log Server Origin: 10.191.11.210
Time: 2023-09-06T18:51:10Z
Interface Direction: inbound
Interface Name: daemon
Id Generated By Indexer:false
First: true
Sequence number: 225
Source: 34.195.30.101
IP Protocol: 0
Destination Port: 0
Encryption Failure: Unknown SPI: 0x5a4211c for IPsec packet.
VPN Peer Gateway: 34.195.30.101
Scheme: IKE
VPN Feature: IKE
Action: Drop
Type: Log
Blade:VPN
Origin: FW_GPRS_DURAN
Service: 0/0
Access Rule Number: 0
Interface: daemon
Description:
Log2:
Id: 0abf0bd2-1d4c-2726-64f8-ca78a54f004c
Marker: @A@@B@1694024864@C@11863241
Log Server Origin: 10.191.11.210
Time: 2023-09-06T18:52:40Z
Interface Direction: inbound
Interface Name: bond10.644
Id Generated By Indexer:false
First: true
Sequence number: 43
LogID: 404840
Source: 34.195.30.101
Destination: 190.111.65.126
IP Protocol: 50
Encryption Fail Reason: Packet is dropped because an IPsec SA associated with the SPI on the received IPsec packet could not be found
Member ID: 1_11
Action: Drop
Type: Connection
Policy Name: ClusterGPRSDuran_Ckp
Policy Management: Manager64k
DB Tag: {848FD104-DE25-9944-BC90-38D724932081}
Policy Date: 2023-09-05T20:22:13Z
Blade: Firewall
Origin: FW_GPRS_DURAN
Service: 50
Product Family: Access
Logid: 1
Interface: bond10.644
Description: ESP Traffic Dropped from 34.195.30.101 to 190.111.65.126
The strange thing is that if I go to see the SPIs with the VPN TU command, the gateway does have them registered.
Our enviroment is 64000 chassis R81.10 JHF take 109.
L4 distribution mode enabled.
I attached the evidence here.
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When did this start happening?
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good question. The problem started exactly after I upgraded the chassis from R80.20SP to R81.10 JHF take 109.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you send output of below from CP?
vpn tu tlist -p peer_ip (just replace peer_ip with aws IP address)
Btw, does anything change if you reset the tunnel on both ends?
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The output of that command during the failure is attached here in this post, it is called "vpn your tlist".
If the VPN is restarted from either end it starts working again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right, sorry, my bad. In that case, I would open TAC case and see what they say. Personally, easy debug you can do yourself.
Andy
vpn debug trunc
vpn debug ikeon
-generate some traffic
vpn debug ikeoff
Get ike.elg and vpnd.elg from $FWDIRlog dir
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I ALREADY have a case open but I still don't have an answer. In the debugs it practically says the same as the logs.
messages like that:
W_GPRS_DURAN-ch01-11[5 Sep 15:31:04][tunnel] RequestBySPI: no match for spi b5b53723, owner 7f000001, peer 101.30.195.34 - will send Delete PL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
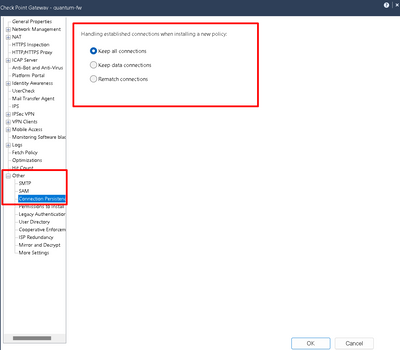
I dug through my old notes way back when I was helping someone with this, probably back from R65 days (I know, I know, there was no aws then haha), BUT...it was between CP and Cisco, literally same issue and we fixed it by enabling option to "keep all connections" under connections persistence on gateway properties and also "keep ike SAs" under global properties (advanced at the bottom and then vpn somewhere).
I dont have access to smart console right now, but can log in if you want me to find options Im referring to. Just watching "Jeopardy", nothing too exciting lol
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Keep ike sas is already activated, I will check the other option. Thanks for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Will log in and send a screenshot, give me 5 mins.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I already have this option enable. I have noticed that the initiator of the negotiations is always AWS. I have lowered the phase 2 timer on my side from 1 hour to 45 minutes, so far it has negotiated twice and now the Check Point side is starting renegotiations.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats one option in case like this. I checked an official SK for tunnel config to aws and shows phase 1 420 mins and phase 2 3600 seconds.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello.
Do these commands work for both IKEv1 and IKEv2?
In IKEv2, it is the same file to extract, for review?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes bro, its the same.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 29 | |
| 22 | |
| 19 | |
| 12 | |
| 11 | |
| 9 | |
| 9 | |
| 8 | |
| 6 | |
| 6 |
Upcoming Events
Mon 25 Nov 2024 @ 02:00 PM (EST)
(Americas) AI Series Part 3: Maximizing AI to Drive Growth and EfficiencyTue 26 Nov 2024 @ 10:00 AM (CET)
EMEA Session: Automated Collaborative Prevention with 3rd Party Endpoint SolutionsTue 26 Nov 2024 @ 03:00 PM (CET)
Navigating NIS2: Practical Steps for Aligning Security and ComplianceTue 26 Nov 2024 @ 05:00 PM (CET)
Discover the Future of Cyber Security: What’s New in Check Point’s Quantum R82Tue 03 Dec 2024 @ 10:00 AM (GMT)
UK Community CNAPP Training Day 1: Cloud Risk Management WorkshopTue 03 Dec 2024 @ 05:00 PM (CET)
Americas CM Session: Automated Collaborative Prevention with 3rd Party Endpoint SolutionsMon 25 Nov 2024 @ 02:00 PM (EST)
(Americas) AI Series Part 3: Maximizing AI to Drive Growth and EfficiencyTue 26 Nov 2024 @ 10:00 AM (CET)
EMEA Session: Automated Collaborative Prevention with 3rd Party Endpoint SolutionsTue 26 Nov 2024 @ 03:00 PM (CET)
Navigating NIS2: Practical Steps for Aligning Security and ComplianceTue 26 Nov 2024 @ 05:00 PM (CET)
Discover the Future of Cyber Security: What’s New in Check Point’s Quantum R82Tue 03 Dec 2024 @ 05:00 PM (CET)
Americas CM Session: Automated Collaborative Prevention with 3rd Party Endpoint SolutionsTue 03 Dec 2024 @ 10:00 AM (GMT)
UK Community CNAPP Training Day 1: Cloud Risk Management WorkshopWed 04 Dec 2024 @ 10:00 AM (GMT)
UK Community CNAPP Training Day 2: Cloud Risk Management WorkshopAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter