Hello everyone!
I have an issue with some SmartEvent reports on a firewall that is operating in bridge mode, in standalone operation mode and with R81.10 JHF 79 GA.
The model of the firewall is a 5600 which basically has the following on its interfaces:
*Mmgt interface - for firewall management.
*Bridge interface composed by interface eth1 (for inbound traffic) and eth2 (for outbound traffic) [defining eth1 as internal interface and eth2 as external interface in anti-spoofing].
The source traffic comes from a corporate office and sends the traffic to a Backup as a Service provider, this is the traffic that passes through the bridge interfaces. Basically a bridge for a "LAN" type network.
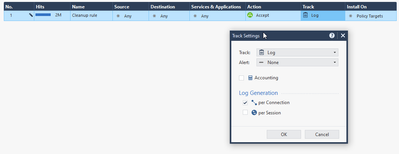
I am trying to generate some SmartEvent reports such as "Network Activity", "Threat Prevention" or any other type of report, however when I put the report for the last 7 days, 24 hours or any time range, the reports do not contain any information and generate empty reports.
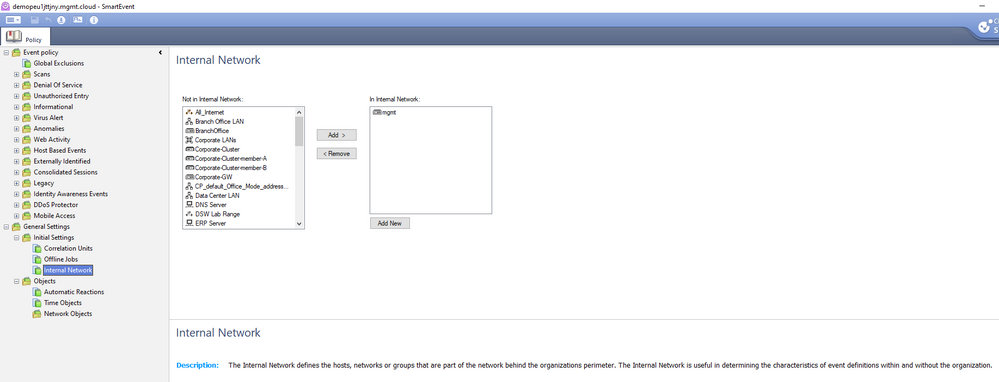
In the firewall I have the Monitoring (advanced networking) blades, SmartEvent Server, SmartEvent Correlation Unit and log indexing is enabled.
I tried to turn off the mentioned blades and turn them on again, installing database and policies, I stopped the smartevent services in CLI with evstop, evstart, but in none of these tests I got any difference or any result in the reports.
I have even run a cpstop, cpstart and I haven't seen any results in the SmartEvent reports either.
The strange thing is that I can see the logs of the connections that pass through the firewall without any problem, I see traffic through the br1 with a tcpdump by CLI, I don't see any traffic dropped by "fw ctl zdebug + drop", I have an accept any-any rule, but still, I don't see any results in the reports.
Has anyone had something similar happen? or any idea?
Greetings to all!