- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: HowTo Set Up Certificate Based VPNs with Check...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HowTo Set Up Certificate Based VPNs with Check Point Appliances - R77 edition
Preface
Securing virtual private networks (VPNs) in enterprise Site-to-Site environments is an important task for keeping the trusted network and data protected. Also it's critical to avoid any loss of data sovereignty.
When it comes to VPN security many security experts first think of encryption algorithms, perfect forward secrecy (PFS), Diffie-Hellman groups... and a long pre-shared key (PSK). Ouch!
What about VPN certificates?
Every security expert knows how much better certificates are for gaining high security levels. Therefore certificates are always best practice in enterprise grade security environments.
However, most VPN Site-to-site setups are still based on simple, long lasting pre-shared keys. In many cases these keys were even forgotten by the administrators in charge of keeping the network secure because once configured for the VPN tunnel they are not needed anymore.
This is because it's much quicker and really easy to set up a VPN with a simple pre-shared key than having to deal with certificates and a certificate authority (CA).
But is it really that hard to implement a way better security architecture based on certificates? This article shows how simple it can be when you work with Check Point Firewall & VPN security gateways.
So let's get started!
When working with VPN tunnels between Check Point gateways there is absolutely no reason not to use VPN certificates.
Setup:
Management : Check Point SmartCenter
Gateway : Check Point Firewall & VPN
Remote Office : Check Point 1100 Appliance
Centrally managed
Check Point is well-known for its superior security management solution to which all Check Point gateways are connected. This central management approach makes it so easy to deploy security settings to all connected gateways with a single click on policy installation.
Check Point's security management is called SmartCenter Server (or Multi-Domain Security Management) and has an internal certificate authority built-in. This InternalCA enables the global use of certificates between all connected components and gateways right out-of-the-box.
Check Point automatically generates certificates when a new Check Point object is created, so you don't have to take of certificate handling. Check Point does it all for you.
Establishing a certificate based VPN in centrally managed Check Point environments is as easy as 1-2-3.
First, create a VPN community for certificate based VPNs (Mesh or Star topology)
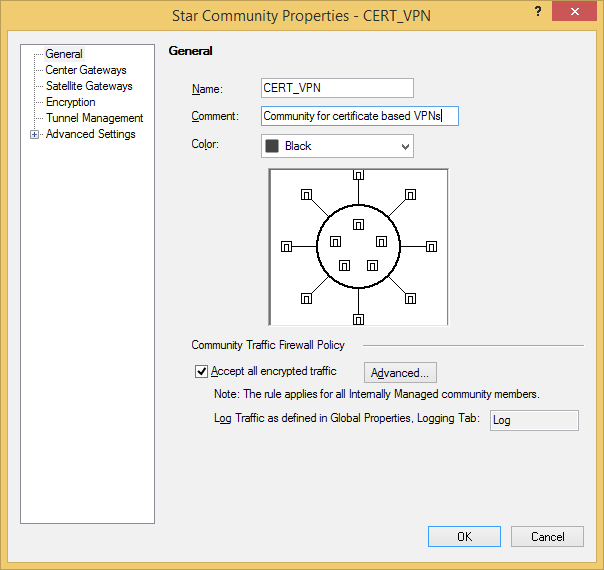
Configure your preferred VPN encryption settings for Phase 1 (IKE) and Phase 2 (IPsec).
We'll be using a permanent VPN tunnel here, because the Remote Office is a dynamically assigned IP address (DAIP) gateway. Therefore, when it's IP address changes it will automatically re-establish the VPN tunnel. Cool feature, isn't it?
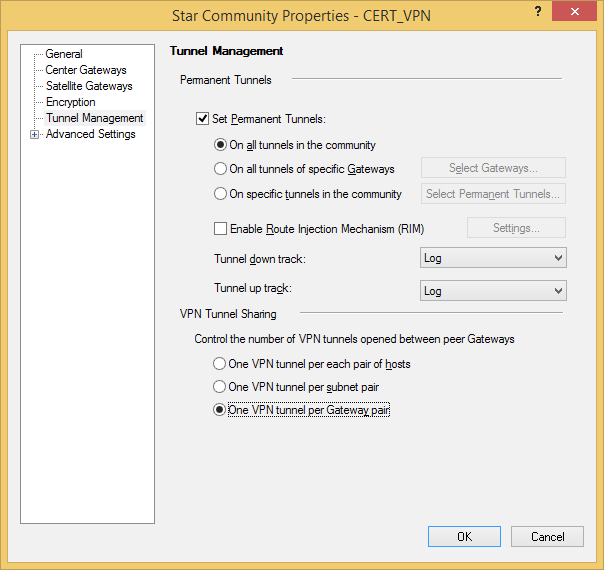
Leave the checkbox for pre-shared keys unchecked!
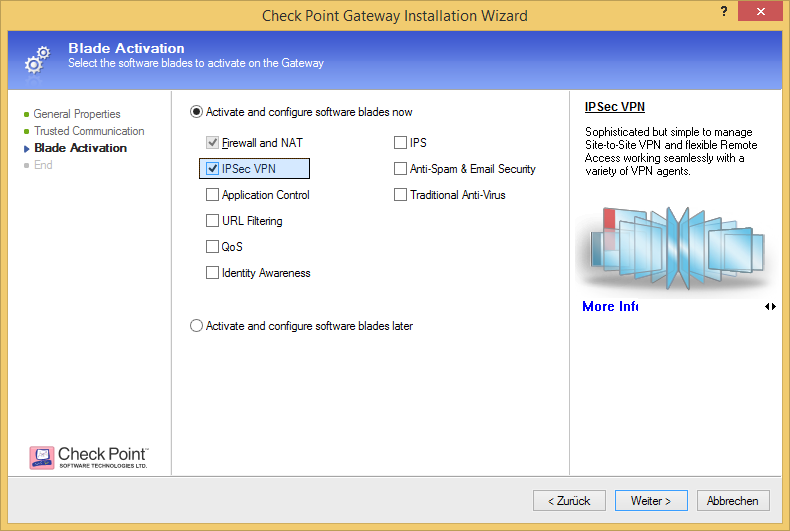
Activate IPsec VPN on your participant gateways if it isn't already.
Choose your VPN community..
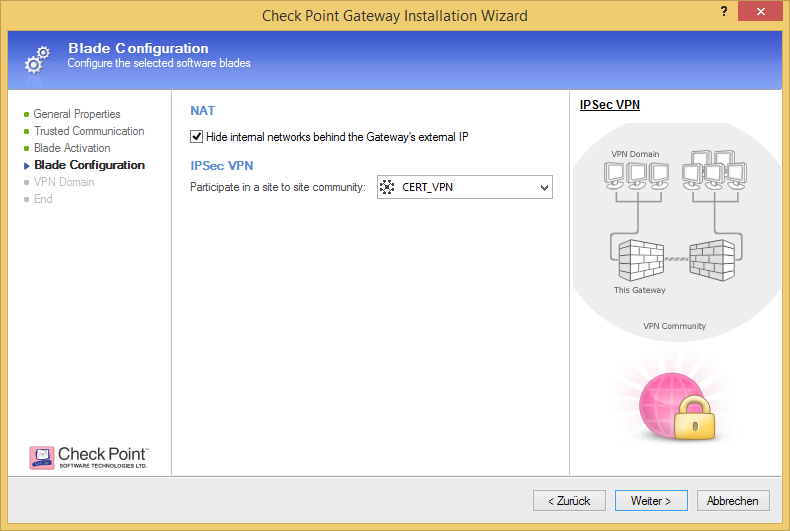
..and select the VPN encryption domain of the specific gateway.
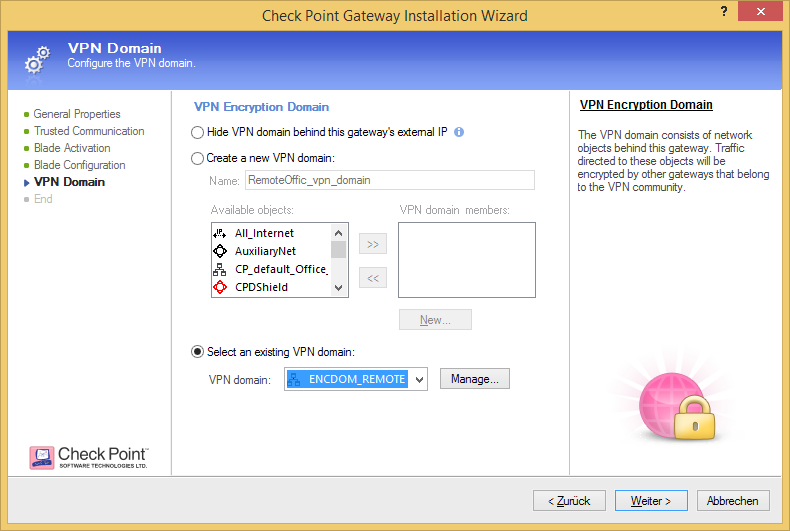
Please note that you can either configure the VPN topology in wizard mode when creating a new Check Point object or in classic mode when the gateway object is already existing. Depending on where you configure it your graphics might look a bit different to the screen shots used here.
Verify your VPN certificate and IPsec VPN community.
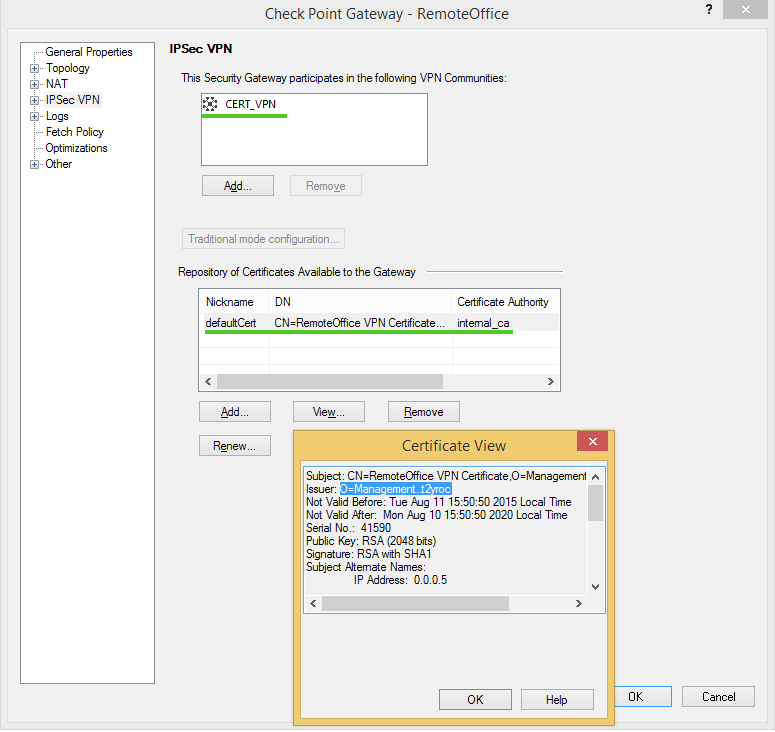
After you have configured the VPN topology for your VPN gateways you should add them to your VPN community.
Add your VPN gateways to your VPN community.
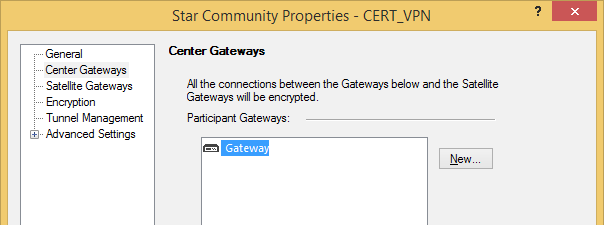
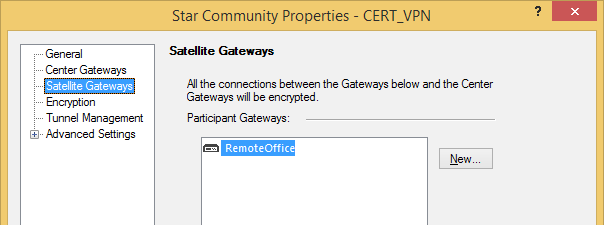
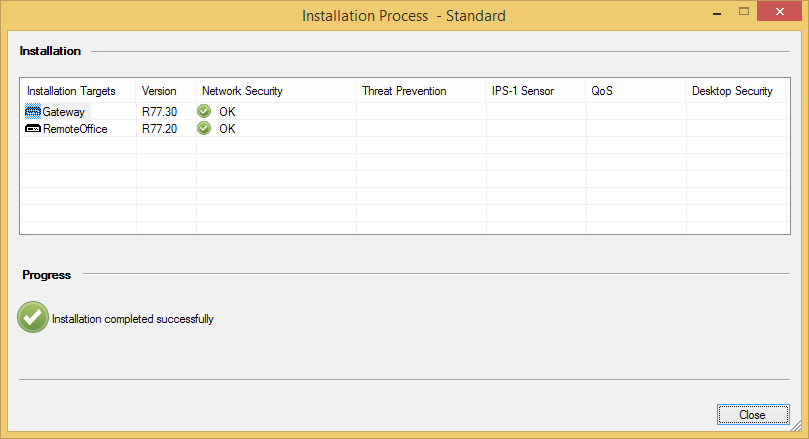
Finally, install the security policy.
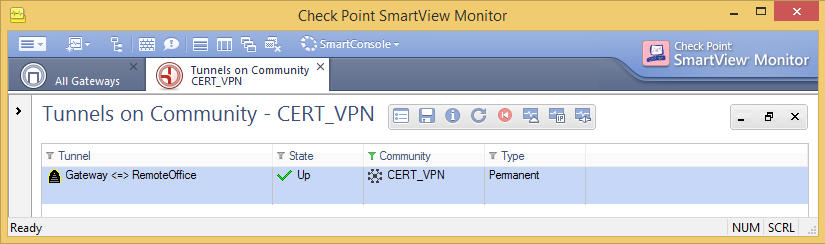
The certificate based VPN tunnel is now up an working!
Externally managed
Other companies love Check Point, too! They have their own SmartCenter Server (or Multi-Domain Security Management) as central Check Point security management.
To configure a certificate based VPN tunnel with their VPN gateway you just need to exchange certificates!
Let's go!
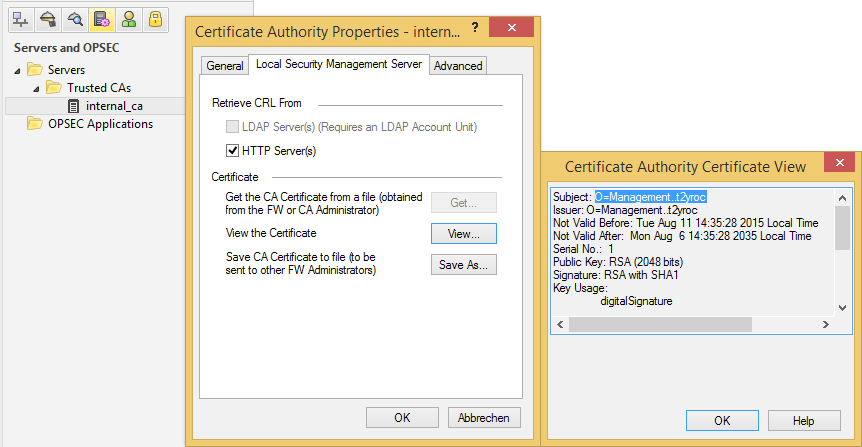
Navigate to Manage > Servers and OPSEC Applications... > internal_ca > Edit... > Local Security Management Server > Save As... and export your CA certificate in order to send it to the firewall administrators of that other company. Tell them to send you theirs as well.
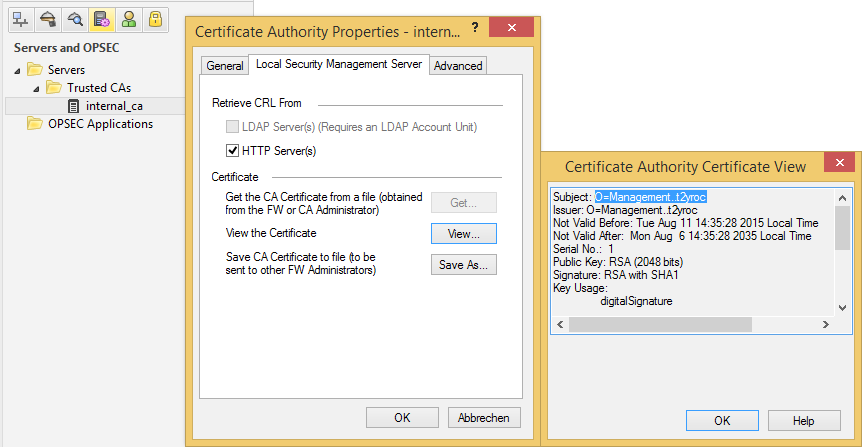
Import their CA certificate via Manage > Servers and OPSEC Applications... > New > CA > Trusted select External Check Point CA and open the tab External Check Point CA
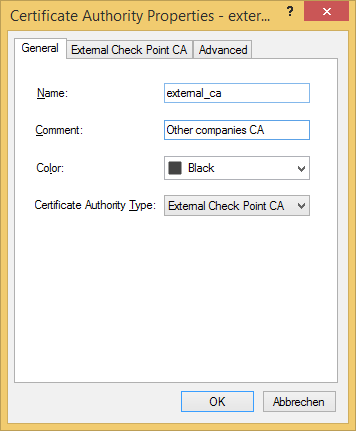
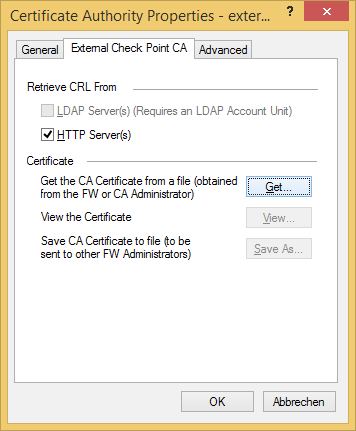
Import their CA certificate and confirm with OK.
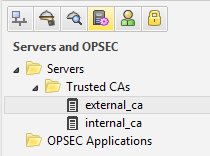
Now you have two Trusted CA certificates that you can use for your VPN setup.
Create a new Check Point Externally Managed VPN Gateway... and configure your certificate based VPN according centrally managed VPNs.
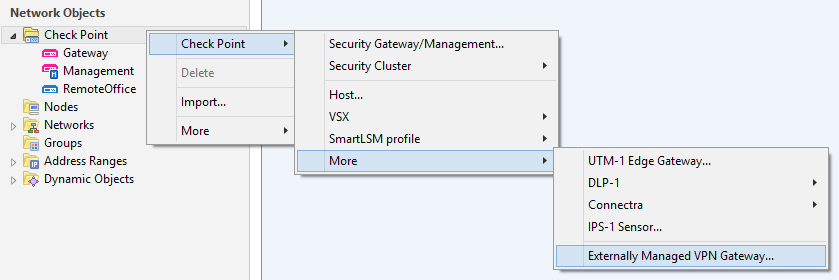
Select their CA certificate as Matching Criteria for your IPSec VPN setup.
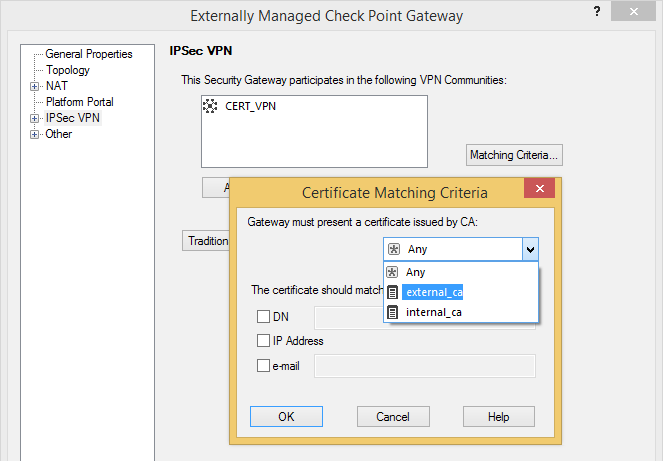
In case the Externally Managed VPN Gateway is a dynamically assigned IP address (DAIP) gateway make sure CRL checking works and the VPN tunnel is configured to be permanent. Check that your gateway can reach the CRL distribution points (check if DNS resolving is required), CRL retrieval via HTTP and CRL Caching is checked and enter the correct DN for their VPN certificate! (i.e. the DN of their defaultCert as shown under IPSec VPN of their Check Point Gateway object)
Locally managed
Check Point's 700 appliances are locally managed. So can be 1100 / 1400 appliances.
Check Point 1400 Appliance FAQ
Using the same technique as described for externally managed Check Point gateways won't work as 600/1100 appliance don't have a SmartCenter server running. Still, these SMB appliances have their own local CA!
Check Point's SecureKnowledge article sk94028 describes the correct procedure.
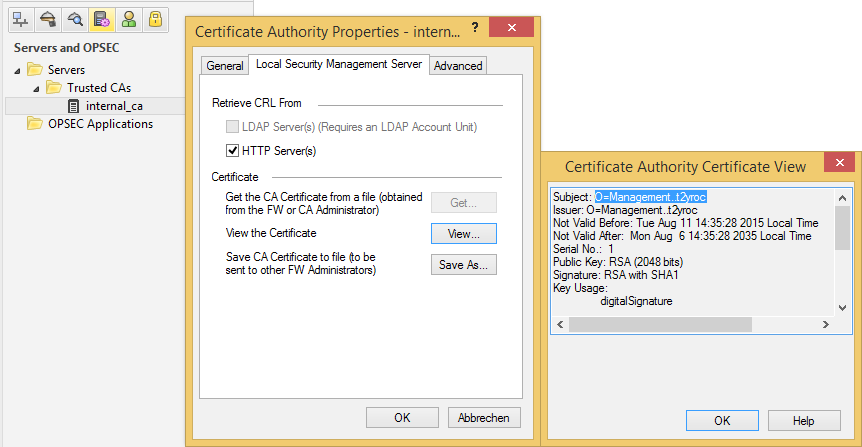
First, let's export our InternalCA to the 1100 / 1400 appliance at our remote office.
In SmartDashboard just navigate to Manage > Servers and OPSEC Applications... > internal_ca > Edit... > Local Security Management Server > Save As... and export the certificate.
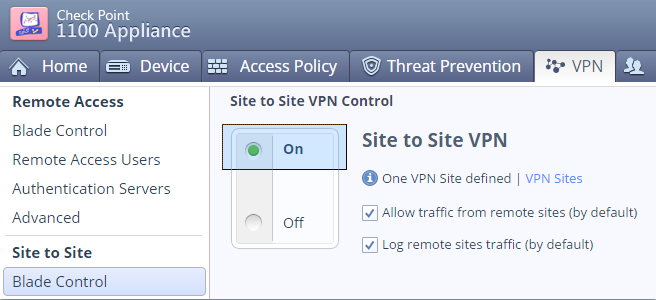
Verify that the locally managed SMB appliance has Site-to-Site VPN enabled.
Import the internal_ca.crt file to your locally managed SMB appliance.
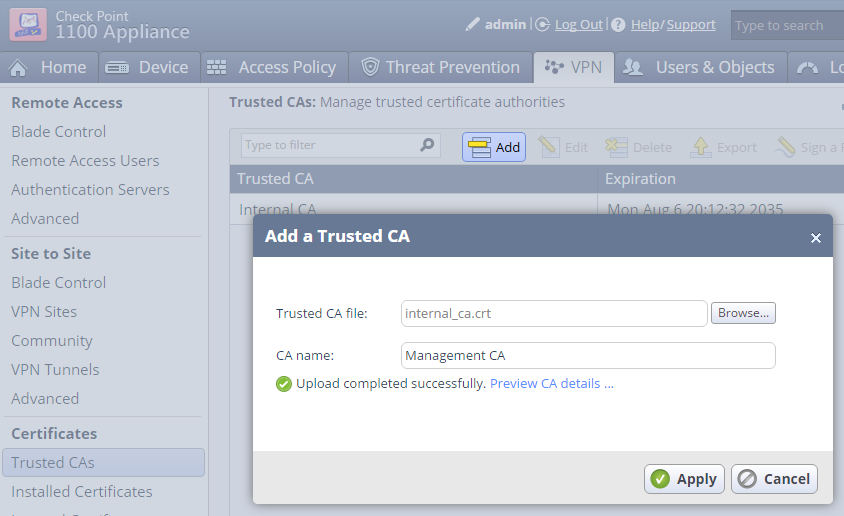
You may want to disable CRL checking if your Management as primary CRL Distribution Point can't be reached or isn't resolvable. In an ideal world this shouldn't be required.
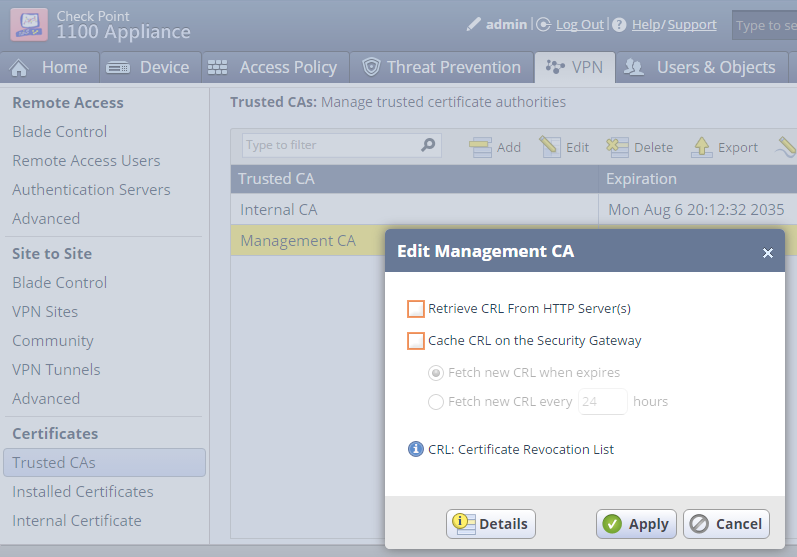
sk94028 details the CRL verification mechanism of Check Point's SMB appliances.
Easy, isn't it? Now we want to export the SMB appliance's certificate to our Management or (if you prefer) issue a certificate request to be signed by our Managements Internal_CA.
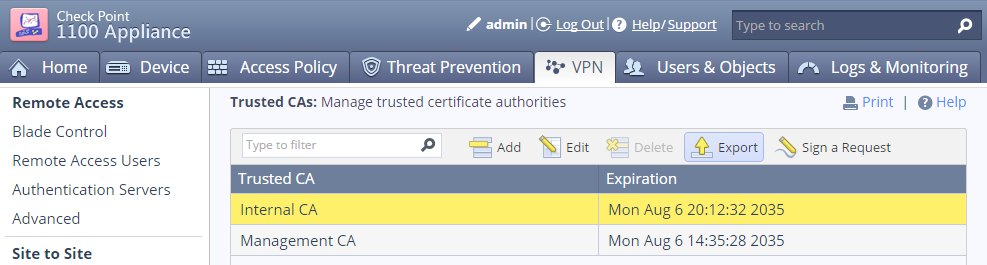
Option A - Export the SMB appliance's certificate
Highlight the Internal CA of our SMB appliance (NOT the one we just imported), then click "Export" and save the file.
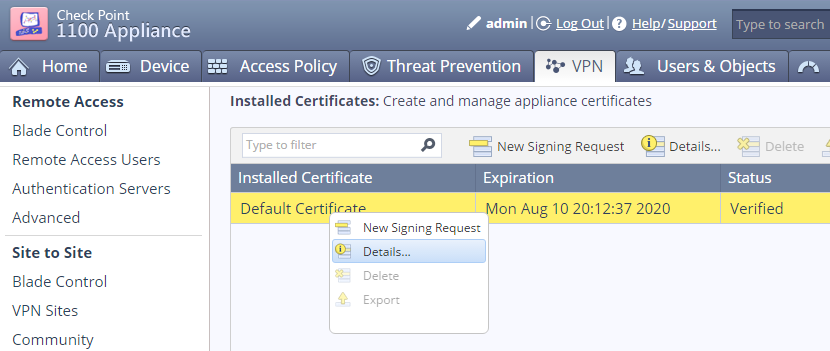
Go to VPN > Certificates > Installed Certificates and open the Details of the Default Certificate.
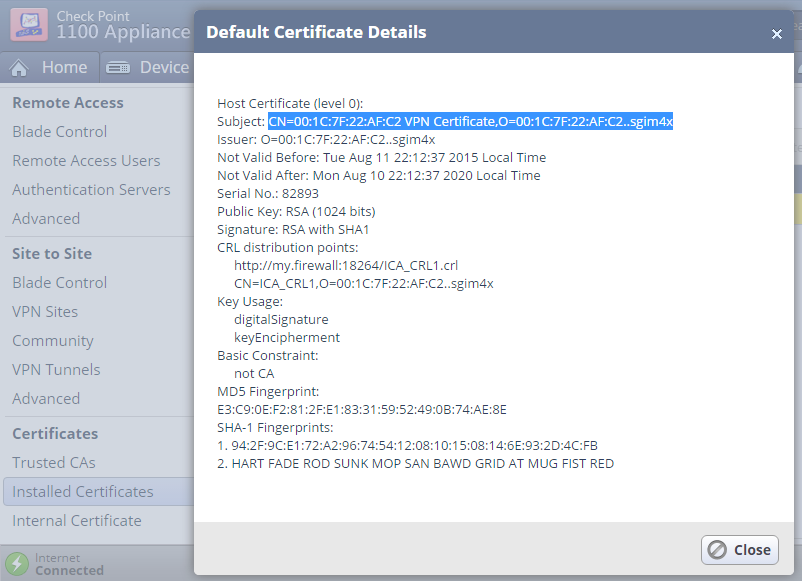
Copy the Subject of the Default Certificate.
Create a VPN Site for the certificate based VPN tunnel to our VPN Gateway.
Configure the VPN site to use Certificate authentication.
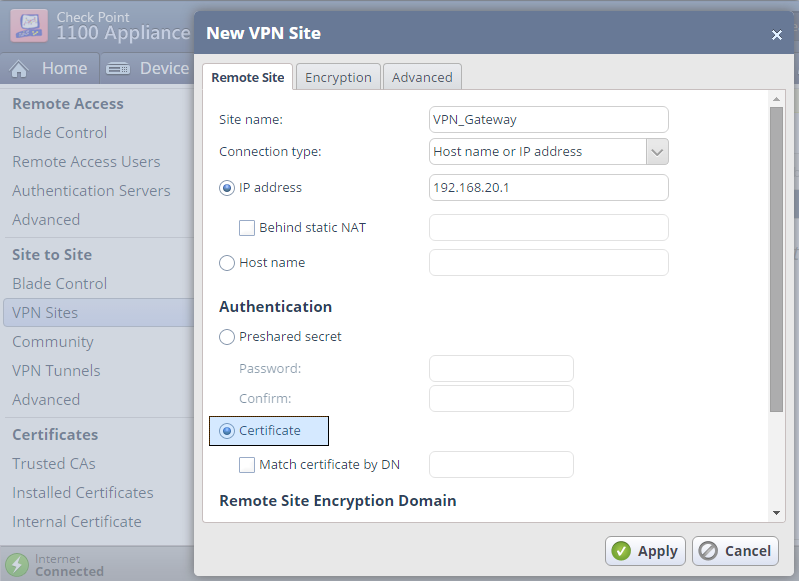
In the Advanced tab > Certificate Matching set the "Remote Site Certificate should be issued by" to our Management Trusted CA's Name.
We are now finalizing our way cool VPN setup in SmartDashboard on our Management.
Navigate to Manage > Servers and OPSEC Applications... > New > CA > Trusted select OPSEC PKI and open the tab OPSEC PKI to import our saved SMB Internal CA file.
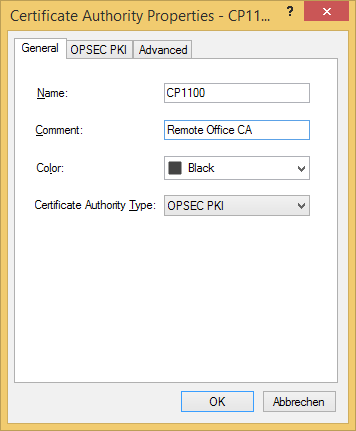
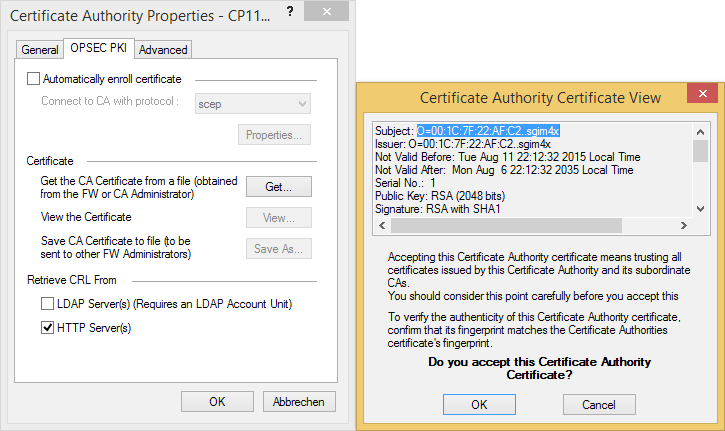
Again, you may want to disable CRL checking if required.
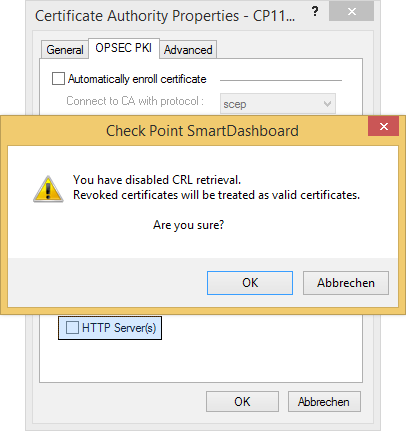
You'll then find our imported SMB certificate 'CP1100' next to our internal_ca within the Trusted CAs list of our Management.
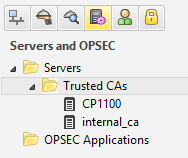
Option B - Issue a certificate request
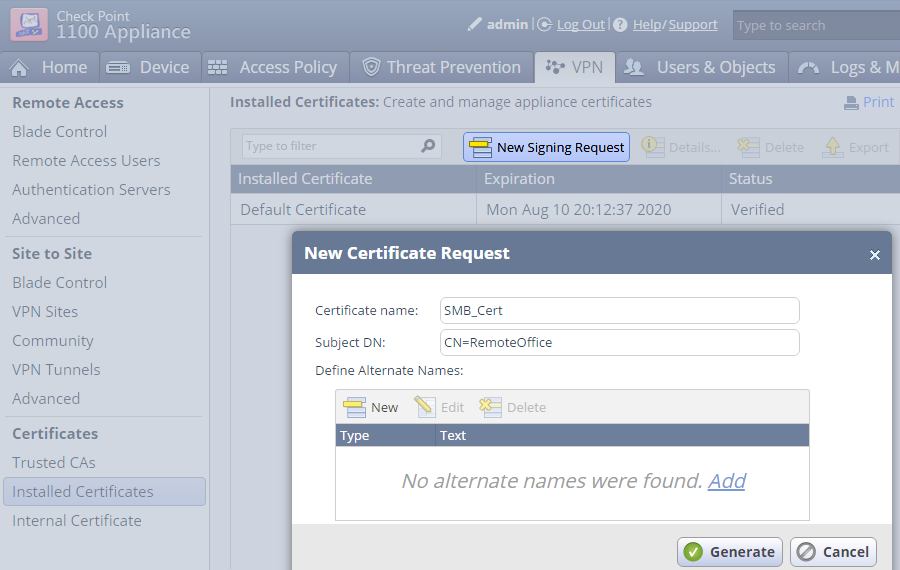
Go to VPN > Certificates > Installed Certificates and click New Signing Request to generate a new certificate.
Enter a Certificate name and Subject DN.
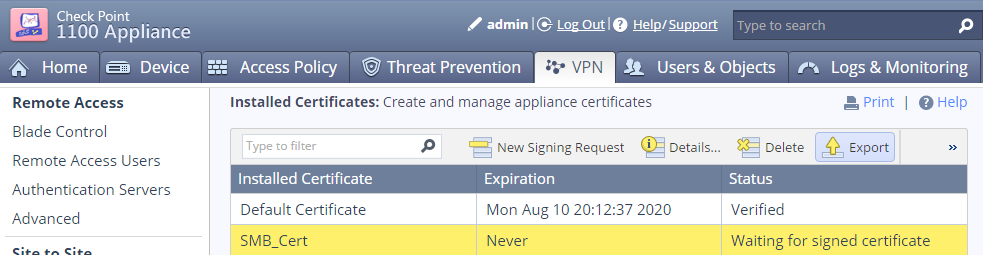
Export the Signing Request to a file
Copy the contents of the exported file
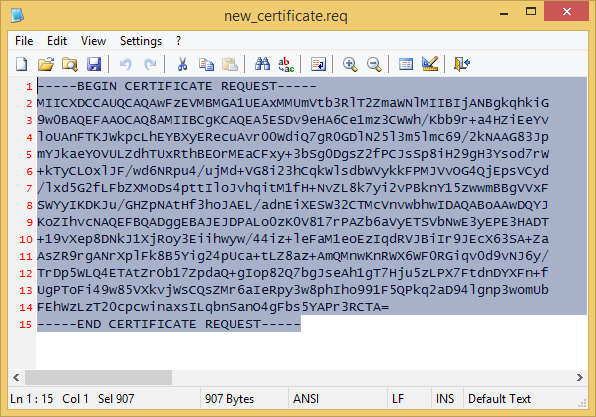
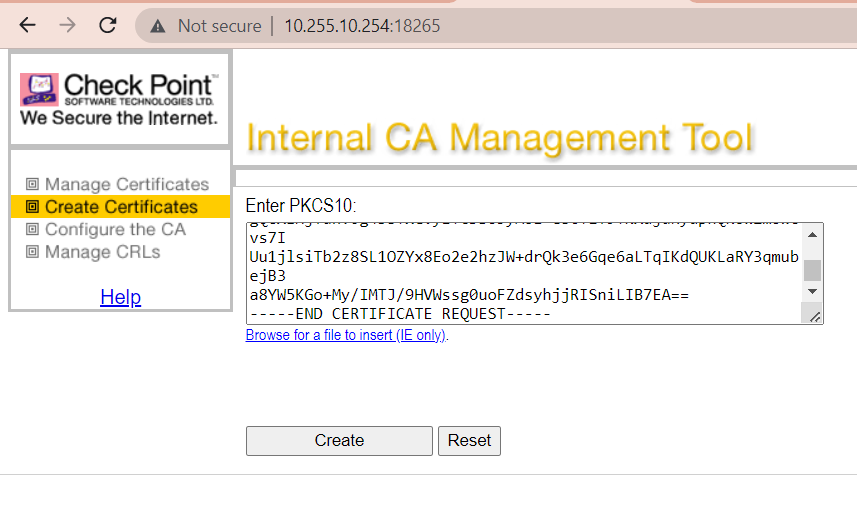
On the Management start the ICA Management Tool (sk39915), go to Certificate Creation and paste the certificate request into the PKCS#10 text box.
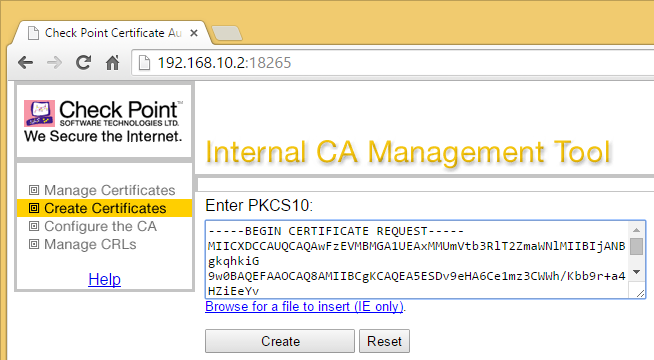
Create the signed certificate.
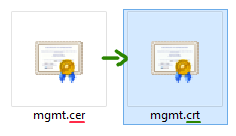
If required change the filename extension of the created certificate to .crt
On the SMB appliance Upload the Signed Certificate and Complete.
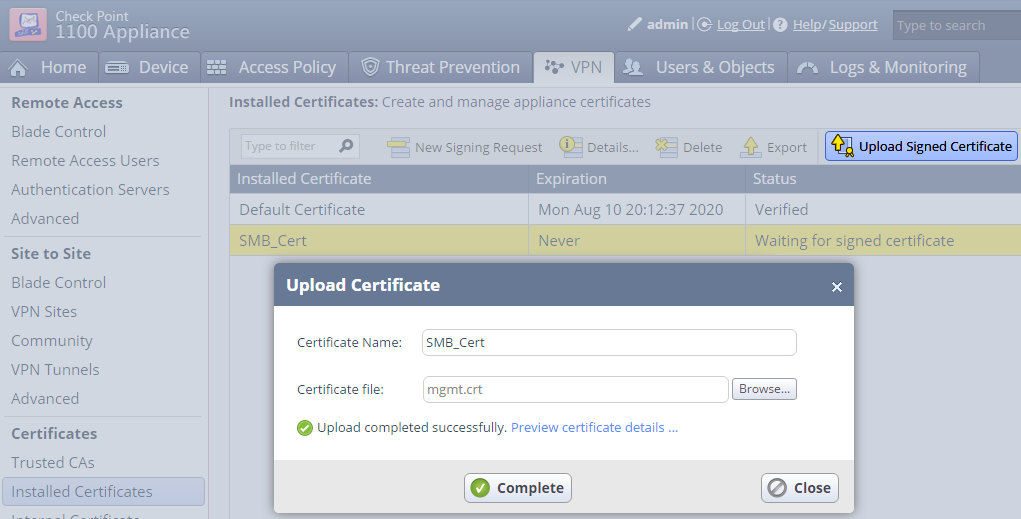
End of Option B
Now simply create an Externally Managed Check Point Gateway for our SMB appliance and your are all set up and done.
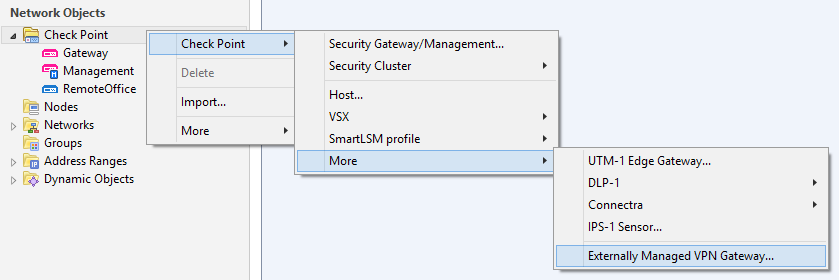
When configuring the Matching Criteria for our SMB appliance, check the DN box and paste the Subject of our SMB appliances Default Certificate if you took Option A.
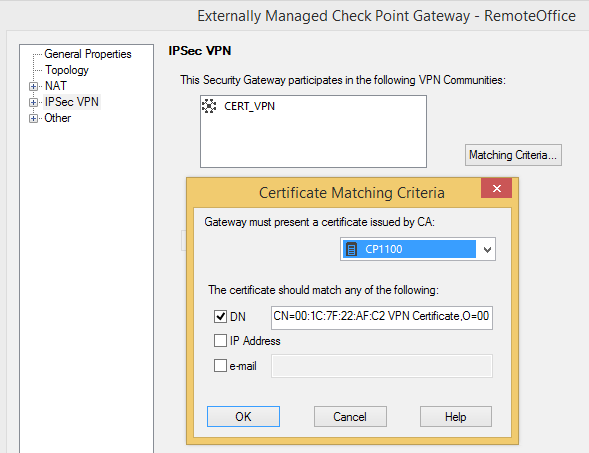
In case of Option B first copy the DN of the created Certificate from within ICA Management Tool
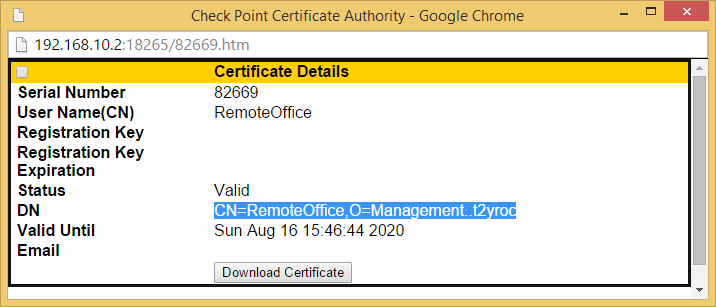
then paste it into the DN field of the VPN certificate as issued by our internal_ca.
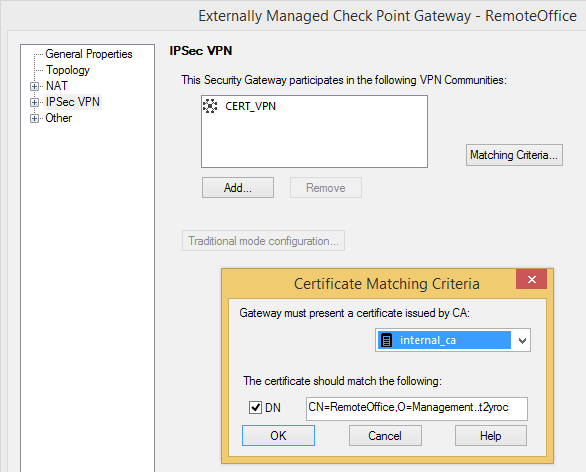
Install the security policy.
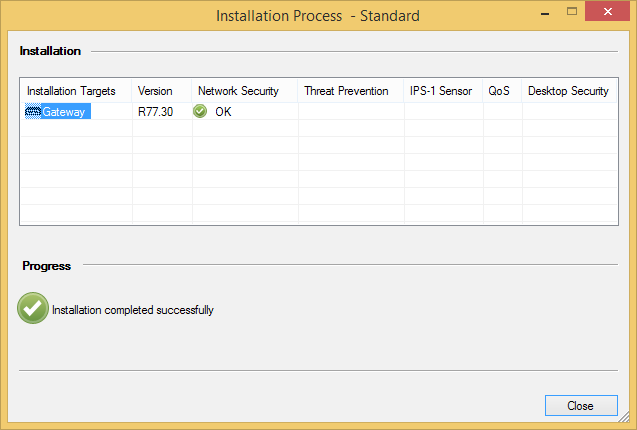
And check out the working VPN tunnel.
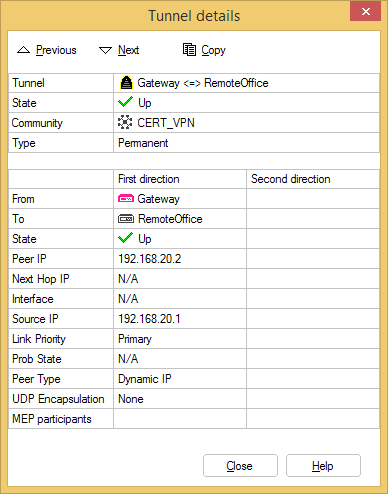
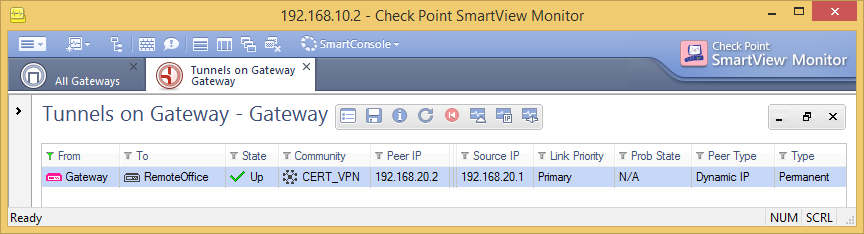
Danny Jung is passionate about VPN security and leads you through the joy of creating certificate based VPNs with Check Point appliances. Danny Jung is the Chief Technology Officer (CTO) at ESC and has been working with Check Point Firewalls for more than a decade.
Thank you.
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Danny this is a great article. I am looking to configure DAIP site to site with an external vendor with R80.10. Do you have a similar article I can copy of you. Can't find anything that tells you how to do this. Much appreciated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi Denny, Is it possible to use Certificate based VPN while negotiation with different Vendor like Cisco. I.e. "A" end Checkpiont VPN gateway and "B" end Cisco ASA firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can find that in CP Site to Site VPN Administration Guide R80.30 p.21ff !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i have Checkpoint VPN Gateway with R77.30 and the other end we have Cisco ASA firewall. Not sure if we can have Certificate based VPN to negotiate tunnel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all, has some one configured an IPSEC using a Cisco router with Dynamic IP?
I don't know if it's better create the certificate and export both (CA and the one signed) from Cisco and then importing them to CP or do reversely.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the other vpn peer is an interoperable device(3rd party device) and you need to configure the VPN with certificate based authentication, you have 2 options:
1. Use the ICA of the checkpoint. In that case, you'd need to export the internal_ca from the SMS/DMS, and import it in the other peer. Then, from the other peer you'll need to generate the CSR , copy it and sign it with the ICA mgmt tool and export the certificate and import it in the other peer and on the interoperable device object select the new certificate in the matching criteria.
2. Use an external CA for the other peer and the ICA for the CKP. In that case, you'd need to export the external_ca and the certificate from the external CA that the other peer will use. Then import them using the ICA mgmt tool and on the interoperable device object select the new certificate in the matching criteria.
There could be another option when you use and external CA for both the CKP and the interoperable device, in that case in both sides you'd need to have the root/inter ca certificate imported in the devices, also on both sides you'll need to generate a CSR and request the external CA to sign them and impor the certificates in both peers. Then import the bew certificate issued for the CKP and for the other peer using the ICA mgmt tool and on the interoperable device object select the new certificate in the matching criteria and on the CKP object add the new certificate in the IPSec VPN properties issued by the external CA.
The SK relevante for the ICA mgmt tool is: sk30501 - Setting up the ICA Management Tool
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes! It is possible to establish a vpn tunnel with cisco using certificates and having Check Point SMS as a Certification Authority, first, you need to create a Certificate signing request from cisco device, then you have to enable the ICA management tool in the Smart center server (Checkpoint Management) by connecting through command line (cpca_client set_mgmt_tool on -no-ssl), then you have to paste the CSR as PKS in Generating certificate as follow:
Then press button create and now you have a certificate for the router device, once you have the certificate of the ICA and the certificate for the cisco device you need to enroll the CA certificate first and then the certificate for the cisco device signed by ICA, from there the configuration on cisco device is pretty simple, you have to choose to authenticate using certificates in your cisco configuration.
Note: sometimes the CRL is problematic because is not possible to verify the revocation list, so disable this verification on router side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Is it possible to build a VPN with a locally managed SMB appliance while still retaining the option to send the logs to the SMS?
I can't really find it, but this seems to be mutually exclusive since logging requires SIC and therefor a regular Gateway object, but certificate matching/management for VPN requires an Externally Managed Gateway object. Is there some way to combine this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I had it and it was working
VPN Tunnel - SMB locally managed - Interoperable device
Log object - Check Point host with SIC - SMB locally managed was sending logs to my log server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've also done this.
You configure it in Logs and Monitoring > Logs > External Log Servers > Check Point Log Server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there any SK that shows how to add and configure 1575 centrally managed to SMS 81.20.
I can add it but I am not sure if DIAP is working or not, i am getting this:
Main Mode local machine configured not to respond to unknown IP addresses (i.e. not exportable for SR, and/or not included in the RemoteAccess community, and/or no DAIP's defined)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is the 1575 configured as a DAIP object?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes,
on SMB I see these logs:
I wonder why all traffic is "drop" on SMB
Logs from SMS:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you have NAT configured for your management so your remote gateway can reach it?
The message about not being able to validate the certificate would speak to this being not set properly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
NAT is active on the SMS.
We were unable to publish the SMS on our external IP address because it affected all our other VPN tunnels. When the SMS was published on the external IP, all other VPN tunnels went down as they started communicating with the SMS instead of the firewall.
We are now using a different public IP that is on the same subnet as our external IP. However, when performing SIC between the SMB and SMS, only our external IP shows up, even if we select another public IP.
I am unsure if this is correct or not!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So is the public IP that is supposed to be used configured in the object shown here?
Also, this doesn't take effect until a policy push occurs to the relevant gateways.
Also when you say "only our external IP shows up" where exactly are you referring to?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 15 | |
| 13 | |
| 10 | |
| 8 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 2 | |
| 2 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter