- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: How to disable SIP ALG inspection in a specifi...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
How to disable SIP ALG inspection in a specific rule in Checkpoint? Also Could this be done globally, like Cisco ASA?
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually I am not sure Tomer answer will work. After having been on first name bases with R&D VOIP for a year with loads of VOIP tickets in R65 I learned a lot of the background of the code. And I guess most of it is still valid.
At least in R77.30 I always use the following strategy:
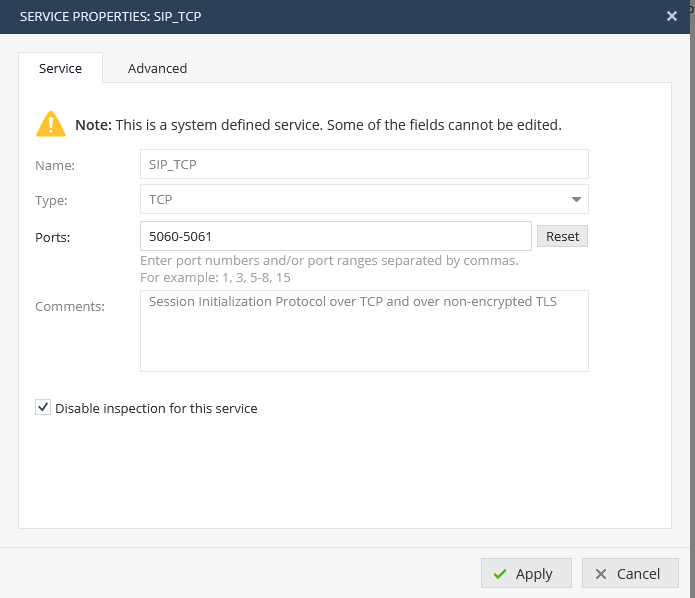
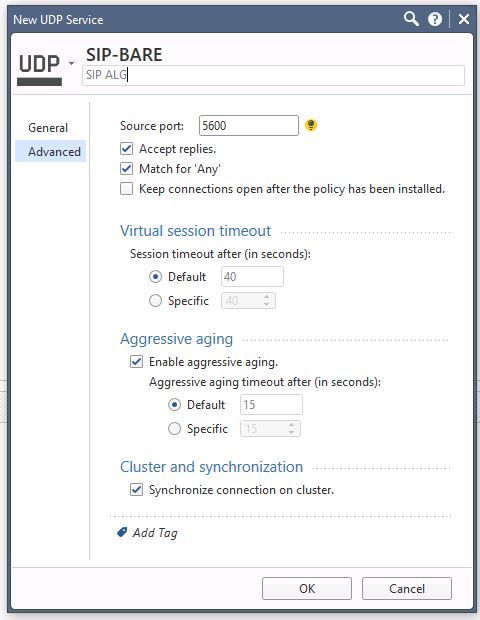
- Define your own UDP or TCP object without a protocol handler. For example: Name it SIP-BARE and use UDP/5600
- Make sure you enable "Match for Any" on your own service and disable it on the existing service.
- Make a rule for you own service AND!!!! make sure it is ABOVE any rule that uses the build in SIP services (which contains handlers).
If you forget to put your rule in the right order the whole trick will not work.
As soon as you have a rule that will contain a handler for a specific TCP or UDP port that decision will stick.
So if you have a generic SIP on rule 30 and your own definition on rule 40 you will still see the SIP handler act on those connections.
If you put your own definition in rule 28 and have generic SIP in rule 30 then rule 28 will not act on SIP traffic but rule 30 will still act on SIP traffic and do all sorts of magic.
I must admit this is a tricky concept to understand at first but once you understand these basics you can explain a lot of unexpected behaviour in Check Point firewalls.
So far I have not been able to verify this is still how it works with R80.10 and I have yet to add a PABX to my lab. (Actually I have a 3CX PABX but it has some other issues I need to sort out first.)
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
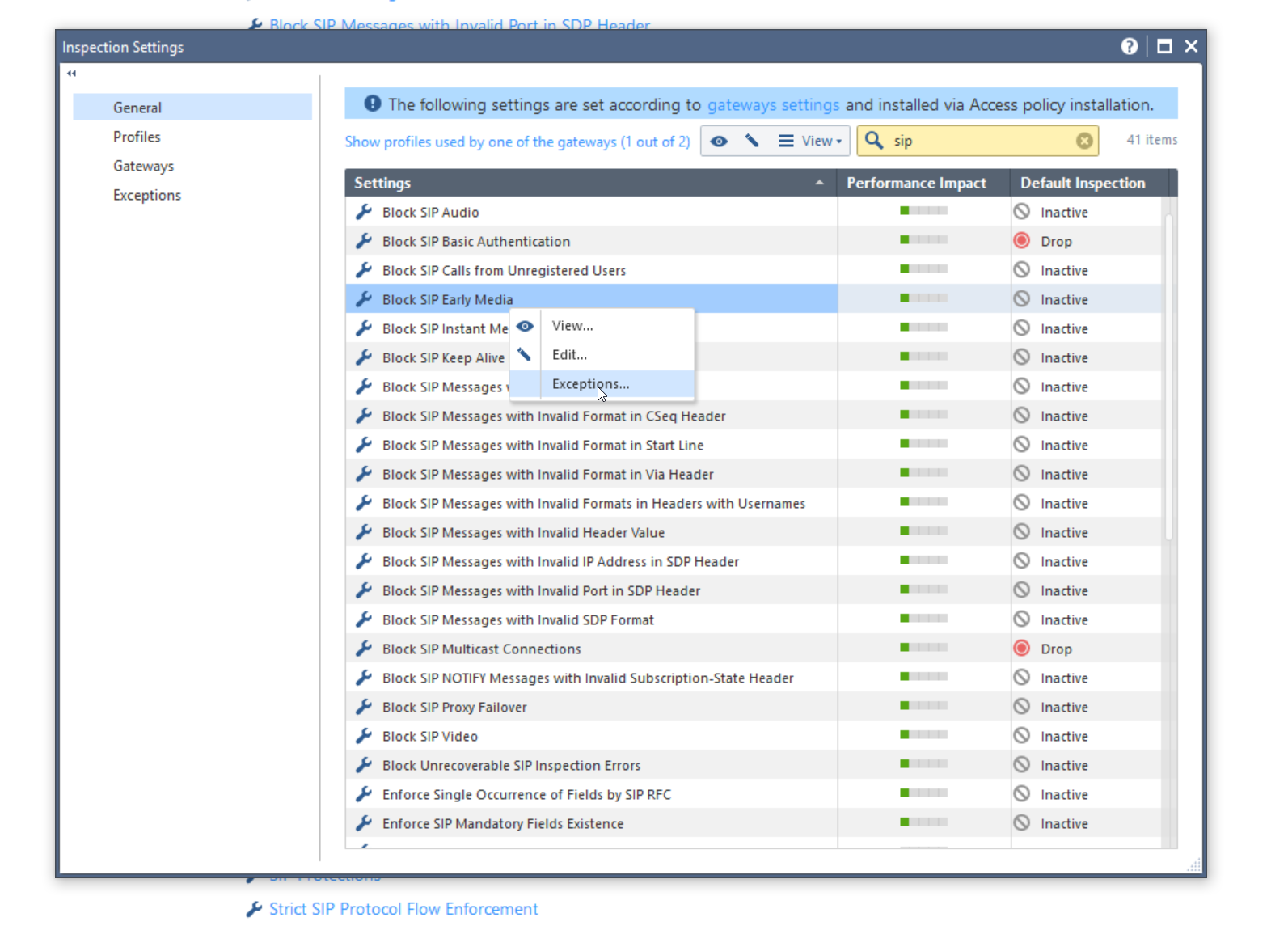
You can do this by creating exception for this inspection setting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What are the exceptions settings?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You should Disable Inspection for this device in network object menu !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
I have a question about security risk from disabling SIP ALG inspection. to disable SIP ALG by creating an exception for Block SIP Early Media on this inspection setting
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
how about 1800 series ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually I am not sure Tomer answer will work. After having been on first name bases with R&D VOIP for a year with loads of VOIP tickets in R65 I learned a lot of the background of the code. And I guess most of it is still valid.
At least in R77.30 I always use the following strategy:
- Define your own UDP or TCP object without a protocol handler. For example: Name it SIP-BARE and use UDP/5600
- Make sure you enable "Match for Any" on your own service and disable it on the existing service.
- Make a rule for you own service AND!!!! make sure it is ABOVE any rule that uses the build in SIP services (which contains handlers).
If you forget to put your rule in the right order the whole trick will not work.
As soon as you have a rule that will contain a handler for a specific TCP or UDP port that decision will stick.
So if you have a generic SIP on rule 30 and your own definition on rule 40 you will still see the SIP handler act on those connections.
If you put your own definition in rule 28 and have generic SIP in rule 30 then rule 28 will not act on SIP traffic but rule 30 will still act on SIP traffic and do all sorts of magic.
I must admit this is a tricky concept to understand at first but once you understand these basics you can explain a lot of unexpected behaviour in Check Point firewalls.
So far I have not been able to verify this is still how it works with R80.10 and I have yet to add a PABX to my lab. (Actually I have a 3CX PABX but it has some other issues I need to sort out first.)
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your solution should work on R80.10 as well.
Please make sure that voip_multik_enable_forwarding param is off when no SIP inspection needed to avoid heavy performance issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you replying to Hugo's method or Tomer?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SIP works on UDP 5060 port.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 17 | |
| 7 | |
| 6 | |
| 6 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Wed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter