- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Policy Insights and Policy Auditor in Action
19 November @ 5pm CET / 11am ET
Access Control and Threat Prevention Best Practices
Watch HereOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: How to Monitor Concurrent VPN users connected ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to Monitor Concurrent VPN users connected to a Gateway (OID)
Dear Checkmates,
If a customer have asked to you how to monitor the concurrent VPN sessions per user with a specific SNMP tool you will have to follow the following procedure:
1. Login to the Gateway via SSH
2. From clish run the command "show configuration snmp" to check which is your community
The Output should be something like this:
CPSG> show configuration snmp
set snmp mode default
set snmp agent on
set snmp agent-version any
set snmp community labtest read-only
add snmp interface eth2.4
add snmp interface lo
Note: The community in this case is "labtest"
3. Go again to expert mode and create a directory:
CPSG# mkdir /var/log/snmpmon_script
4. Navigate to the directory you created in the previous step
CPSG# cd /var/log/snmpmon_script
5. Create a script in which you will put the following command:
CPSG# vi vpnconcurrentmon.sh
fw tab -t userc_users -s | awk '{print $4}' | grep -v -e "#VALS"
Notes: If you want to insert press "i" then paste the command and to save the changes and exit type
5.1. ":"
5.2. "wq!"
5.3. "Enter"
6. Then we have to make sure that the script that we have created works "sh vpnconcurrentmon.sh"
-It should give you the number of concurrent VPN users
7. Then you have to use snmpwalk to make sure your firewall is not using the OID you are about to configure:
CPSG# snmpwalk -v 2c -c labtest localhost .1.2.3.4.5.6.7.8.15
Note: The OID that we want to use in this case is: .1.2.3.4.5.6.7.8.15
8. Then we will create a copy of the original file, to have a copy and modify the original:
CPSG# cd /etc/snmp
CPSG# cp userDefinedSettings.conf userDefinedSettings.conf_original
9. Then to modify the original file we have to make a new "vi" to the file named: "userDefinedSettings.conf"
CPSG# vi userDefinedSettings.conf
9.1 In the editor add the line at the end of the comments "#":
extend .1.2.3.4.5.6.7.8.15 process_monitor /bin/sh /var/log/snmpmon_script/vpnconcurrentmon.sh
10. In clish mode restart snmp services:
CAT-EP> set snmp agent off
CAT-EP> set snmp agent on
CAT-EP> save config
CAT-EP> exit
11. In expert mode validate your OID:
CPSG# snmpwalk -v2c -c labtest localhost .1.2.3.4.5.6.7.8.15
iso.2.3.4.5.6.7.8.15.1.0 = INTEGER: 1
iso.2.3.4.5.6.7.8.15.2.1.2.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114 = STRING: "/bin/sh"
iso.2.3.4.5.6.7.8.15.2.1.3.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114 = STRING: "/var/log/snmpmon_script/concurrentvpn.sh"
iso.2.3.4.5.6.7.8.15.2.1.4.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114 = ""
iso.2.3.4.5.6.7.8.15.2.1.5.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114 = INTEGER: 5
iso.2.3.4.5.6.7.8.15.2.1.6.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114 = INTEGER: 1
iso.2.3.4.5.6.7.8.15.2.1.7.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114 = INTEGER: 1
iso.2.3.4.5.6.7.8.15.2.1.20.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114 = INTEGER: 4
iso.2.3.4.5.6.7.8.15.2.1.21.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114 = INTEGER: 1
iso.2.3.4.5.6.7.8.15.3.1.1.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114 = STRING: "2"
iso.2.3.4.5.6.7.8.15.3.1.2.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114 = STRING: "2"
iso.2.3.4.5.6.7.8.15.3.1.3.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114 = INTEGER: 1
iso.2.3.4.5.6.7.8.15.3.1.4.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114 = INTEGER: 0
iso.2.3.4.5.6.7.8.15.4.1.2.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114.1 = STRING: "2"
CPSG#
CPSG# fw tab -t userc_users -s | awk '{print $4}' | grep -v -e "#VALS"
2
11.1 Then use again the snmpwalk command to navigate to the correct OID:
CPSG# snmpwalk -v2c -c labtest localhost .1.2.3.4.5.6.7.8.15.4.1.2.15.112.114.111.99.101.115.115.95.109.111.110.105.116.111.114.1
18 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
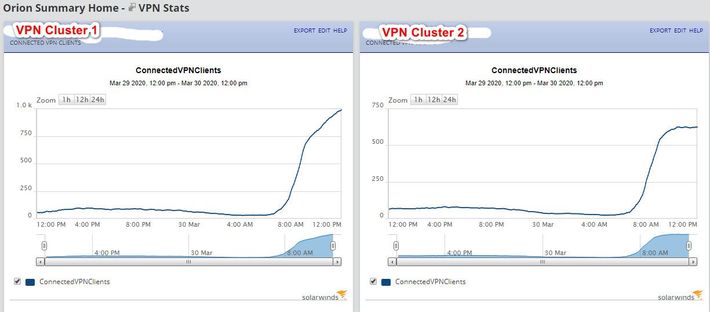
Good morning everyone. We're doing this currently with SolarWinds NPM, and we went about it slightly different. We currently have our entire organization working from home, connected to two separate VPN gateway clusters. This is what we did;
1.) Enable SNMP in Gaia, and make sure your poller has SNMP access to it via the rulebase on the gateway.
2.) Make sure SolarWinds NPM has discovered the gateway, and is actively monitoring it.
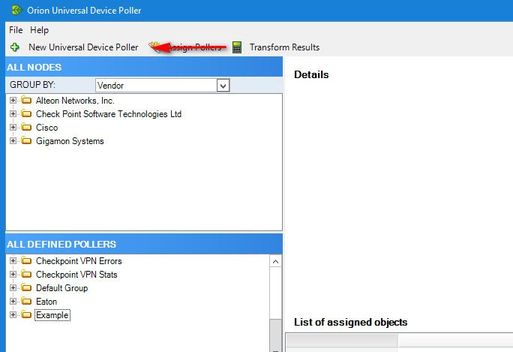
3.) From the SolarWinds server, open the Universal Device Poller tool, and create a new Universal Device Poller;
4.) Setup the OID, give it a name, and set the polling interval;
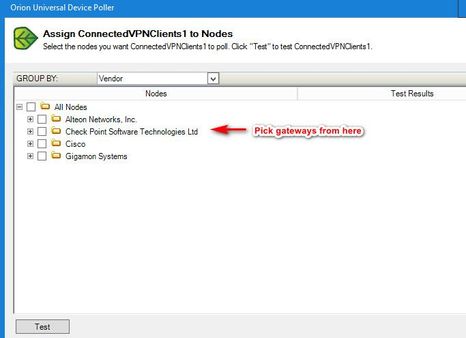
5,) Assign it to the nodes you want to monitor;
That's pretty much it. Here's an example of what the graphs look like;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is exactly the information I was looking for.
However, I am getting really strange results:
[Expert@auc01-fw-ext01-a:0]# snmpget -c public -v 1 172.18.160.2 .1.3.6.1.4.1.2620.1.2.5.4.23.0
SNMPv2-SMI::enterprises.2620.1.2.5.4.23.0 = STRING: "163"
[Expert@auc01-fw-ext01-a:0]# fw tab -t userc_users -s
HOST NAME ID #VALS #PEAK #SLINKS
localhost userc_users 147 72 87 0
As you can see, 72 vs 163.
Did you encounter anything like this?
On another gateway, I am getting 6 vs 279.
→ CCSE, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there. It took some trial and error on our part as well, but what I noticed is that is you drop the '0' (zero), you get the proper result. It seems as though adding that final zero gives you the high water mark for the most connected clients the gateway has seen at one time.
Try 1.3.6.1.4.1.2620.1.2.5.4.23, and see if you get the desired results.
Try 1.3.6.1.4.1.2620.1.2.5.4.23, and see if you get the desired results.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did try without the .0 on the end and got an SNMP error. The environment I tested on is R80.10, which is slated for upgrade soon anyway. Obviously from all the discussion here, the various releases produce different results, and there also appears to be bugs surrounding this. Looks like I will have to fallback on a script to get the data, like original solution at the top of this thread.
→ CCSE, CCTE
→ CCSE, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May need a patch from TAC to resolve this on R80.10.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, even after upgrade to R80.30 T155, same results. So, I gave up and did the original SNMP script solution described at the beginning of this thread. Works great, but a custom mod that must be tracked between major upgrades.
My client is happy with solution. I do wish there was a reliable OID that truly returned the same result as "fw tab -t userc_users -s"
→ CCSE, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Adam,
Make sure you are using a specific OID that is not being used by something else, remember that you have to navigate to the specific number of OID that has the number of your current vpn sessions,
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the step by step. I am not finding the 1.3.6.1.4.1.2620.1.2.5.4.23 oid in the Universal Device Poller. I even did a MIB update. Any suggestions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello!
wow this is a cool thing, but can you explain, why i see too little users when i run the same stuff on a R80.20SP plattform?
[Expert@NWATSBGFWCL01-ch01-04(active)# g_fw tab -t userc_rules -s
1_01:
HOST NAME ID #VALS #PEAK #SLINKS
localhost userc_rules 164 98 877 0
1_02:
HOST NAME ID #VALS #PEAK #SLINKS
localhost userc_rules 164 98 876 0
1_03:
HOST NAME ID #VALS #PEAK #SLINKS
localhost userc_rules 164 98 877 0
1_04:
HOST NAME ID #VALS #PEAK #SLINKS
localhost userc_rules 164 98 877 0
[Expert@NWATSBGFWCL01-ch01-04(active)# ./vpnconcurrentmon.sh
94
i see 98 connected to the Maestro, but the script shows me 94?
is there a logical explanation?
best regards
Thomas.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I use on R80.20 the MIB iso.3.6.1.4.1.2620.500.9000.1.2 and get all current Users via SNMPv3.
Then we wrote a own check-plugin additional to the standard Checkpoint Plugins to have a overview on our "Check MK" monitoring server with counter and usernames.
The check is a little bit rudimentary (not much configurable now) but perhaps it´s useful for someone else here:
#!/usr/bin/python
# -*- encoding: utf-8; py-indent-offset: 4 -*-
# +------------------------------------------------------------------+
# | ____ _ _ __ __ _ __ |
# | / ___| |__ ___ ___| | __ | \/ | |/ / |
# | | | | '_ \ / _ \/ __| |/ / | |\/| | ' / |
# | | |___| | | | __/ (__| < | | | | . \ |
# | \____|_| |_|\___|\___|_|\_\___|_| |_|_|\_\ |
# | |
# | Copyright Mathias Kettner 2014 mk@mathias-kettner.de |
# +------------------------------------------------------------------+
#
# This file is part of Check_MK.
# The official homepage is at http://mathias-kettner.de/check_mk.
#
# check_mk is free software; you can redistribute it and/or modify it
# under the terms of the GNU General Public License as published by
# the Free Software Foundation in version 2. check_mk is distributed
# in the hope that it will be useful, but WITHOUT ANY WARRANTY; with-
# out even the implied warranty of MERCHANTABILITY or FITNESS FOR A
# PARTICULAR PURPOSE. See the GNU General Public License for more de-
# tails. You should have received a copy of the GNU General Public
# License along with GNU Make; see the file COPYING. If not, write
# to the Free Software Foundation, Inc., 51 Franklin St, Fifth Floor,
# Boston, MA 02110-1301 USA.
# .1.3.6.1.2.1.1.1.0 Linux gateway1 2.6.18-92cp #1 SMP Tue Dec 4 21:44:22 IST 2012 i686
# .1.3.6.1.4.1.2620.1.1.25.3.0 19190
#checkpoint_connections_default_levels = (40000, 50000)
import datetime
vpn_states = {
"3": "Active",
"4": "Destroy",
"129": "Idle",
"130": "Phase1",
"131": "Down",
"132": "Init",
}
def inventory_checkpoint_vpnconnections(info):
# pprint.pprint(info)
return [(None, None)]
def check_checkpoint_vpnconnections(item, params, info):
state = 0
counter = 0
infotext1 = ""
for lauf in info:
# print (lauf[2])
user = lauf[0].split("@")
starttime = saveint(lauf[2])
timea = datetime.datetime.fromtimestamp(starttime)
timeb = timea.strftime("%m/%d/%Y, %H:%M:%S")
# print (timea)
infotext1 += user[0] + " Status: " + vpn_states[lauf[1]] + " Since: " + timeb + "\n"
counter =+ counter +1
# + vpn_states[lauf[1]
# + " since : " + datetime.fromtimestamp(lauf[2]) + "\n"
infotext=("%d VPN Connections\n" % counter )
return state, infotext + infotext1, [("vpnconnctions", counter)]
check_info["checkpoint_vpnconnections"] = {
"check_function": check_checkpoint_vpnconnections,
"inventory_function": inventory_checkpoint_vpnconnections,
"service_description": "VPNConnections",
"has_perfdata": True,
"group": "checkpoint_connections",
"snmp_scan_function": scan_checkpoint,
"snmp_info": (".1.3.6.1.4.1.2620.500.9000.1" , [ "2", "4", "29" ]),
"includes": ["checkpoint.include"],
}
Regards,
Andi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Results from fw tab -t userc_users -s differ greatly from OID 1.3.6.1.4.1.2620.1.2.5.4.23.0, SmartConsole and SmartView Monitor in our environment (R80.30 Take 111). I raised a support call about it and a fix was provided in Take 155 (see PRJ-3404, PRJ-5954, VPNS2S-417 SmartView Monitor VPN tunnel status may show incorrect or missing tunnels status for a cluster object.) However, when I installed this in production it made the problem worse with the figures wildly different to fw tab. I have raised a new call now and been provided with another hotfix. I'm not going to be able to deploy that in production for a while as it involves a simultaneous reboot of both cluster members so have gone down the SNMP extend script route now for our monitoring.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
in this case I should see the RA Users by Endpoint Security client . Are there any method to see the Mobile Access Users via SNMP?
Thanks.
Jacopo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much, it has been very useful to me!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Learning SNMP, bare with me: I was wondering why the OID .1.2.3.4.5.6.7.8.15 was used? Is that just an example? I’m trying to poll using What’s Up Gold but it defaults to 1.3.6.1 when setting up a poll due to the Checkpoint mib that is loaded. Any assistance would be appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think it is one OID pre defined on GAIA OS to add your own commands.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Always return 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to set virtual system 1 ?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 24 | |
| 18 | |
| 15 | |
| 13 | |
| 12 | |
| 10 | |
| 6 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Wed 19 Nov 2025 @ 11:00 AM (EST)
TechTalk: Improve Your Security Posture with Threat Prevention and Policy InsightsThu 20 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERThu 20 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAWed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchWed 19 Nov 2025 @ 11:00 AM (EST)
TechTalk: Improve Your Security Posture with Threat Prevention and Policy InsightsThu 20 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERThu 20 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAWed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter