- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Re: HTTPS inspection: Inspection despite exclusion...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HTTPS inspection: Inspection despite exclusion?
hi there,
i've created an exclusion for a website like printing.post.de. To do this i went to HTTPS Inspection Blade, created a policy. As Source i chose an Access Role. Theres an Active Directory Group behind it.
As Destination i created an Object "domain" like .printing.post.de. Action is "Bypass". Saved and installed.
It works like this for almost all users but one. Theres one user, thats also part of the AD Group, that triggers the HTTPS inspection.
The website isnt working for that user and i can see that the site is inspected in the logfiles
There are no known differences between that user and all the others
Any hints?
regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds like you did it properly. Personally though, I ALWAYS use wildcard for https bypass, ie *printing.post.de*, Im sure that would work. If you give it a go, you can test, something like below screnshot
Best,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Note that this can match more sites than you might expect. Among other things, it would match printing.post.de.virusbiz.ru.
I posted an analysis of what a custom application/site object matches a little under a year ago.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats very true, agree. Thats a danger in using those I suppose, though personally, I never had an issue.
Best,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
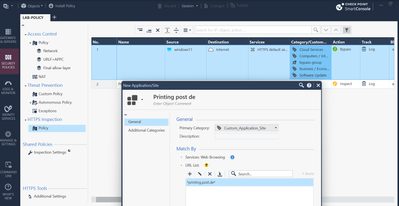
Hi @the_rock ,
today i tried to cleanup our smartconsole a bit. We use at the moment single domains for those httpsi rules, and not an application group
i created now an Application (httpsi Whitelist)and added some websites there
i then created a new rule with "source" as computergroup, Destination internet and category "httpsi Whitelist". Action bypass. very similar to your screenshot
But it wont work. Websites are inspected, though. Is there anything else needed for this?
it looks like attached. IT consists of our IT Department computers. the whitelist contains only one website with no special setups
thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is the key. You need to ensure those sites are ALLOWED in urlf layer, as per my post below. Im positive if you do that, it will work. I had R80.30, R80.40 lab, now I have R81.20 and R82 ssl inspection lab, never an issue.
Andy