- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Firewall HA status (health check)
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Firewall HA status (health check)
All,
Is there a script that can be run on the MDS to show the HA state of the clusters in that CMA.
I thought about using a generated candidate list from CDT tool however, I was not sure it this would be accurate enough ( i thought it would be :-). Is there another option or will this be fine.
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is the command you have to run on GW:
cphaprob state
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi G_W_A.
We have over 2k of firewall and going to each running that command is not feasible and time consuming..
What I am trying to accomplish is to pull all the firewall status, in one location, whether by MDS, or any way that is suggested. We have multiple MDSs and I am thinking that whatever solution I get would have to be ran on all of the MDS we have for the relative CMA and respective firewall.
Generating a candidate list will give a listing of the firewalls within a CMA (mdsenv) and you can tell the HA status there, but is there a script that will pull all the firewalls (per CMA) (without having to "mdsevn" into the CMA).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can run a command FROM SMS on every GW: GAIA - Easy execute CLI commands on all gateways s...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
You can use the AMON based cpstat command.
It has a variety of flags based on the machine type (Management, Gateway etc.).
In your case from the Domain (CMA) run cpstat <flag> -h <IP address of Security Gateway or Cluster or Cluster member>
So, for clustering status:
cpstat ha -h <IP address>
Just run cpstat once on the gateway to see the various flags, for example:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, this actually worked pretty well.
It still puts me in a position to run it for each firewall.
So far the candidate list seems to the best solution to see all the firewalls, per CMA, all at once.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can also use below:
[Expert]# cphaprob
Usage:
cphaprob [-vs <vsid>] state ................................. Shows cluster states of all members
cphaprob [-reset [-h|-c]] [-l <count>] show_failover ........ Shows cluster failover information
cphaprob names .............................................. Shows the member print mode in local logs
cphaprob [-reset] [-a] syncstat ............................. Shows the Delta Sync overall statistics
cphaprob [-reset] ldstat .................................... Shows the transport layer statistics
cphaprob [-i[a]] [-e] [-l] list ............................. Shows Critical Devices in problem state (use the -l flag to view the full list)
cphaprob [-vs all] [-a][-m] if .............................. Shows status of all cluster interfaces (use the -m flag to view VLAN monitoring mode)
cphaprob show_bond [<bond_name>] ............................ Shows all monitored bond interfaces
cphaprob show_bond_groups ................................... Shows all groups of bond interfaces
cphaprob igmp ............................................... Shows the IGMP membership status
cphaprob fcustat ............................................ Shows the Full Connectivity Upgrade statistics (when upgrading between minor versions)
cphaprob tablestat .......................................... Shows the information about the cluster interfaces on all members in a table format
cphaprob routedifcs ......................................... Shows the interfaces that are monitored by RouteD daemon when OSPF is configured
cphaprob roles .............................................. Shows the roles of the RouteD daemon
cphaprob release ............................................ Shows SW version match for all cluster members
cphaprob ccp_encrypt ........................................ Shows the CCP Encryption mode
cphaprob [-d|-f|-s] corr .................................... Shows the Correction Layer stats (All|Dispatcher|Firewall|SXL)
cphaprob mvc ................................................ Shows the Multi-version cluster state
NOTE: Some commands are NOT applicable for 3rd party clusters.
[Expert]# cphaconf
Usage:
cphaconf [-i <machine id>] [-p <policy id>]
[-n <cluster num>] [-c <cluster size>]
[-l <failover track mode >] [-m <service|primary-up|active-up>]
[-R 'a'|<required IF num>] [-f <Decision function type>]
[-t <sync IF 1>...] [-d <non-monitored IF 1>...]
[-M multicast|pivot] [-N <MAC magic num>]
[-u <member_name1,member_name2,...>]
start .................................................... Configures internal cluster settings
cphaconf stop ..................................................... Stops clustering on this member
cphaconf [-t <sync IF 1>...] [-d <non-monitored IF 1>...] add ..... Adds Sync and Private interfaces explicitly to the kernel
cphaconf clear-secured ............................................ Clears Sync interfaces from the kernel
cphaconf clear-non-monitored ...................................... Clears non-monitored interfaces
cphaconf debug_data ............................................... Prints ClusterXL internal data to dmesg (see sk93306)
cphaconf delete_link_local [-vs <vs_id>] <IF name> ................ Removes a link local VIP from the interface
cphaconf set_link_local [-vs <vs_id>] <IF name> <cluster IP> ...... Adds a link local VIP to the interface
cphaconf mem_id_mode <id|name> .................................... Configures how local logs show this member - by ID or NAME
cphaconf failover_bond <bond-name> ................................ Performs failover between slave interfaces in the bond
cphaconf [-s] <set|unset|get> var <name> [value] .................. Configures and shows values of global kernel parameters
cphaconf bond_ls <set <name> <value> | remove <name>> ............. Configures the minimal number of required slaves for bond LS
cphaconf set_pnote -d <device> -t <timeout(sec)>
-s <ok|init|problem> [-p] [-g]
register........................................ Registers the user-defined Critical Device
cphaconf set_pnote -f <file> [-g] register ........................ Registers the user-defined Critical Devices from the file
cphaconf set_pnote -d <device> [-p] [-g] unregister ............... Unregisters the user-defined Critical Device
cphaconf set_pnote -a [-g] unregister ............................. Unregisters all Critical Devices
cphaconf set_pnote -d <device> -s <ok|init|problem> [-g] report ... Reports the specified state for the Critical Device
cphaconf ccp_encrypt <on/off> ..................................... Configures CCP Encryption mode
cphaconf ccp_encrypt_key <key> .................................... Configures CCP Encryption key
cphaconf mvc <on/off> ............................................. Configures Multi-version cluster state
NOTE: Some commands are NOT applicable for 3rd party clusters.
[Expert]
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you The Rock, I will look into these commands.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you also tried Management API commands to retrieve lists:
mgmt_cli show simple-clusters
https://sc1.checkpoint.com/documents/latest/APIs/#introduction~v1.8%20
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
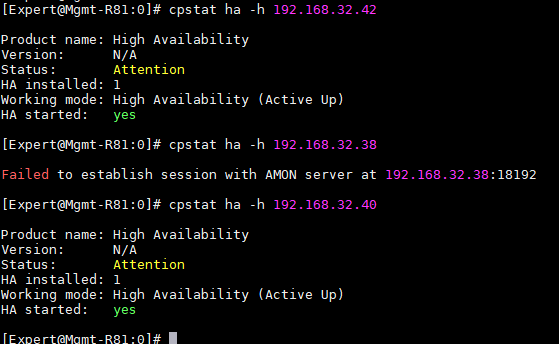
Hello,
I ran the command given on CLI and got the response below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
are there any pre-requisites?
mdsenv Domain1
#cpstat ha -h <IP of cluster>
#cpstat ha -h <IP Gateway1>
#cpstat ha -h <IP Gateway2>
gaves always the exact same result:
Product name: High Availability
Version: N/A
Status: OK
HA installed: 1
Working mode: High Availability (Active Up)
HA started: yes
I thought to get a standby message from gateway2
[R80.40]
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks - I'll ask someone to look at this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
We ran this in the lab and when one of the members is down it does give Status: Attention
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
my understanding was that it is possible to fetch the HA status from the MDS.
In our case, (R80.40) it does not work. But never mind.
Regards
[Expert@MDS-01:0]# mdsenv DOM1
## ClusterXL
[Expert@MDS-01:0]# cpstat ha -h IP-address of Cluster
Product name: High Availability
Version: N/A
Status: OK
HA installed: 1
Working mode: High Availability (Active Up)
HA started: yes
[Expert@MDS-01:0]# cpstat ha -h IP-address of GW1
Product name: High Availability
Version: N/A
Status: OK
HA installed: 1
Working mode: High Availability (Active Up)
HA started: yes
[Expert@MDS-01:0]# cpstat ha -h IP-address of GW2
Product name: High Availability
Version: N/A
Status: OK
HA installed: 1
Working mode: High Availability (Active Up)
HA started: yes
## VRRP Cluster
[Expert@MDS-01:0]# cpstat ha -h IP-address of Cluster
Product name: High Availability
Version: N/A
Status: OK
HA installed: 1
Working mode: High Availability (Active Up)
HA started: yes
[Expert@MDS-01:0]# cpstat ha -h IP-address of GW1
Product name: High Availability
Version: N/A
Status: OK
HA installed: 1
Working mode: Sync only (OPSEC)
HA started: yes
[Expert@MDS-01:0]# cpstat ha -h IP-address of GW2
Product name: High Availability
Version: N/A
Status: OK
HA installed: 1
Working mode: Sync only (OPSEC)
HA started: yes
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 21 | |
| 17 | |
| 14 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter