- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: F5 BIG-IP ICAP and SandBlast (TEX)
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
F5 BIG-IP ICAP and SandBlast (TEX)
Enable SandBlast ICAP server
Login to export mode and start the ICAP server on the TEX appliance or security gateway.
[Expert@cp-fw-01:0]# icap_server start
cpwd_admin: Process CICAP started successfully (pid=31792)
[Expert@cp-fw-01:0]#
Check if the ICAP processes are running.
[Expert@cp-fw-01:0]# ps -def |grep icap admin
31792 4631 0 19:19 ? 00:00:00 c-icap -N -f /opt/CPsuite-R77/fw1/c-icap/etc/c-icap.conf admin
31813 31792 0 19:19 ? 00:00:00 c-icap -N -f /opt/CPsuite-R77/fw1/c-icap/etc/c-icap.conf admin
31820 31792 0 19:19 ? 00:00:00 c-icap -N -f /opt/CPsuite-R77/fw1/c-icap/etc/c-icap.conf admin
31826 31792 0 19:19 ? 00:00:00 c-icap -N -f /opt/CPsuite-R77/fw1/c-icap/etc/c-icap.conf admin
31931 31651 0 19:20 pts/1 00:00:00 grep icap
[Expert@cp-fw-01:0]#
Enable ICAP logging.
[Expert@cp-fw-01:0]# tecli advanced remote emulator logs enable
remote emulator logs set to enabled successfully
[Expert@cp-fw-01:0]#
Also make sure that your firewall rules allow access to the ICAP server port 1344/TCP on the TEX appliance or security gateway.
Please note that Jumbo Hotfix Accumulator Take_286 or higher for R77.30 should be used.
More information can be found in sk111306: Check Point support for Internet Content Adaptation Protocol (ICAP) server
Prepare the F5 BIG-IP
Download the f5.checkpoint_sandblast_icap iApp template from the link below. This is an iApp template that creates ICAP related elements (nodes, pool, internal virtual server, profiles). The newly created request and response adapt profiles can be used by standard virtual servers so they can interact with a Check Point SandBlast ICAP Server.
- Login to the Configuration Utility and Import the iApp template: iApps > Templates > Import.
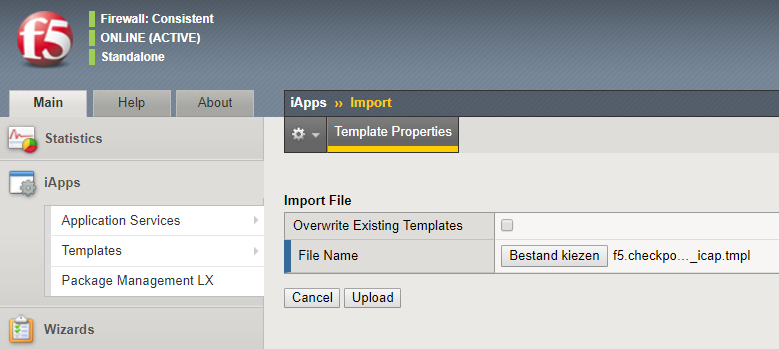
- Deploy a new application by using the iApp: iApps > Application Services > Applications > Create.
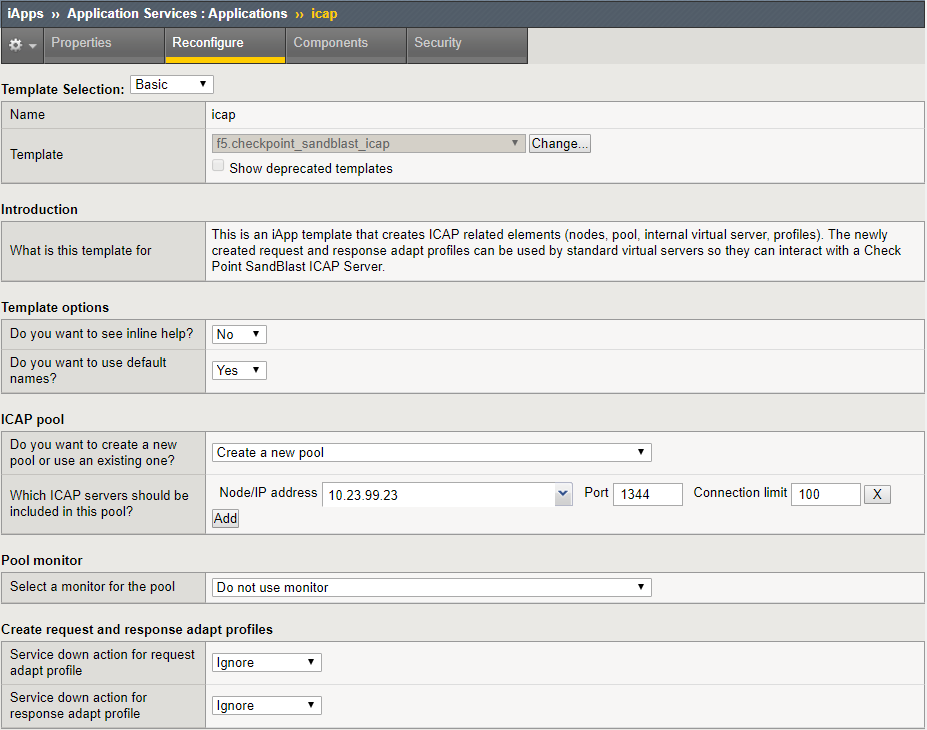
- Click Finished to deploy the iApp. You will see the components that have been configured.

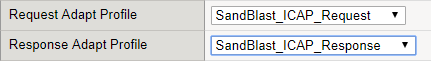
- You can now use the newly created Request and Response Adapt profiles and attach them to a Virtual Server that has been configured with a HTTP profile.
Testing Check Point SandBlast
Below you'll see some screenshots of what happens when a user attempts to upload or download malicous files.
Malicious uploads
- Upload a file that triggers Threat Emulation (Zero-Day Protection).
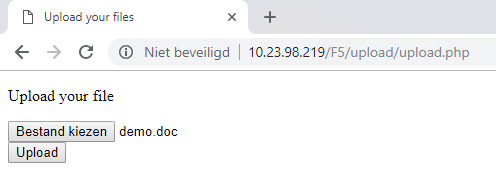
- The upload of this malicious file is prevented by Check Point SandBlast.

- Here you can see the log message that is created by Check Point.
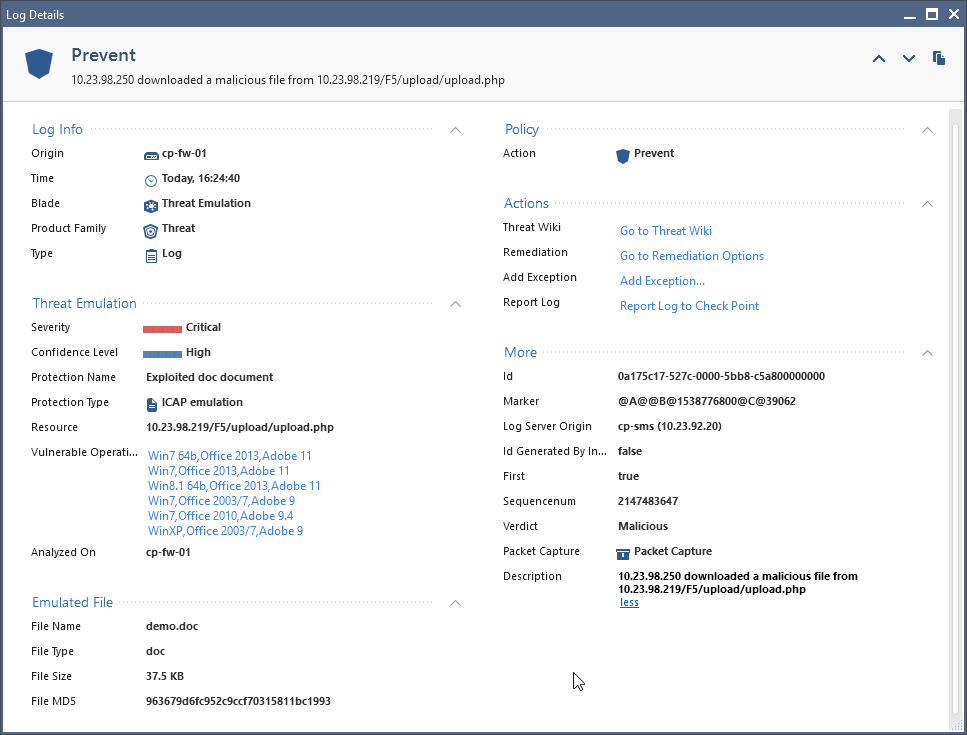
Malicious downloads
- A user tries to download a malicious file.
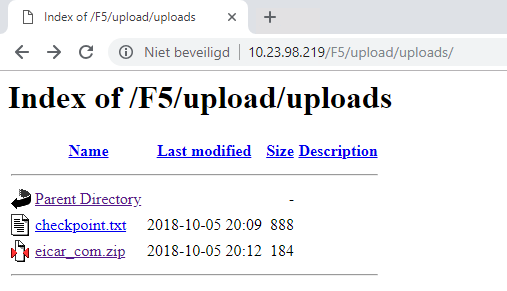
- The download of a malicious file is prevented by Check Point SandBlast.
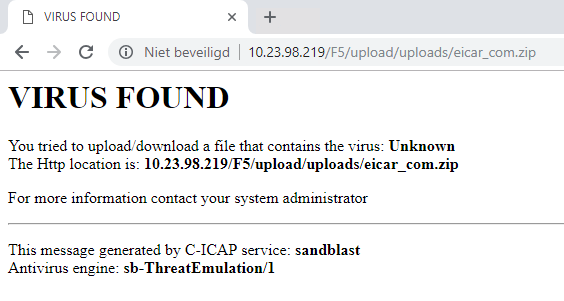
- Below of an example what log message is created by Check Point.
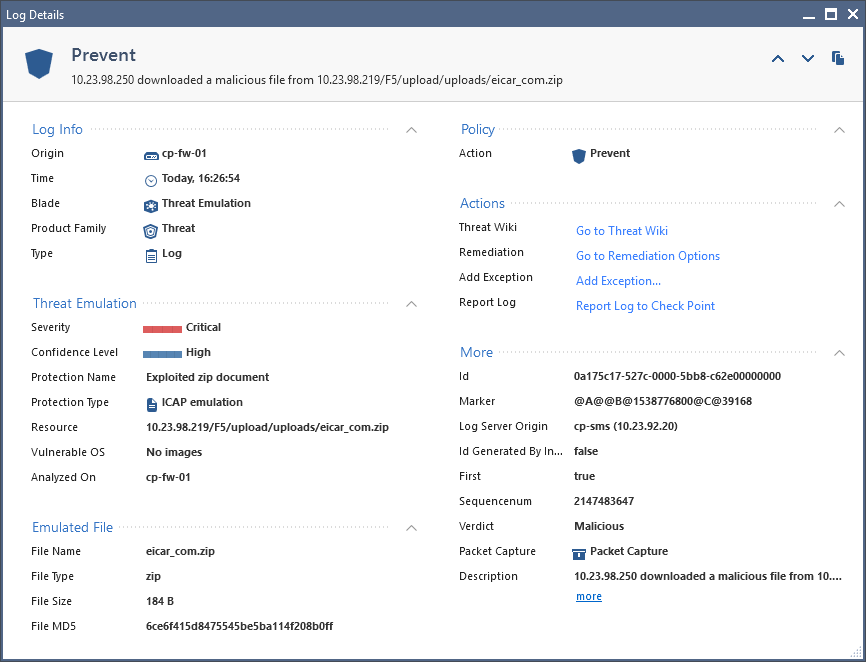
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Niels van Sluis,
nice!
You have one problem with this configuration! On the F5 config, you can not set the max. ICAP connections setting. If the maximum ICAP connection number is exceeded, you will get an ICAP error. I had a big customer who had a real problem with that. During testing this is not noticeable at first, because the max. connection number is usually not reached.
In the iApp, there is also no entry for max. connections to see in your pictures.
I work a lot with F5 and I have not found a solution for this problem. No iRules or other solutions are possible.
I already had a ticket for this topic at F5 and Check Point open. But without success.
If you have a solution write it here please. I'd be very happy if there was a solution.
Otherwise I'd be careful!
With a Symantec (Bluecoat) SG, Fortigate, Squid or McAfee Web Gateway this works without problems.
Symantec (Bluecoat) SG ICAP and Sandblast (TEX)
Fortigate Firewall ICAP and Sandblast (TEX)
McAfee Web Gateway ICAP and Sandblast Appliance (TEX)
Maybe Thomas Werner from Check Point has a solution or more informations.
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Niels van Sluis,
I just looked at the iApp template.
In the iApps template I also didn't see anything about max ICAP connections!
I find the article great but please be careful without max. ICAP connection settings.
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko,
Thanks for your feedback, I'll look in to this. I didn't know this to be an issue.
Kind regards,
--Niels
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko,
So I assume setting the Connection Limit on the SandBlast_ICAP_Pool pool member didn't work? Do you have an easy way of reproducing this error?
I've been testing, but all seems okay (although my firewall had a load of 64). See the below output.
[nielsvs@localhost ~]$ ab -n 1000 -c 200 http://10.23.98.219/F5/upload/uploads/eicar_com.zip
This is ApacheBench, Version 2.3 <$Revision: 1706008 $>
Copyright 1996 Adam Twiss, Zeus Technology Ltd, http://www.zeustech.net/
Licensed to The Apache Software Foundation, http://www.apache.org/
Benchmarking 10.23.98.219 (be patient)
Completed 100 requests
Completed 200 requests
Completed 300 requests
Completed 400 requests
Completed 500 requests
Completed 600 requests
Completed 700 requests
Completed 800 requests
Completed 900 requests
Completed 1000 requests
Finished 1000 requests
Server Software: C-ICAP
Server Hostname: 10.23.98.219
Server Port: 80
Document Path: /F5/upload/uploads/eicar_com.zip
Document Length: 459 bytes
Concurrency Level: 200
Time taken for tests: 155.535 seconds
Complete requests: 1000
Failed requests: 0
Non-2xx responses: 1000
Total transferred: 625000 bytes
HTML transferred: 459000 bytes
Requests per second: 6.43 [#/sec] (mean)
Time per request: 31106.983 [ms] (mean)
Time per request: 155.535 [ms] (mean, across all concurrent requests)
Transfer rate: 3.92 [Kbytes/sec] received
Connection Times (ms)
min mean[+/-sd] median max
Connect: 0 2 2.6 1 10
Processing: 1219 29546 7854.4 29687 56783
Waiting: 1219 29545 7854.3 29687 56782
Total: 1229 29548 7853.1 29688 56787
Percentage of the requests served within a certain time (ms)
50% 29688
66% 32377
75% 34387
80% 35846
90% 38867
95% 41347
98% 43732
99% 45058
100% 56787 (longest request)
[nielsvs@localhost ~]$
Kind regards,
--Niels
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Niels van Sluis,
This does not describe the maximum number of connections over the F5.
It is the maximum number of connections between ICAP Server and ICAP Client.
You can limit this on a Symantec (Bluecoat) SG as follows:
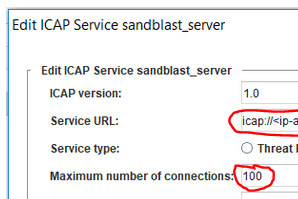
It doesn't work on F5.
For example, the TE Appliance provides 100 ICAP TCP sockets and the 101 connection between F5 and TEX Appliance is established, an ICAP error occurs.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko,
When setting the pool members (read: the pool member is the SandBlast ICAP server) connection limit to for example 50, it does limit the ICAP connections being sent to the SandBlast ICAP server. However, this seems to result in the virtual server that has the adapt profiles attached become unavailable (connections being rejected). What happens on the Bluecoat when the Maximum number of connections to the SandBlast ICAP server is being reached? Will it just serve the requests without content scanning (fail-open) or will it reject requests until resources become available again?
Kind regards,
--Niels
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Bluecoat SG is running a queuing of objects until one of the ICAP TCP connections can process a request. This may make everything very slow. But there are no ICAP errors.
However, you can adjust the parameters on the TEX Appliance in the following file:
$FWDIR/c-icap/etc/c-icap.conf
I don't have a system to test right now. Please read the infos under the following link:
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As I said, I do not think it is reasonable to limit it to the F5.
So I wouldn't use it in critical environments.
I'm a big fan of F5 and Check Point. But here I don't see any solution for the problem at the moment.
But maybe ask Thomas Werner from Check Point. He's very good at TEX and ICAP themes.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko,
On the F5 BIG-IP it's also posible to queue the connections to the ICAP server when there is a connection limit set on the connections to the ICAP server. I've tested it, and it works. Here is how to do it:
- Enable Request Queueing on the SandBlast_ICAP_Pool (see Advanced options).
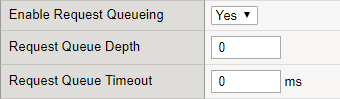
- Set connection limit to the SandBlast ICAP Pool member.
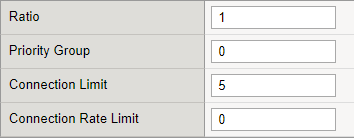
As you can see, in this example the limit of connections towards the ICAP server is set to 5 and Request Queing is enabled. See below the benchmark test without these settings applied and another with the settings applied.
- 10 requests with 10 requests concurrent and as expected 5 are failing, because the limit is set to 5 and there is no queueing.

- 10 requests with 10 requests concurrent and as expected and no failing connections, because queueing is enabled.
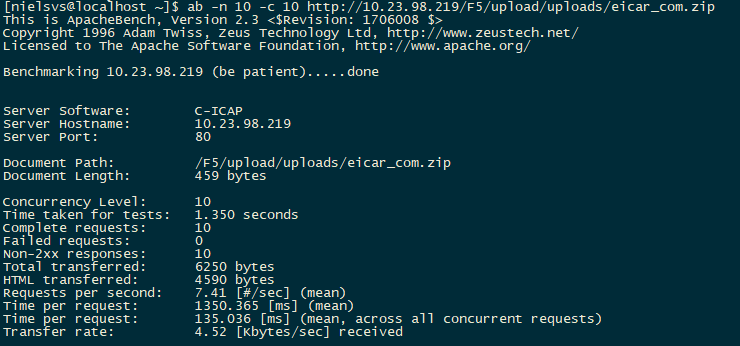
I'll add this to the iApp template soon 🙂
The iApp template now sets the default connection limit of the SandBlast ICAP Server to 100 connections and also Requeust Queueing is enabled on the SandBlast ICAP Server pool.
Kind regards,
--Niels
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very nice! I'll give you 100 points![]() .
.
One more small question. Which F5 version do you use 12 or 13?
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko,
Thanks for the point and feedback. In my lab I have version 14 running. But the functionality being used in the iApp template is also available in version 12 and 13. But I guess also in version 11.
Kind regards,
--Niels
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko, Niels,
In Israel I talked with Heiko about the cons/pros of ICAP as mentioned here, and we talked about an idea to implement the ThreatPrevention API via an iRule.
What do you guys think. Will it work ?
Cheers
Martijn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Martijn,
Hi Niels,
Yes, I had an interesting conversation with Martijn in Israel. Sometimes the world is small:-) I think it is possible to send the file via iRule directly to the Sandblast API via https. I'm gonna take a look at this in a quiet minute. It won't be easy, but it should work.
Regard
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 11 | |
| 11 | |
| 10 | |
| 7 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 3 |
Upcoming Events
Fri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


