- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Enabling web server security
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Enabling web server security
Hi guys,
I have a checkpoint firewall with ngtx. I want to enable web security for my web servers (sql injection, cross site scripting etc.). I did this by creating a host of web server and enabled the protections.
Is that all or do I need to add something else somehwere too. In the guide it mentions the following "Enforcement of these protections are dependent on IPS profile" What does that mean?
Also how can I test that these protections are working via some testing method?
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir,
1. Open a Core Protection
2. In General Tab double click a profile (e.g. Optimized)
3. Go to Advanced Tab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Uh, that one. Drop obviously means, the connection will be terminated once this particual IPS protection is triggered. Accept here means it will be doing "monitor only" for this specific defence. You will get a log, but the connection will persist anyway. Good only for tuning.
26 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Protections can be enabled/disabled in your IPS profile and/or your Threat Prevention policy, depending on management and gateway version.
It would be helpful if you specified the exact steps you followed and provided some screenshots of exactly what you did.
Also, anytime you make changes to IPS, you need to push the Threat Prevention policy (Access Policy for R77.x Gateways).
As far as testing some of these protections, you can use a tool like Burp Suite.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Phoneboy,
Thanks for suggesting BurpSuite, I have applied for a trial.
As for the steps, I did the following
- Created a new host
- Clicked on Servers>Web server>Protections
- Protections were enabled already.
- Pushed the Threat Policy ( exisiting Policy is Scope=Any and Action=Optimized )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Guys,
Kindly help me to know if this is correct. Appreciate the help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What does your Threat Prevention rulebase look like?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear PB,
My threat policy is "ANY" and "OPTIMIZED"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am curious about this as well. I thought we just need to configure the Profile protection and it will apply; This looks very specific to web server; do we need to configure all the web server object this way?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Frank_Yao1,
to enable the Webserver-protections you have to enable the servertype Webserver and the protections on all your webservers host objects.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Wolfgang,
I want to confirm if my config is right or not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your configuration is correct (assuming gateway is R80.x).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes Kandarp, you config looks good.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This was required pre-R80.x, but I don't believe this is no longer required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoy , please clarify:
Are we still required to configure the Web Server objects and their protections individually, or is the "Optimized" profile taking care of that irrespective to the target server?
Thank you,
Vladimir
P.S. It is really difficult to track which response is relevant to which thread in the forum unless person is mentioned by name and the excerpt from their post is included in the reply.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I follow Vladimir, there should be a statement for the web security configuration.
I think it is too needed in R80.xx, there are no protections like „SQL injections, cross site scripting, etc. „ in the normal IPS protections.
Dameon, please can you clarify if needed or not.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm checking this, but I don't believe it's required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Checking on all of it 🙂
And yes, I'm aware we need to add indents in threads, but that's turning out to be a bigger problem to solve than it should be.
And yes, I'm aware we need to add indents in threads, but that's turning out to be a bigger problem to solve than it should be.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes you are still required to do that. Those protections have moved to so called core protections that are installed with Access Control Policy. See my full response to this thread.
EDIT: I thought this response would have shown under Vladimir's question. Hmmm...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
There two types of protections (or actually three if you count also inspection settings):
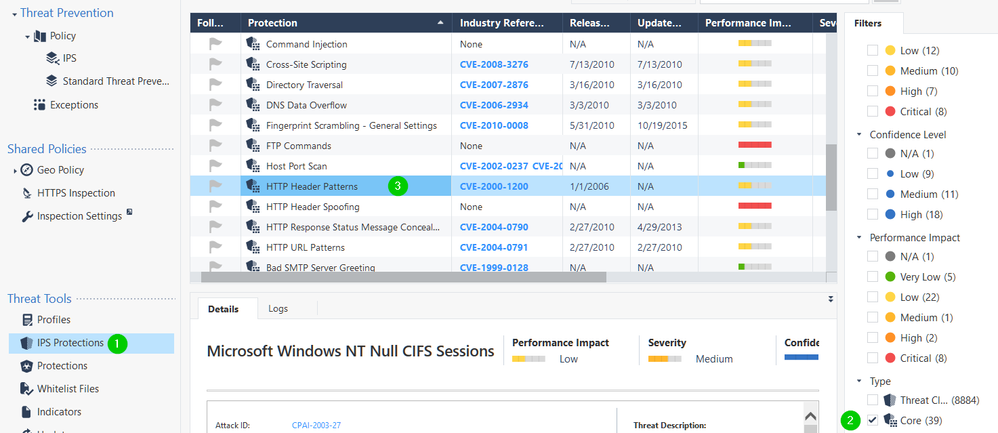
Threat Cloud Protections that are the actual IPS Protections updated from Check Point Threat Cloud. These protections are installed with the Threat Prevention Policy.
Core Protections are protections that require IPS blade, but are there by default (there are 39 of them or so). These protections are installed with the Access Control Policy.
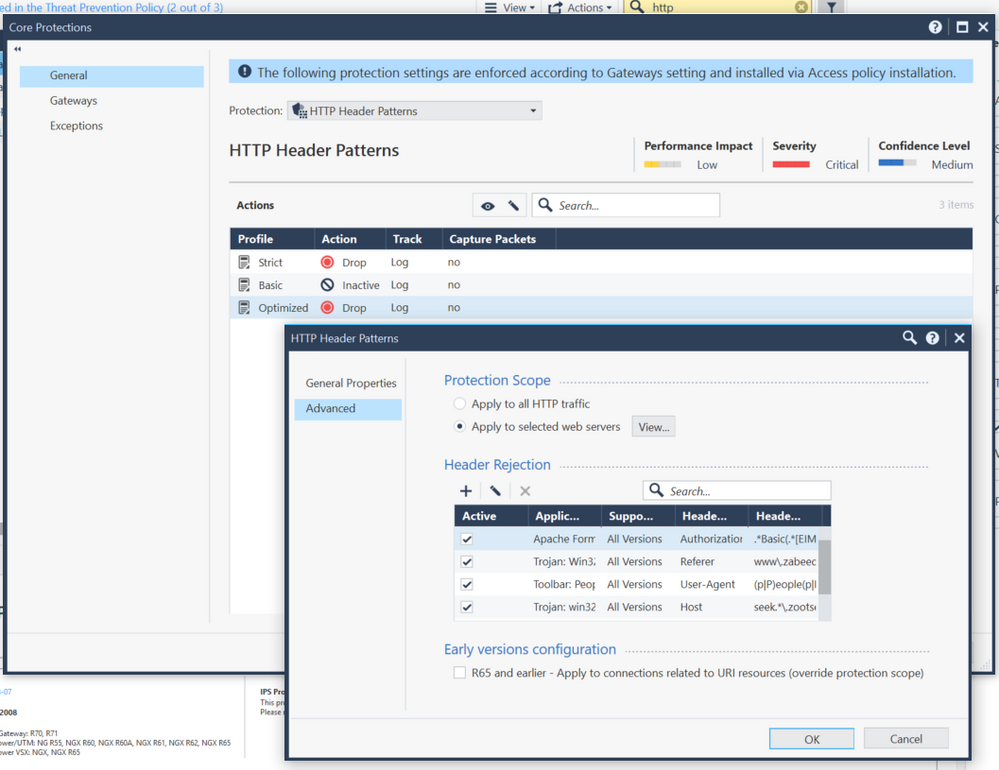
Core Protections are assigned directly to the gateways with their profile. You can then select whether you want this specific protection to be assigned to a selected web server or not (if it's a web server related protection). If you know your web servers and have configured them, make sure "Apply to Selected Web Servers" is selected. Otherwise select "Apply to all HTTP Traffic". By clicking View you can view the web servers that you have configured in the host object as a web server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Lari_Luoma , how on earth did you get to see the screen from your post above 🙂 ?
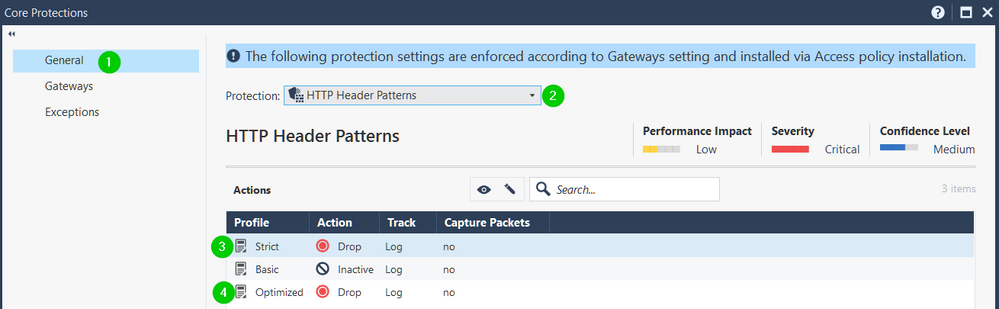
I am pocking in both, R80.20 and R80.30 in Core Protections and all I am seeing is:
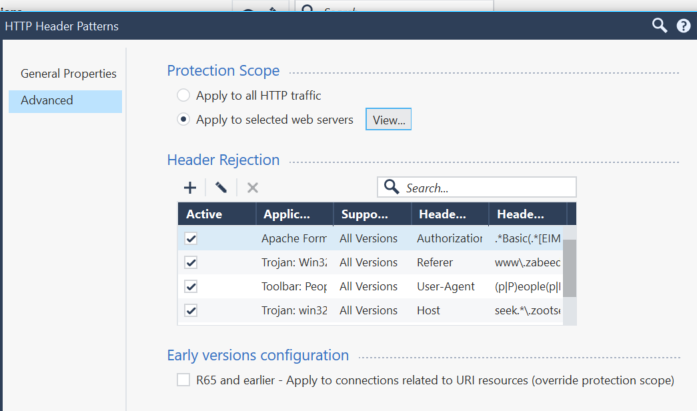
and when editing the selected "HTTP Header Patterns", I am seeing:
Which, IMHO, got to mean that the entire scope is protected and that there is no need to cherry-pick the Web Servers.
Am I looking at this wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir,
1. Open a Core Protection
2. In General Tab double click a profile (e.g. Optimized)
3. Go to Advanced Tab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you @Lari_Luoma ! I am looking at it now.
One comment for Check Point developers: If you have a protection that is not really being enforced until additional settings are configured, perhaps another icon and action should be defined for it (i.e. gear with "config required").
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Lary,
can you clarify the difference between Accept and Drop in IPS core protection Action?
thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Vladimir,
can you clarify the difference between Accept and Drop in action field?
thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is no Accept in IPS, AFAIK. What are you trying to figure out?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Uh, that one. Drop obviously means, the connection will be terminated once this particual IPS protection is triggered. Accept here means it will be doing "monitor only" for this specific defence. You will get a log, but the connection will persist anyway. Good only for tuning.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great, thank you! So, basically, "accept" in IPS core protection is considered a kind of "detect" for IPS ThreatCloud protection, very confusing.
This information is not documented nowhere! Very helpful
Kind regards
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 37 | |
| 29 | |
| 11 | |
| 10 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter