- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Efficient way to disable several hundred IPS p...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Efficient way to disable several hundred IPS protections that do apply to our environment
1. What is the the most efficient way to disable several hundred IPS protections that do apply to our environment? We are trying to avoid the use of manual method such as shown in the attached screenshot.
2. Can you also share a strategy how to apply different list of IPS rules for the External and Internal Policy. For example, IPS protections that the attack requires that the vulnerable system be exposed to the internet should not be applied to the internal firewall policy.
3 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Normally the best way to address the needs for protections in the different parts of the network is entirely around a few things:
1. Asset management: Knowing what assets are in different parts of the environments based of change control requirements in your organization.
2. Vulnerability assessments: If you are running a vulnerability scanning tool (Rapid7, Nessus, OpenVAS) you can look at the assets in the network and build your IPS profile with what is in that part of the environment.
3. Tailored Safe: If you are running R80.30+, you can enable SmartExtension called Tailored Sage and it will build a profile around the hits in your logs. You can just validate the IPs with what services are out there. https://community.checkpoint.com/t5/SmartEvent/IPS-Utilization/m-p/100329
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are a lot of bulk operations that can be easily performed on collections of IPS signatures that are not immediately obvious, the following is excerpted from my "IPS Immersion" self-guided video series.
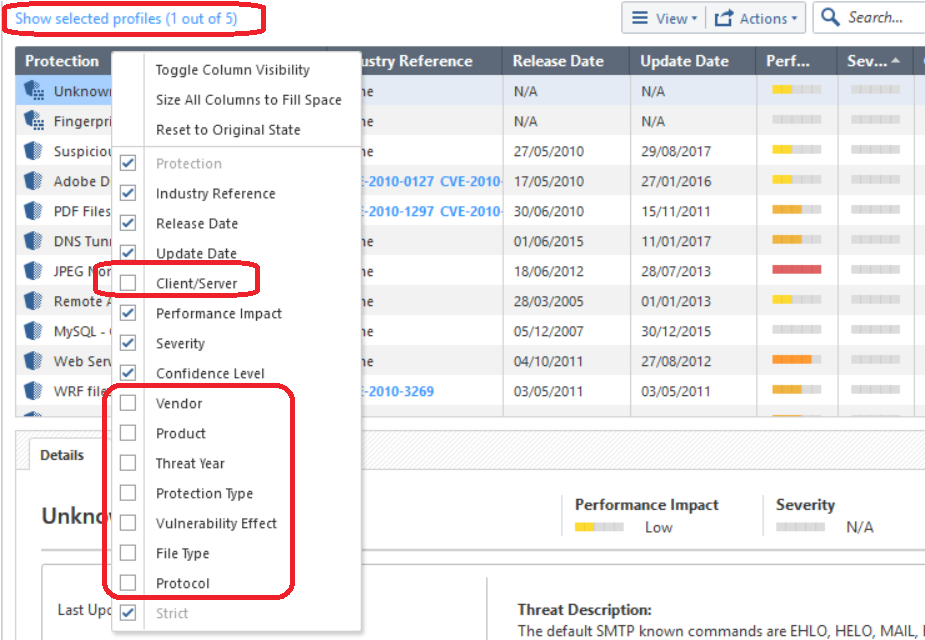
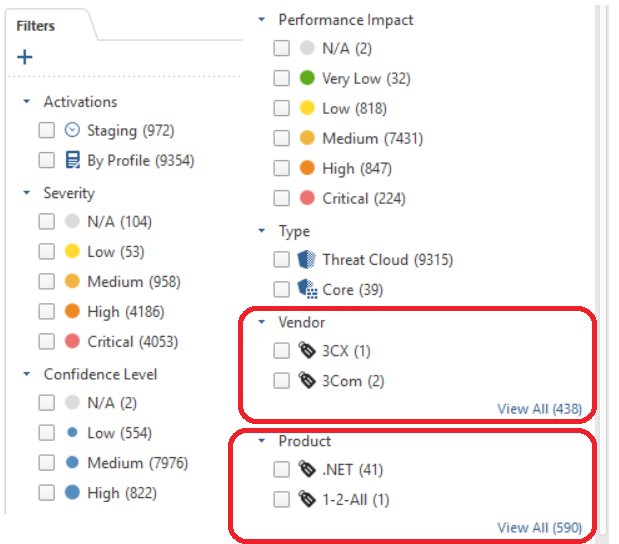
There are many hidden columns on the IPS Protections screen that can be revealed and then used to sort protections, I find the "Vendor" and "Product" ones very useful:
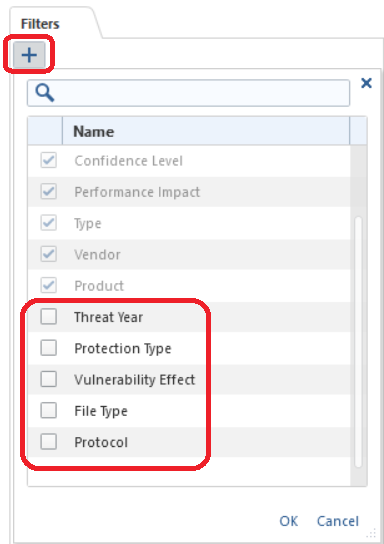
The Filters tab on the right is useful and well, and can have extra filtering criteria unhidden by clicking the "+" character, note the hidden vendor and product lists as well:
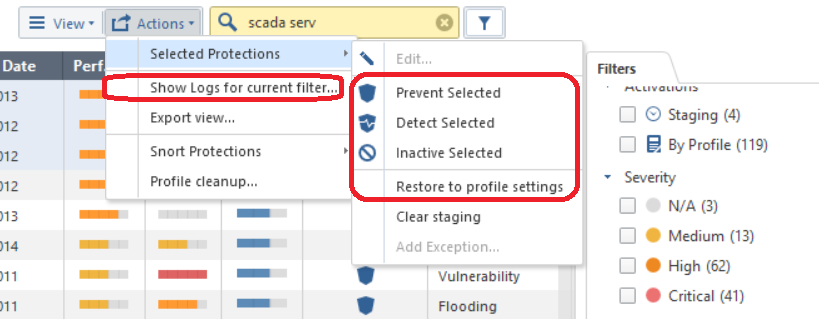
Once you get the desired list of protections displayed by using the various "Filter" tab checkboxes and even the search field above, and you want to perform a bulk operation upon all of those currently displayed, you can set all of them to Protect, Detect, or Inactive from the Actions menu with one click as shown below; these operations can be run on hundreds or even thousands of IPS Protections.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not entirely sure what you are asking, but each IPS Protection is defined as either a "client" or "server" attack; you can expose this hidden header and then sort Protections by client/server to bunch them up for a bulk operation. The client/server designation is unfortunately not available on the Filters tab though.
Server attacks would normally be initiated inbound from the Internet against your server which has some exposure to the Internet, although obviously a server-based attack could be launched from the inside as well. Client attacks usually occur when an internal system visits or is tricked into visiting a malicious website, which then tries to exploit a vulnerability in the client's browser, and shove some kind of malicious code onto the client's machine for execution. So Server attacks would definitely qualify as "exposure" to the Internet, but really so would Client based ones, the connection just happens to be initiated by your internal client.
So I guess it depends on what you mean by "exposure".
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for sharing the info!
Is their a way to identify IPS protections based on their applicability to the internal network that is behind the internal firewall? For example based a category of attack types; SQL injection, XSS, etc?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Normally the best way to address the needs for protections in the different parts of the network is entirely around a few things:
1. Asset management: Knowing what assets are in different parts of the environments based of change control requirements in your organization.
2. Vulnerability assessments: If you are running a vulnerability scanning tool (Rapid7, Nessus, OpenVAS) you can look at the assets in the network and build your IPS profile with what is in that part of the environment.
3. Tailored Safe: If you are running R80.30+, you can enable SmartExtension called Tailored Sage and it will build a profile around the hits in your logs. You can just validate the IPs with what services are out there. https://community.checkpoint.com/t5/SmartEvent/IPS-Utilization/m-p/100329
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. We do run vuln scan with Rapid7. What kind of report can run to identify the assets in the environment?
2. Can I use SCCM?
3. I will read the documentation on "Tailored Sage". Our management gateways are R80.40 but the blades are at R80.20.
Finally, how can disable, the several hundred non-applicable IPS protections which are in the current profile, other than by selecting each protection one by one manually? --For example using a csv file
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The most efficient way to disable a bunch of protections is via the API.
On the other hand, why do you feel this is necessary?
If your logic is: better performance with less signatures, you won’t achieve better performance by doing this since most of the performance impact comes from turning on IPS to begin with, not necessarily the specific signatures used (though high/critical performance impact ones will).
If your logic is: reducing false positives, false positives may still be a thing even if you disable all those “irrelevant” signatures.
False positives can be dealt with as needed with exceptions in any case.
I don’t see what’s gained by going through the exercise.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Both reasons:
1. Reduce the specific signatures with performance impact.
2. And also reduce FPs for products or versions we do not have.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are a lot of bulk operations that can be easily performed on collections of IPS signatures that are not immediately obvious, the following is excerpted from my "IPS Immersion" self-guided video series.
There are many hidden columns on the IPS Protections screen that can be revealed and then used to sort protections, I find the "Vendor" and "Product" ones very useful:
The Filters tab on the right is useful and well, and can have extra filtering criteria unhidden by clicking the "+" character, note the hidden vendor and product lists as well:
Once you get the desired list of protections displayed by using the various "Filter" tab checkboxes and even the search field above, and you want to perform a bulk operation upon all of those currently displayed, you can set all of them to Protect, Detect, or Inactive from the Actions menu with one click as shown below; these operations can be run on hundreds or even thousands of IPS Protections.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your post contains valuable information.
Is their any other strategy to define IPS protections based on whether the attack surface needs to be exposed to the internet for the attack to succeed or is unreachable because it is behind the internal IPS blade and the firewall?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not entirely sure what you are asking, but each IPS Protection is defined as either a "client" or "server" attack; you can expose this hidden header and then sort Protections by client/server to bunch them up for a bulk operation. The client/server designation is unfortunately not available on the Filters tab though.
Server attacks would normally be initiated inbound from the Internet against your server which has some exposure to the Internet, although obviously a server-based attack could be launched from the inside as well. Client attacks usually occur when an internal system visits or is tricked into visiting a malicious website, which then tries to exploit a vulnerability in the client's browser, and shove some kind of malicious code onto the client's machine for execution. So Server attacks would definitely qualify as "exposure" to the Internet, but really so would Client based ones, the connection just happens to be initiated by your internal client.
So I guess it depends on what you mean by "exposure".
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You answered my intended question by elaborating it in your explanation.
Thank you!
-Faisal
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 20 | |
| 20 | |
| 16 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter