- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: DoS Rate Limiting (samp rules) Logging
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
DoS Rate Limiting (samp rules) Logging
Hi Mates,
I have configured some test Rate Limiting rules for an R80.20 VSX environment. The config was set with "monitor only" mode enabled first and the rules are in place;
[Expert@fvsx_gateway:3]# fw samp get
operation=add uid=<5e7da64e,00000000,21c2f50a,000078b1> target=all timeout=indefinite action=drop log=log service=any source-negated=true source=cidr:172.16.0.0/12 pkt-rate=100 track=source flush=true req_type=quota
I can see that the rules are enabled and seem to be picking up traffic that should be dropped;
[Expert@vsx_gateway:3]# fwaccel dos stats get
Firewall:
Number of Elements in Tables:
Penalty Box Violating IPs: 0 (size: 8192)
Blacklist Notification Handlers: 0 (size: 1024)
SXL Device 0:
Total Active Connections: 0
Total New Connections/Second: 0
Total Packets/Second: 41
Total Bytes/Second: 4077
Reasons Packets Dropped:
IP Fragment: 0
IP Option: 0
Penalty Box: 0
Blacklist: 0
Rate Limit: 0
Number of Elements in Tables:
Penalty Box: 0 (size: 0)
Non-Empty Blacklists: 0 (size: 0)
Blacklisted IPs: 0 (size: 0)
Rate Limit Matches: 154 (size: 262144)
Rate Limit Source Only Tracks: 94 (size: 262144)
Rate Limit Source and Service Tracks: 0 (size: 262144)
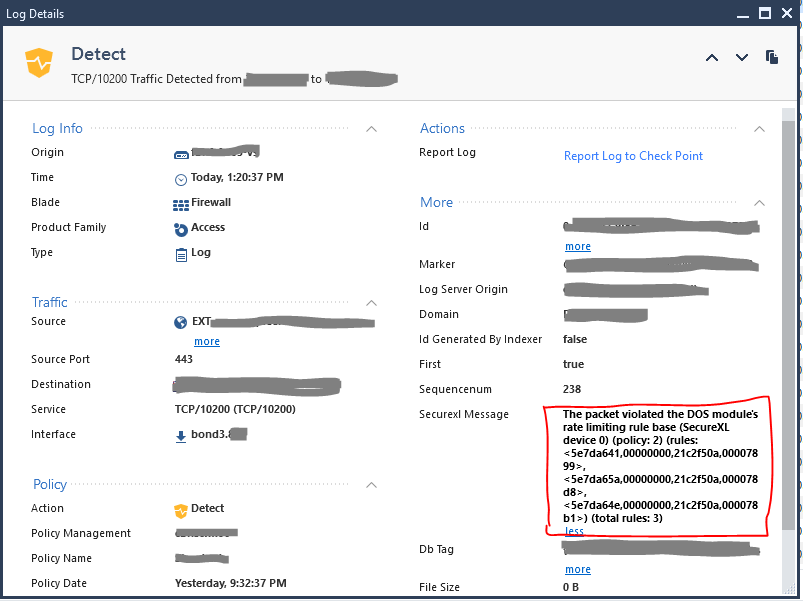
Are these violations also logged in SmartConsole Logs&Monitor?
I've checked against some of the source/dest addresses shown in the "dos_rate_matches" SecureXL table but I can't see anything that suggests that there would be a drop based on Rate Limiting. Has anyone got an example of one of these logs?
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looks like the logs are being presented. I did some updates around actually installing the rules (using "w samp add -t 2 quota flush true") so that may have kicked them into life. They may also just have taken some time to get through to the Mgmt device.
I haven't seen an easy way to search for these ones yet. Free text doesn't seem to work for any of the text or UIDs for the DOS rules. I had to grab the IP out of the fwaccel table ("fwaccel tab -t dos_rate_matches -f") and then search in Logs&Monitor.
Anyone found an easier way to monitor these?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would also like to know if there is an easier way to search the logs for these results. Has anyone found another method?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same here. The feature works well but we are a bit blind if we can't filter/search the logs in smartconsole.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As that field is not indexed, you cannot search for these entries, unfortunately.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could it be indexed?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not without an Request for Enhancement.
Highly recommend working with your local Check Point office around this requirement.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Luis, try using the parameter "-l a" when creating the rate limiting rule. This will create an alert log in logs & monitor. You are then able to filter by "alerts" so it should be fairly easy to locate them unless you have a lot of other alert rules/logs being generated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Chad, the best way I have figured out how to help with tracking the logs is to use the "-l a" parameter which creates an alert log in logs & monitor. You are then able to filter by "alerts" so it should be fairly easy to locate them unless you have a lot of other alert rules/logs being generated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think it is mandatory to be able to to search by source and destination ip for troubleshooting purposes.
But in terms of monitoring we need to be able to identify this type of alerts. The best and easiest way I can think is with the comment and name that fwaccel dos allows you to set with -c and -n.
This way we could totally control the number of fwaccel dos, we could create graphs to track it, etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'd be interested to see how the SmartEvent DOS mitigation rules being created in term s of acceleration. I believe you can search them by "sam rule" free text search, but it will return all of those.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 15 | |
| 13 | |
| 10 | |
| 8 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 2 | |
| 2 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter