- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Content awareness issue
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Content awareness issue
Hey guys,
I hope someone can clarify this for me, though Im pretty sure how it works, but need to see if there is any way around it. So, to make long story short, customer has https inspection enabled, vpn, url and app control, as well as IA and monitoring.
They want to block certain machines from being able to download any exe file off the Internet. Now, this does work, but ONLY if source in content awareness ordered layer is set to any, not if you use specific PC or subnet. Also, if that specific machine is set to bypass google services in https inspection policy, then content awareness does not take place at all.
I replicated this in the lab and its exact same issue and we even have TAC case as well for this. Here are my questions:
1) Considering https inspection takes place before regular policy, does this mean once this traffic is bypassed it wont check anything else after?
2) If 1 is indeed true, is there ANY way to get around this?
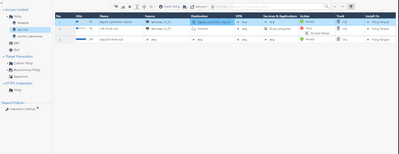
Also, I attached 2 screenshots from my lab. If I disable bypass rule for inspection policy, then all exe files are blocked on windows 10 I use behind the fw.
Tx as always!
Best,
Andy
Andy
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Had call with escalations and here is what DOES work. So, we disabled bypass rule to updatable objects in https inspection policy and then added rule to ALLLOW them in app / urlf ordered layer and that works fine, as it allows content awareness layer to work, since inspection happens. Otherwise, when bypass is there, then content awareness wont take effect.
Please see below:
Best,
Andy
Andy
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
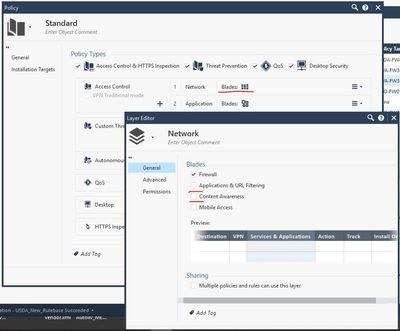
Issue solved after working with TAC escalations. Key is to NOT have specific updatable objects bypassed in https inspection, but rather allow in ordered url / app control layer. If they are bypassed in https inspection, then it will never hit last ordered layer, in our case content awareness, since https traffic would have already been processed.
Update from TAC:
Inspection allows the firewall to go inside the packet and view the unencrypted data thereby classifying the file type, file name etc which is downloaded/uploaded. More on content awareness, after these attributes are identified the usermode processes verify if such content is allowed or blocked. The decision/verdict is provided to the rule base execution engine and the final enforcement block/accept is enforced accordingly.
The reason why this is not in the document is due to the fact that this is only relevant for HTTPS service and not other services like FTP.
I understand their is a concern with the Google Services which will be more clear after discussion with the customer, however until that point please feel free to test the content awareness for HTTPS connections with inspection enabled and let us know if their are any issues.
PS...I thought this was the solution until I had to reboot my mgmt server and then it did not work at all...makes no logical sense. Then when I rebooted gw and windows lab machine, it worked for maybe 30 mins and stopped again. I will update once I talk to escalations again.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hey @the_rock ,
Could you get the expected behavior if you had combine the Content Awareness with Firewall blade, and with App & URL Filtering ?
That way your packets would have hit the Firewall policy and then the Content Awareness part...
Ty,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We tried, but no luck...:- (
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Sorin_Gogean ...just to add something else...and I will speak today to same escalation person in TAC about it. What I find super odd is that google chrome behaves totally inconsistent with this content awareness feature. So, say if I reboot my lab gateway where windows lab test pc sits behind doing https inspection, exe files will NOT be blocked, but they WILL be blocked in IE and mozilla. I dont get it...maybe its related to below CP sk, but already did that and still same issue
But, even with IE and mozilla, thats not consistent all the time. I really have a feeling this blade does not work right at all when it comes to CP. If I cant have it working right in simple lab, I have no confidence to ask the customer to implement it fully in production.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
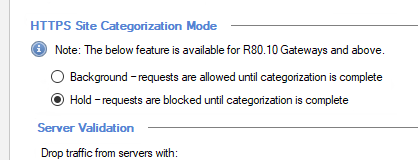
Have you checked the HTTPS Inspection settings regarding Background/Hold Mode:
And we also block QUIC (udp/443) in order to achieve what we want. And after a lot of tweaking we are pretty happy with Content Awareness etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Marcel_Gramalla ...we did implement below, but no luck
If you are referring to setting under blades -> app control and urlf -> advanced settings -> its set to background, but I tried other ones too, same issue.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Huh..the screenshot got lost. I mean this setting above in the good old HTTPS Inspection Dashboard.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
O yea, tried that before, no change.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Had call with escalations and here is what DOES work. So, we disabled bypass rule to updatable objects in https inspection policy and then added rule to ALLLOW them in app / urlf ordered layer and that works fine, as it allows content awareness layer to work, since inspection happens. Otherwise, when bypass is there, then content awareness wont take effect.
Please see below:
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 21 | |
| 20 | |
| 16 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter