- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Can not block TikTok
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
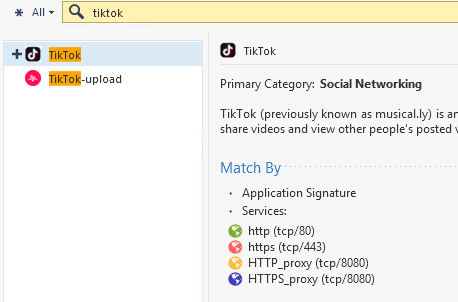
Can not block TikTok
Hi everyone.
I'm having some problems blocking tiktok. Already block the app and domains with an Access Control Policy, in a way it worked but I still can see like 50% of the videos on the app. Is there something else that I can do?
Logs show that FW is blocking some traffic but the app uses different domains and cdn's to reach tiktok. Is there something else that I can do?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
17 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What I do and ALWAYS works is add custom app with *domain*
So, in your case just add custom site as *tiktok* and block it. Sometimes I found I may need to add any existing applications if they exist , but thats not often.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is the rule that I have created for this:
I add on the tiktok custom site the app domains that I found here: https://www.netify.ai/resources/applications/tiktok . Is this what works for you? This is the config that blocks around half of the videos from the app for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In that case, you may need to examine the logs carefully and see why that happens. Do you have https inspection enabled or not?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't have https inspection. What I see on the logs is that the App & URL Policy for TikTok (7) is actually blocking traffic, but the App & URL Cleanup rule (16) is matching some traffic and letting it pass, I think this would explain why I can see some videos but I don't know how to fix it. Cleanup rule is configured to let pass all traffic.
Here you can find attached some evidence.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In some cases, you may need to add the IP addresses to block as well.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cleanup rule is usually configured to drop all traffic not matched by other rules - that is how it got the name 8).
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
True that my friend :-). But, in all seriousness, it is recommended by CP to allow all at the bottom of ordered url and app control layer.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's how we have configured the url and app layer, so the traffic pass the rule that blocks tiktok (even when other traffic to the same IP addres is being blocked for that policy like I mentioned before) and goes all the way down to cleanup rule that allows all. This happens with a lot of IP addresess of tiktok, not just the one from the capture "Permit and block to same IP" that I attached before. Would you recommend to trace and block all those IP addresess?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I would. Sadly, I had to do same for customers in some cases. Even TAC suggested the same. You can open support case to see if they suggest anything else though.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I will tell you what I find works the best, in my opinion...now, this might not be what most customers would do, but works well from what I experienced. Instead of say, creating another url and app control ordered layer, I always end up creating section towards the top of built in access layer with url and app control rules you need. The downside to it could be the fact that you have to enable those blades in this ordered layer, so acceleration might not work as well, but otherwise, I honestly had not seen any major issues with it.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just a quick note - Checkpoint have added tiktok as an application
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried this method but this requires https inspection to work 100%. We see lot of traffic identified as TikTok and blocked, but the website still works and video still plays; Surely you'd think the easy solution is to enable https inspection, but that's not possible because we are talking about a wifi network. Users cannot be forced to download and install certificate for https inspection to work (especially on the mobile devices).
We are able to block correctly using Harmony Mobile following the sk; but that's only managed devices. Devices not managed/guest devices is the concern here.
Interested in hearing some other ideas or suggestions. Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
upon further investigation, we found out this is an issue and open a support case; it's blocking on some gateways but in one specific network and the gateway the traffic going out, it is not blocked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know that - but i would call it PassAll rule...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's what I've always done, and agreed Checkpoint recommends that as well, so your application rules really should be block specific's and then allow everything else (as a generic rule of thumb).
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 21 | |
| 20 | |
| 19 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter