- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
Quantum SD-WAN Monitoring
Register HereAI Security Masters
Hacking with AI: The Dark Side of Innovation
MVP 2026: Submissions
Are Now Open!
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Apple and HTTPS Inspection
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Apple and HTTPS Inspection
Hi,
I am about to implement HTTPS Inspection but there are some issues with Mac's and software updates.
Current HTTPS Inspect rules bypass 17.0.0.0/8 and itunes.apple.com but still there are some issues.
Are there any plans for an Updatable Apple object or anyone else that has run into this issue that has found a solution ?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @nooni ,
Can you be more explicit on what are the HTTPS Inspection issues you're facing - more exactly with examples/screenshots ?
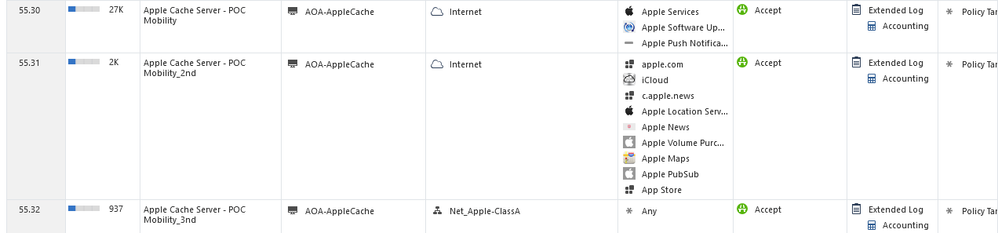
We've looked into this as we are running an POC to implement apple cache servers, therefore we had to make sure that Apple traffic via CheckPoints were not inspected (certificate substituted).
FWL policies looks like:
For the HTTPS Inspection, we're bypassing "apple.com" CustomApp object and "c.apple.news" .
Those objects contains:
| apple.com | c.apple.news |
|
*.aplle.com |
c.apple.news |
So with that, we were able to see that the Apple cache machine, was able to register the Apple Cloud cache services, and download packages.
Ty,
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah, I remember my struggles on this subject with a customer couple of years back who is 95% Apple shop.
What we ended up doing was whitelist followimg:
*apple*
*itunes*
and bunch of Apple IP ranges
Sadly, I wish there were appropriate updatable objects there. Now in all fairness, all other major fw vendors dont have those updatable objects either when it comes to Apple : - (
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, will try that and i hope that someone from Check Point can update us on plans for an Updatable object 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For us to have an Updatable Object, the vendor has to provide the IP ranges in a machine consumable format.
Without that, it’s impossible for us to accurately determine what IP ranges vendors use for what.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you try to use the HTTPS services recommended bypass Updateable object and Apple Smart Accel Updateable object for exception?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes Https inspect bypass both updatable objects is used to bypass.
Could not find any Apple related category in Updatable objects list ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I dont think you would find it, as it simply does not exist : - (. Anyway, I gotta get ready to drive to test center to give my CCTE exam, but when I come back, will fire up my https inspection lab in R81.20 and verify all this.
Cheers mate.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, it was a response to GW Albrecht 🙂
Good luck on your exam!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tx mate! Yea, I know it was response to our good man Guenther :). Anyway, will check when Im back, hopefully around 11 am EST.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It does exist at least since R81.20 / R81.10.00. Please do not state that something simply does not exist if the only reason for the statement is your ignorance ! No harm in telling: I never heard of, i never saw that, i do not believe it exists. But not: Does not exist...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats right, I see exact same thing you posted, which does literally nothing lol. I was on the call once with TAC escalations guy and customer and that was pretty much only thing he could find as well. So, factually, okay, I will give it to you, it DOES exist, but its useless 😂
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @nooni ,
Can you be more explicit on what are the HTTPS Inspection issues you're facing - more exactly with examples/screenshots ?
We've looked into this as we are running an POC to implement apple cache servers, therefore we had to make sure that Apple traffic via CheckPoints were not inspected (certificate substituted).
FWL policies looks like:
For the HTTPS Inspection, we're bypassing "apple.com" CustomApp object and "c.apple.news" .
Those objects contains:
| apple.com | c.apple.news |
|
*.aplle.com |
c.apple.news |
So with that, we were able to see that the Apple cache machine, was able to register the Apple Cloud cache services, and download packages.
Ty,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for sharing this solution 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello there,
Can you show us what is included in your apple software updates object?
We have a simular issue that ipads can no longer recieve updates when inspection is on. however we would like to limit what we exactly open.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Me, personally, I just do *apple* and call it a day lol
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 12 | |
| 9 | |
| 8 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter