- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Anti-Spoofing and VPN Traffic
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Anti-Spoofing and VPN Traffic
Hi CheckMates,
I wanted to do a cleanup of our current Firewall (R77.30) topology and enable Anti-Spoofing in Prevent mode for all interfaces (yes, it was in Detect mode before...).
I checked all routes and defined the topology based on self created groups for all interfaces containing multiple networks.
The strange thing is that I get Anti-Spoofing logs for outgoing VPN traffic. We have one "company backbone" Interface (eth3) where all traffic to 10.0.0.0/8 is routed and our Internet Interface is eth0. Our Clients are coming from eth4.
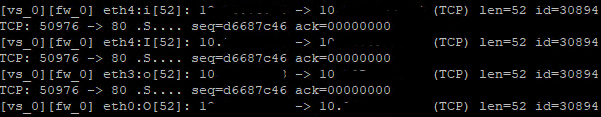
In my logs I can see the following:
For every connection I see a Anti-Spoofing entry coming from eth0 and afterwards the correct VPN message coming from eth4. Strangely enough with fw monitor I can see the traffic coming from eth4:i and eth4:I (which is correct) leaving eth3:o and then finally leaving eth0:o:
I was wondering if you have any idea what's wrong with this setup.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the mistake made the most times with Anti Spoofing and VPN's?
You add a route for 10.0.0.0/8 towards the internal network, even though you only use 10.10.*-10.50.* and you have a VPN with a remote network 10.60.1.0/24, according to the route it lives on the inside of your gateway. When you copy the routing, or in R80.20+ you set the spoofing based on the routing table, you have that network as an internal interface network.
But in fact it lives on the Internet side of the gateway, what you need to do is either get your routing setup properly and if you don't want to do that just add a new group, containing all remote VPN networks, in the 'Do not check for anti-spoofing' option of the internet facing interface.
The reason you see eth3 and then eth0 is due to the fact your main 10.0.0.0/8 route is on eth3 but the VPN is actually routing the traffic out, the Return traffic is dropped by anti spoofing.
Regards, Maarten
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check your interface topology with my One-Liner for Address Spoofing Troubleshooting and compare it with your VPN topology by using my One-liner to show VPN topology on gateways.
From your description it seems that your VPN encryption domains and internal networks definitions are for the same 10.x networks which is causing the spoofing logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the mistake made the most times with Anti Spoofing and VPN's?
You add a route for 10.0.0.0/8 towards the internal network, even though you only use 10.10.*-10.50.* and you have a VPN with a remote network 10.60.1.0/24, according to the route it lives on the inside of your gateway. When you copy the routing, or in R80.20+ you set the spoofing based on the routing table, you have that network as an internal interface network.
But in fact it lives on the Internet side of the gateway, what you need to do is either get your routing setup properly and if you don't want to do that just add a new group, containing all remote VPN networks, in the 'Do not check for anti-spoofing' option of the internet facing interface.
The reason you see eth3 and then eth0 is due to the fact your main 10.0.0.0/8 route is on eth3 but the VPN is actually routing the traffic out, the Return traffic is dropped by anti spoofing.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the quick response. That's exactly our setup right now. The best way would be to clean up the routing table I guess.
It's more work than just excluding the VPNs in Anti-Spoofing but I think it's worth the effort.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Some of our customers with hundreds of networks and no proper IP plan have the exact same issue. And no this is really not something you want to build for those type of customers, just use the exception method works fine on those customers.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Having supernetted RFC1918 routes (for example 10.0.0.0/8) on the firewall using a core router as the next hop, and that same core router having a default route pointing back to the firewall can also cause what I call a "Core Router Supernet Loop" in my book when traffic is sent to a nonexistent/unused network in that supernetted RFC1918 space. Any traffic such as this (that is not NATted) will loop 255 times between the firewall and core router until the TTL decrements to zero and the packet is finally discarded. Very nasty when hundreds or thousands of these types of packets are being generated every second by a worm or NMS probing and they all get looped 255 times...
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is just 1 one the many reasons why we actually want to use dynamic routing for these type of customers.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Maarten,
I have the same situation and i thought about adding a static route specifically for the 10.60.1.0/24 network to the external interface, but I’m encountering the same anti-spoofing issue.
Do you know why the firewall is not analyzing the static route, while only the exception works?
Thank you in advance!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 12 | |
| 8 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter