- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Access role rule over VPN remote access
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Access role rule over VPN remote access
Hi all,
I need to create a rule to allow specific traffic towards specific IPs for some users AND their machines only.
The inline rule from within the LAN is working, so the ADuser+ADmachine+LAN combo can reach the IPs on specific ports; All the other traffic is dropped.
I've created another inline rule for the VPN connected users (Office Mode, CheckPoint Mobile client) but the traffic is always dropped even though enters the rule; I tried different combinations in the source and destination, but I can't understand if it's a problem in the policy or in the way the users are recognized through the VPN.
My current rule is this:
1- src: Any / dst: IP_1, IP_2 / VPN: RemoteAccess / svc: Any / action: (inline layer)
1.1- src: myAccess_Role (ADuser+ADmachine) / dst: Any / VPN: Any / svc: RDP, http / action: Accept
1.2- src: Any / dst: Any / VPN: Any / svc: Any / action: Drop
But I already tried to change the src in the rule 1 (to myAccess_Role or legacy "ADusersVPN@Any"), adding the Office Mode net in the myAccess_Role.
Thanks for any help
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What identity sources are set in your Identity Awareness config for the relevant gateway/s?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry for the late reply, the sources were:
Active Directory Query
Identity Collector
Remote Access
and today I've added the Identity agent (but I'm not sure is properly configured...)
Still not working though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What I did for customer I always work with is create parent rule say office mode to any, any service as parent rule, then few access roles as child rules and we never had a problem.
Can you send a screenshot? Sorry for spelling mistakes, was typing this on my phone.
Happy holidays.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
If you are using remote access as your identity source then I don't think specifying a machine in your AR will work.
The way I would see to accomplish this would be to use the identity agent.
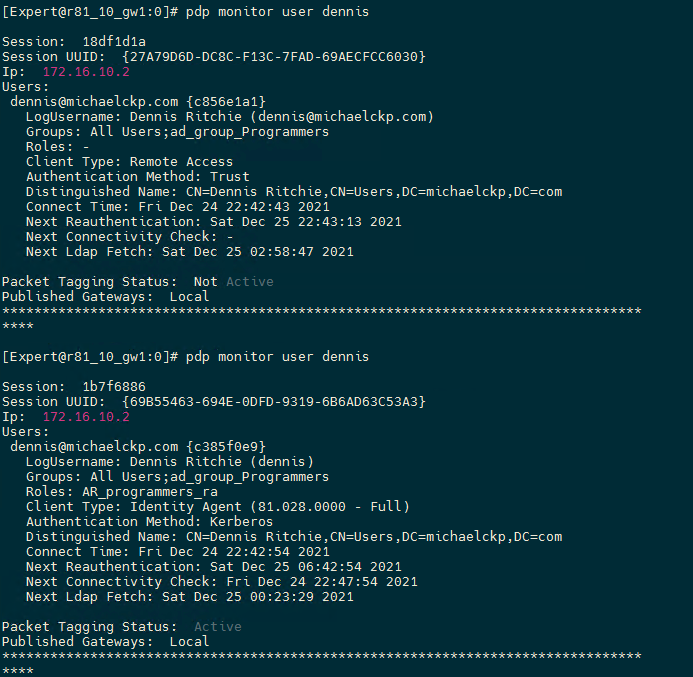
See below where my user identified with remote access was not matched to my AR that specified a user and machine group. You can also see that the user was correctly matched to the AR when sourced from the identity agent.
What I found interesting with this is that the identity agent was able to take over the session even though it has a lower score than remote access per conciliation config. This is convenient in this case where we want both a user and machine association though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the reply,
I've configured the Identity Agent (not sure if I did it the right way though since the documentation is not very clear), I can see that my user now is identified by the ID Agent but if I try to connect to the machines by RDP the traffic is still dropped.
I attach the current rule (n. 24), the 24.1 is:
Networks: Any network
Users: Specified users/groups (5 AD users)
Machines: Specific machines/groups (5 AD clients)
Remote access clients: Any client
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is an update:
I've tried changing the rule 24.1 NOT specifying the machine and the rule is matched, so the problem is that machines are not recognized through the VPN: can you please explain me how to configure the Identity Agent?
I've installed the client on my pc and set the cluster active member as the Server, it says connected but I'm sure this is not complete.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Whats the IP you get when doing a ipconfig or ifconfig on Linux when connected?
The internal network you are triying to reach is different that the one configure for the office mode ip pool (the net you get with the ipconfig result?)
Do you have any error that can provide screenshots?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I'm connected through VPN and I get an Office Mode IP, the rule should allow this traffic since it's set to Any network (I've also tried setting the Office Mode pool specifically).
I don't know which screenshots to provide, at this point it's just a matter of the rule not matching because the user role combo is not matched for the machine.
The identity agent is connected and installed as full version, so I don't know where to configure to recognize the machine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok check the logs and monitor tab to see if there's anything there you can identify and need to adjust a FW rule. Also you can try at your own risk just to test and identify the services/ips etc you need for the rules to create one above the last cleanup rule doing an any any with the vpn community specified and accept then connect and see the logs matching that rule and adjust the corresponding one if this is the case. Thats all for now that i can help so i dont know further, i case you have support also open a TAC case.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 20 | |
| 19 | |
| 18 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter