- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Re: About "CPNotEnoughDataForRuleMatch" and connec...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
About "CPNotEnoughDataForRuleMatch" and connection reset
Hi there,
I've (partly) asked about this before (https://community.checkpoint.com/t5/Security-Gateways/quot-CPNotEnoughDataForRuleMatch-quot-and-quot...), but now I have another related question regarding this behvavior.
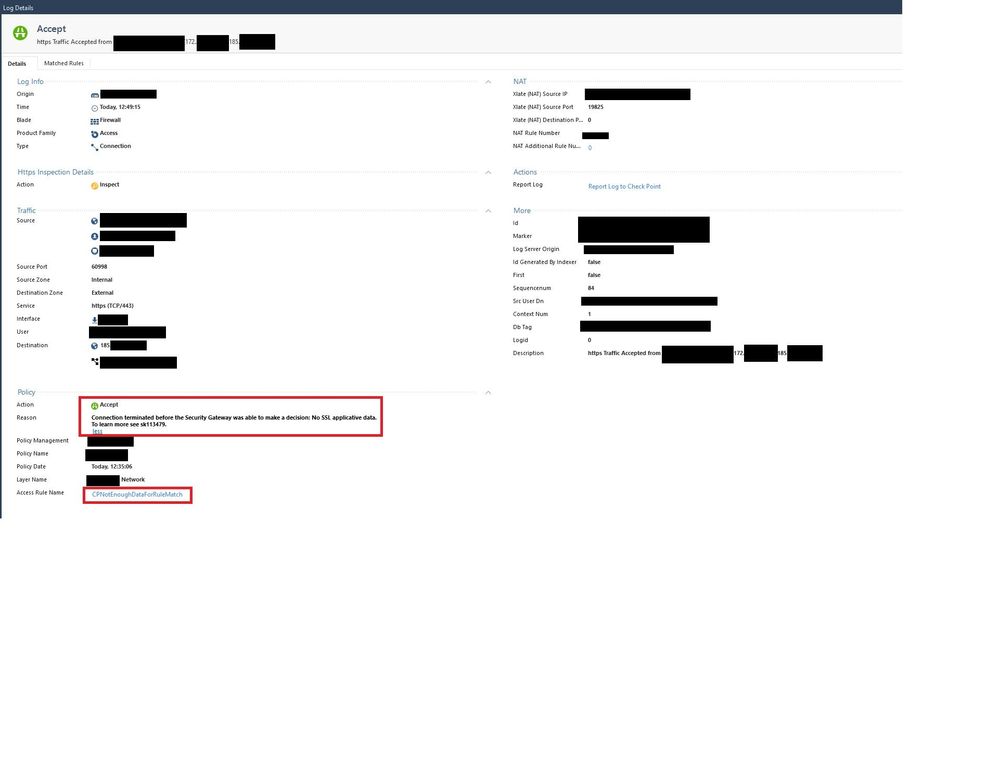
I have a service that connects to an external ip address, but every time the connection gets terminated by a reset from the destination. The log in my firewall says "Accept", however, it is getting "terminated before the Security Gateway was able to make a decision: No SSL applicative data." ("CPNotEnoughDataForRuleMatch").
As I got told in my other post (see link above) the behavior is by design and expected, however, I do have a question to why it happens.
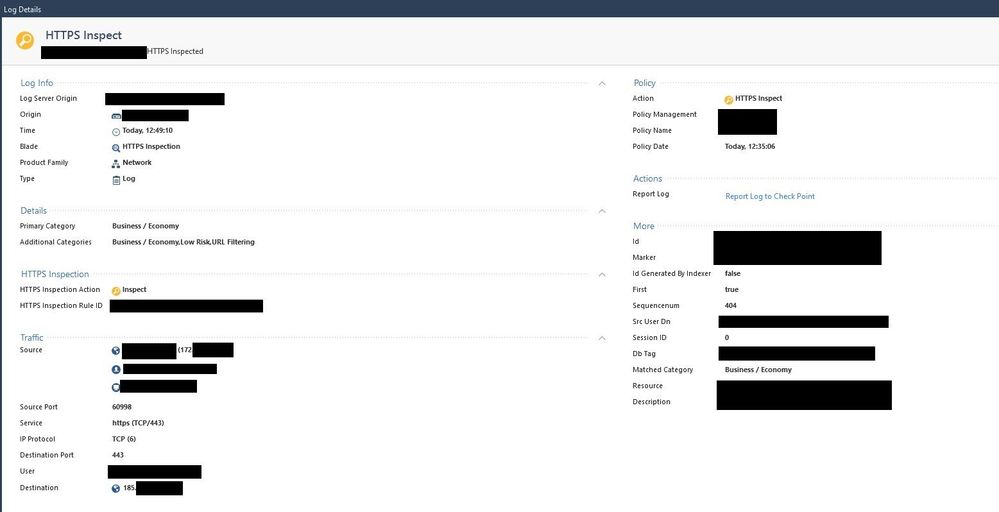
The connection in question gets HTTPS Inspected and the log is as follows:
And the "Accept" ("CPNotEnoughDataForRuleMatch") log looks as below:
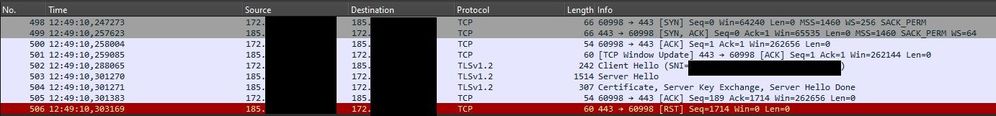
I tried to establish the connection with a Wireshark running on the client (not the firewall) and as far as I can see the handshake completes, but then it gets disconnected by a reset from the destination:
I have the same service on another endpoint WITHOUT HTTPS Inspection and there it connects fine.
So my question is: Is it possible that the packet somehow gets "malformed" in the HTTPS Inspection process and therefore the destination sends a reset back to us and kills the connection? Or is something different going on? I really can't figure it out!
Looking forward to your comments 🙂
Thanks!
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The error states there is no data in the connection, that is true according to the capture so the error is valid.
You state without https inspection connections it works so we should focus on that. Could start is to see if the chosen encryption ciphers are accepted on both sides. In the capture the source is the fw right? That is starting with syn?
-------
If you like this post please give a thumbs up(kudo)! 🙂
If you like this post please give a thumbs up(kudo)! 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, that's the client. I haven't done a capture on the firewall.
It seems like the Handshake and thus cipher suites goes through and it is after that, that the destination endpoint sends a reset packet. I just can't figure out why.
And again if I bypass HTTPSi it works, so my theory was that it had something to do with that...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like @Lesley said, you should check from the gateway (specifically from the gateway to the remote site) with tcpdump.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check out below links, hope it helps. In short, this is literally never CP issue, as 3 way handshake is not completing, but its not because of the fw, but rather the fact that server did not send back syn-ack.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just don't understand why it then works if I bypass HTTPSi... 😞
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But then it sounds like its httpsi issue...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now that I think about it, say if you have httpsi enabled, you can always add bypass rule for affected IPs/destinations.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah, you're right.
Are there any way of troubleshooting that myself or should I involve TAC? And is it okay to bypass destinations that causes problems? Obviously, it wont perform HTTPS Inspection on traffic between whatever source and destination hosts I have defined, but is it a known issue that HTTPSi in some situations will break the connection? It is not a general problem, but I do experience it occasionally.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yea, you said it exactly how I would put it. Not a generic problem, but it happens from time to time. Well...if destination causes problems, then I would NOT bypass it, better to involve TAC. However, if it does not cause issues, I would do it.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, it happens all the time for this specific destination and for now I have just created a bypass rule for it. I will consider getting TAC involved.
Thanks 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sounds good!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Focus on checking HTTPS inspection part, not the CPNotEnoughDataForRuleMatch error.
HTTPS inspection can go wrong between client <-> FW or FW <-> remote server
Mismatch in ciphers but also CA that is not up to date on FW.
-------
If you like this post please give a thumbs up(kudo)! 🙂
If you like this post please give a thumbs up(kudo)! 🙂
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 11 | |
| 7 | |
| 6 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 3 |
Upcoming Events
Thu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasFri 14 Feb 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 33: CPX 2025 terugblik!Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASThu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasFri 14 Feb 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 33: CPX 2025 terugblik!Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter