- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- AD-query failed with Microsoft Windows Server 2022
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
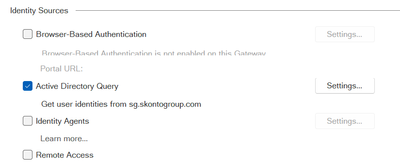
AD-query failed with Microsoft Windows Server 2022
Hello CheckMates,
with Windows Server 2022 Microsoft changed the default behaviour of the RPC authentication level.
Following this AD-query failed (remote login not possible, access roles not enforced etc.) Available in the knowledgebase is this article
Check Point response to CVE-2021-26414 - "Windows DCOM Server Security Feature Bypass"
There is a steatment "Check Point R&D is working on a permanent solution for this issue."
Any solutions for this problem or a timeline when available?
Wolfgang
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Windows Server 2022 is unfortunately still simply incompatible with ADQuery, there is no work around so you would need to use the Identity Collector instead of ADQuery:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
24 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is a workaround in the case. Did you see the link to the MS article in the comments?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@_Val_ yes, I see. But the solution is to lowering the security on the Microsoft site. I know identity collector is the better solution but at the moment we are using only AD-query.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you sure the workaround works on server 2022 as well and not only on previous versions having the update for CVE-2021-26414 ? The MS kb article states that the workaround will not be possible anymore in some times and server 2022 is not listed. So possibly server 2022 is already in this state.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@JeanMarc_C yes you're right. With 2022 this does not work. We tried this but AD query was failing again. Reading again Microsofts knowledgebase article let us realize that it's not supported with 2022 (same as you mentioned). I forgot about it to post here. The solution is to switch to Identity Collector.
There should be a hint in the documentation that AD query does no more work with domain controller on Microsoft Server 2022.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AD query on Microsoft Server 2022 wont never work or till Check Point will release the fix?
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looks like you have to install KB5005619 on Microsoft server 2022 and then you can set the mentioned registry value to disabled. But after Q2 2022 this will be no more available. Have a look at the timeline in KB5004442—Manage changes for Windows DCOM Server Security Feature Bypass (CVE-2021-26414)
@_Val_ please would you check internal regarding AD query and Microsoft Windows server 2022.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Wolfgang,
Unfortunately, there is no simple fix here to adjust AD Query to work with this security enhancement.
We are still investigating the amount of effort needed here, but I can say it will not take few weeks.
As the SK stated, this is a problem which only AD Query suffers from, and Identity Collector which uses different method for acquiring identities works with no change.
I will revise the SK with the needed info raised on this thread - thanks for sharing.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Royi, we appreciate the transparency.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
What solution or workaround would be for Gaia Embedded devices (15xx Appliances)? those don't have option to use Identity Collector.
Thanks,
Raitis Robeznieks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Share identities from a gateway that can.
This could even be a two-core VM off to the side running regular Gaia.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had a ticket with support for this, and there is an ETA to support server 2022 and the security strengthening according the MS KB for end of January 2022. In the meantime workaround or solution is to work with Identity collector (which is better than AD query), share identities between gateways, or use Identity Agent.
It is however not 100% clear if AD 2022 with the registry key change according MS KB is meant to work or not. In my case, on embedded R77.20, it does not work but change the status of the AD from "internal error" to "bad credential".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank You, PhoneBoy for your suggestion.
I have disabled AD Query for all embedded devices, and enabled them to get shared identities from those appliances, that use ID Collector.
Will see, how this will work. I was afraid, that using ID Sharing Identities will not work, it requests/traffic is not processed through GW, that is Identity source. (for example on-site local traffic between separated interfaces/subnets).
Best Regards,
Raitis
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Raitis, @SGInfra
Identity Sharing mechanism will allow more efficient way to save identities. For example, gateway which handle traffic for specific subnets, will get the identities which are part of this subnet only. This design allows each gateway to receive the needed identities only, and not process unneeded sessions.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Royi_Priov, and Thanks for Your advice.
Solution with Shared identities Works fine.
In our topology we have 4 GW running regular Gaia and 6 Gaia embedded appliances.
One of Regular Gaia is central GW for all other devices (sites) in star Community VPN.
I have pointed each Embedded device, to get shared Identities form Central GW and one other Regular Gaia device, that is related (As parrent) site for that branch.
Thanks also to PhoneBoy for provided solution.
B.R.
Raitis
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, SMB clients with just Quantum Spark appliances also need to buy and maintain a license for VM GAIA just for this task? I have not heard of any other vendor with this problem and forcing you to purchase additional licenses for a feature you are supposed to have already paid for. This is not good
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81.X alignment will allow SMB appliances to leverage Identity Collector, stay tuned for the EA (or enquire with your local SE).
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Royi_Priov,, Has SK been revised and updated?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@BeaconBits, yes:
To work without any functionality issues, follow the procedure in this Microsoft article:
https://support.microsoft.com/en-us/topic/kb5004442-manage-changes-for-windows-dcom-server-security-feature-bypass-cve-2021-26414-f1400b52-c141-43d2-941e-37ed901c769c
A fix might be needed to apply this procedure, please check "Availability" section in the above article.
Thanks,
Royi Priov
R&D Group manager, Infinity Identity
Royi Priov
R&D Group manager, Infinity Identity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
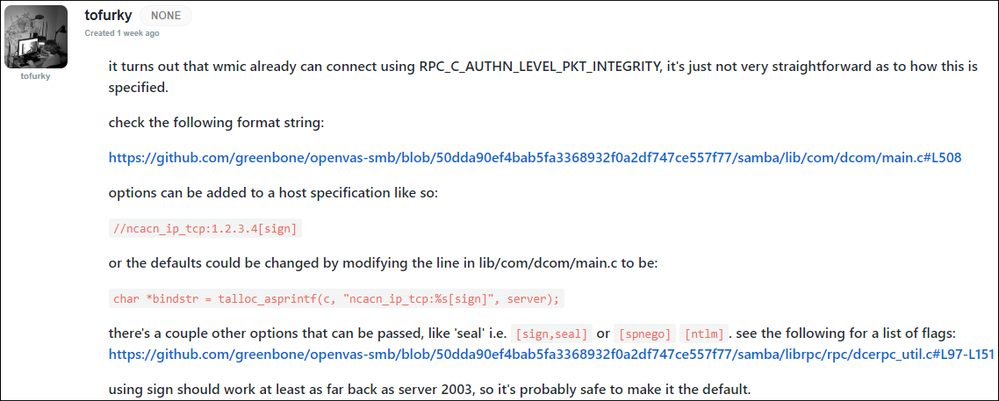
The method of setting the registry key unfortunately makes no difference on an up to date Windows 2022 AD server. Herewith the registry entry we set:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Ole\AppCompat]
"RequireIntegrityActivationAuthenticationLevel"=dword:00000000
Hoping R&D can provide a fix that remediates this problem, what's happened in the 6 months since Microsoft raised awareness of this upcoming change?
Perhaps developers could look to see how other libraries (eg Samba) handle the requirement?
PS: We are running R81 with NTLMv2, LDAPS and Kerberos encryption type aes256-cts-hmac-sha1-96.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Royi_Priov do you have an update to this yet?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There appears to be a custom fimrware r77.20.87 B127 that fixes this, anyone tried it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are there any news if Windows Server 2022 is now supported by AD Query?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
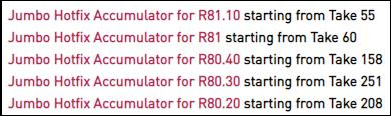
Yes, Jumbo Hotfix Accumulators include changes to make AD Query compatible with this.
Microsoft documented the changes with regards to DCOM hardening in the following knowledge base article:
Summary:
A Microsoft Windows Active Directory Domain Controller (AD DC) will, after being rebooted after the 14th of June 2022, no longer respond to non-signed DCOM packets when they arrive. One can implement a temporary work around to continue receiving and processing unsigned packets, but functionality of this work around ends on the 14th of March 2023.
How to implement temporary work around:
- Login to your AD DCs and make the following registry change, please reboot the DCs after making this adjustment for the change to take effect
- Start -> Run -> regedit
- Copy & paste the following registry key path in to the address bar of regedit:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Ole\AppCompat
- Create a new DWORD registry item called RequireIntegrityActivationAuthenticationLevel, with a decimal value of 0
CheckPoint, as many other vendors, took a while to refactor their code to make use of the new requirement. CheckPoint integrates to a wide variety of devices for identity awareness information and includes two methods to learn IPs of workstations joined to a domain provided by AD DCs. The ADQuery method uses DCOM to subscribe to Security Event logs which essentially inform the firewall of what user authentication sessions originated from what PCs and another which runs as an application on a workstation or server in the network and presents a consolidated stream of authentication events from all AD DCs to a firewall without it being individually configured for each DC in the network.
The change requires the installation of a JHA (Jumbo Hotfix Accumultator) which introduces support for the new method. This update is however only available for all versions in active support.
Example entry from the R80.40 JHA take 158 changelog confirming support for Microsoft's response to CVE-021-26414:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Windows Server 2022 is unfortunately still simply incompatible with ADQuery, there is no work around so you would need to use the Identity Collector instead of ADQuery:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 26 | |
| 19 | |
| 11 | |
| 8 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Wed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter