- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: 23500 and/or 23800 appliances
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
23500 and/or 23800 appliances
Hi checkmates,
anyone had experience with 23.5, and 23.8k appliances? If yes in what configuration?
27 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
23800, R80.10 VSX, < 10 VSes, static routing, peaking 10 Gbps, bond to the core. Nothing too much with fancy blades. FW, ips, ia. So far so good. Nothing to complain about. Just ordered another pair to replace 13800 ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it single 23800 VSX or cluster?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Kaspar, I assume your configuration is single 238k model?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, Easter break from work.. no it's a cluster.:)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have 2 VRRP Clusters on 23800 Appliances as datacenter core firewalls with a lot of VLANs (150+) on 10GB Bonds and actually have issues with the VRRP failover (routed seems to hang, case open) as well as some false positives on the power supply monitoring via snmp. Other than that, those applicances are very fast, but cost a fortune 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
why vrrp not ccp?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've deployed a number of those with R77.30 VSX in ClusterXL. Number of VS' on each cluster with variety of configurations.
Generally, all is well. The only thing of note was an incorrect memory reporting by show asset all command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Alex,
We have many 23500/23800 deployments, in several different scenarios (with and without Blades, clusters -usually ClusterXL-, regular Gateways and VSX...)
Are you looking for anything specific? ![]() Hardware related issues maybe?
Hardware related issues maybe?
Regards!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Needed to know memory/CPU concerns/considerations and performance before purchase commitment. I settled with 2x23.5(s). Now configuration fun: since VS licensing comes as VSLS, does it mean to fully utilize functionality VSX gateways have to be configured in load sharing mode, not HA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would look at it differently: when and if you'll get to the third appliance, you'll have an option of taking advantage of VSLS.
With 2 appliances, the HA is a better option (personal opinion). Otherwise, you'll have to keep track on utilization in order to avoid overloading the systems.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Valid point however theoretically, if gateway has enough power to run 10 VM(s) in VLSM mode it should be fine since only half of active VS(s) will be running on one gateway at given time (5act and 5 standby on each? What would be the breaking point to consider 3rd VSX gateway?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When VS' were 32 bit, it was easier to answer this question, since we knew the maximum allocated vRAM.
With 64 bit VSX memory consumption is dynamic, so you'll have to monitor total active (non-cached) memory consumption of the each member of VSX cluster is lower than 50%. Otherwise, when one of the appliances is down, you may end-up with underperforming VS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good info, thank you. Anything else to watch for or be prepared for before I disappear in VSX forest?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just that you'll lose the WebUI when you designate units as VSX. Not the end of the world, but for consistency sake, pre-configure both units same way and check the diff between configs. Primarily applicable to routing, if you are planning to use any advance features. And, of course, NTP sync the units before clustering them. If your Check Point infrastructure is not huge, consider configuring static DNS entries for all of its components on each unit as well as verify access to the Internet for licensing and CPUSE.
Best of luck!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cool stuff, info I was looking for, thank you. One more Q: I am planning to have 2 VSX gateways in SL mode with VS(s) in HA mode on them. Theoretically should work? Crazy, stupid or potential subside?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You mean VSX' in LS and VS' in HA? I'd suggest asking Kaspars Zibarts, as he is working with VSX more than I do, but if my recollection is correct, VSLS is enabling 3 instances of the same VS, active, standby and a backup. Not sure what that does to resource consumption, but I think it'll be on par with HA with the backup version being normally suspended.
The only advantages to this approach is the ability to rapidly expand the cluster without changing its mode and equal stress of the hardware.
From the point of view of redundancy and failover time, I do not believe you'll gain anything.
Try to find an ARTG articles on VSX, those may come handy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir, you are correct regarding configuration. Do you know where I can find information on why some VSX CLI commands blocked? There is no explanation why, it is simply blocked? Particular command I need is to add brdge.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could it be that you have chosen one of the preset VSX models instead of "Custom Properties"?

And are those interfaces defined as "Physical Interfaces"?

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes and yes :only custom template and can see physical interfaces but no love from bridging side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hm..
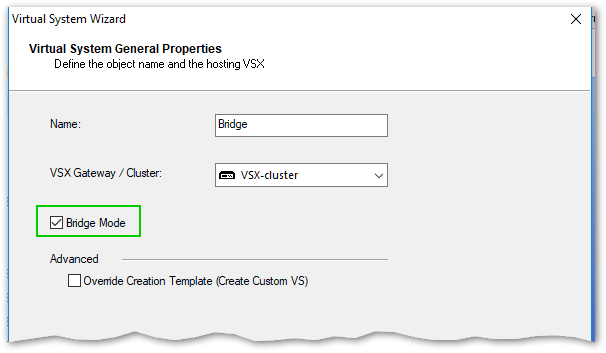
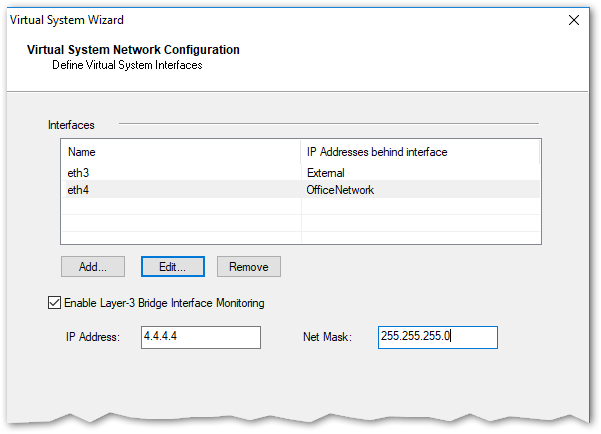

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know about this one, it creates VS in bridge mode. I am looking to create bridge, option available via Gaia UI before VSX disables it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I understand what you are trying to accomplish correctly, I suspect you will not succeed in it.
You are attempting to create a bridge and present it to the VSX as a fait accompli to VS0.
As far as I understand it you can create bundles, trunks, subinterfaces and define routing parameters, but you cannot create a bypass bridge.
How would you manage security on such a bridge?
What is the reason for creating it outside of the context of VS residing on the cluster?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bridging 2 physical interfaces with goal to connect each interface to upstream border routers, (different ISPs). BTW, creating bridge in Gaia UI before creating VSX keeps configuration in CLI and allowed me to crate VS and attach it to the bridge interface created before VSX took over. Setting physical connections to see if it behaves.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you post a screenshot of the VSX topology with bridge present, VS with the bridge attached to it as well as sanitized gaia config?
If you have more than one VS configured, can you check if this pre-defined interface is present in the context of each VS?
I am curious to see how it looks.
When you are saying that WebUI configured bridge is present in CLI, are you implying that the one configured in SmartConsole is not?
Have you published and installed the policy and then confirmed its absence from config?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I will, trying to ping thru 2 bridges interfaces This is from CLI none of the commands available to add vi cli after Gaia UI is disabled:
Pining through the bridge interfaces eth1/eth2 does not work, looks like VS needed to control bridging:
add bridging group 23
add bridging group 23 interface eth2
add bridging group 23 interface eth3
……
set interface br23 comments "br23"
set interface br23 state on
……
set interface eth2 link-speed 1000M/full
set interface eth2 state on
set interface eth2 auto-negotiation on
set interface eth2 mtu 1500
set interface eth3 link-speed 1000M/full
set interface eth3 state on
set interface eth3 auto-negotiation on
set interface eth3 mtu 1500
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir,
Did not make it work yet. Wonder why vBridge option does not exist in VSX only VS in bridge mode. With VS in bridged mode managed to create STP loop, had to disable interfaces. Did not have time to work on this further.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is a pretty good write-up on the subject in "Check Point VSX Administration Guide R80.10" on page 44.
Highly recommend giving it a one-over.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 23 | |
| 23 | |
| 12 | |
| 12 | |
| 8 | |
| 7 | |
| 6 | |
| 6 | |
| 6 | |
| 5 |
Upcoming Events
Wed 05 Nov 2025 @ 11:00 AM (EST)
TechTalk: Access Control and Threat Prevention Best PracticesThu 06 Nov 2025 @ 10:00 AM (CET)
CheckMates Live BeLux: Get to Know Veriti – What It Is, What It Does, and Why It MattersTue 11 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERTue 11 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


