- Products
- Learn
- Local User Groups
- Partners
- More
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
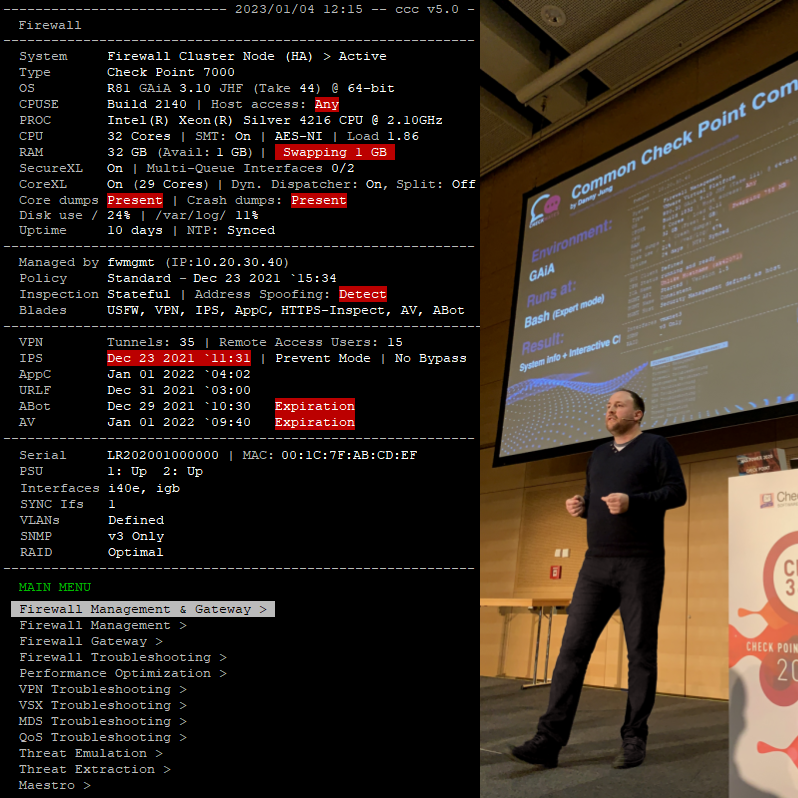
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle.crt https://dannyjung.de/ccc|zcat > /usr/bin/ccc && chmod +x /usr/bin/ccc;. ~/.bashrc
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle
Hi, Denny,
can you insert the version number into the ccc.zip. So, we can see the current version.
Thanks in advance.
@6dd15084-b97a-4 No, this is a community development @Danny is the author.
Concerning the second question, you will understand the use once you open it the very first time.
@6dd15084-b97a-4 No, this is a community development
@Danny is the author.
Concerning the second question, you will understand the use once you open it the very first time.
Hello,
Great job!
If I can make some suggestions for improvement:
- adding the Jumbo HF installed on top the menu (with alreday gathered information)
- AV / URL filtering / Abot version if possible
Regards
Found 1 more very useful thing I use.
Ping Sweep:
for i in {97..110}; do ping -c 1 -W 1 10.10.10.$i | grep 'from'; done
Very fine indeed! A cosmetical issue: My single GW R80.10 shows "No product has flag" when cpstat is issued, same on CLI - the equivalent R77.30 does not (cpstat -f all ha on R77.30 CLI gives "-" for all table values):
[Expert@GW_80.10:0]# ccc
No product has flag 'ha'
No product has flag 'ha'
No product has flag 'ha'
--------------------------------------------------v1.4--
ccc > GW_80.10
--------------------------------------------------------
System: Firewall Gateway
Appliance / Server: VMware Virtual Platform
Version: Check Point Gaia R80.10
Uptime: 22 days
Gateway managed by: SMS7520 (IP: 172.2......
Very fine indeed! A cosmetical issue: My single GW R80.10 shows "No product has flag" when cpstat is issued, same on CLI - the equivalent R77.30 does not (cpstat -f all ha on R77.30 CLI gives "-" for all table values):
[Expert@GW_80.10:0]# ccc
No product has flag 'ha'
No product has flag 'ha'
No product has flag 'ha'
--------------------------------------------------v1.4--
ccc > GW_80.10
--------------------------------------------------------
System: Firewall Gateway
Appliance / Serve
I freely admit that it does really not make much sense, but i have tested it - again - on a SMB 730, just for fun ![]() :
:
[Expert@seven-eleven]# ccc
/usr/bin/ccc: line 13: /etc/profile.d/CP.sh: No such file or directory
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
--------------------------------------------------v1.4--
ccc > seven-eleven
--------------------------------------------------------
System: Firewall Gateway
Appliance / Server: CP 730
Version: Check Point GAiA Embedded R77.20
Uptime: 3 minutes
Gateway managed by: cp_sys_ExternalLogServer_0 (IP: 172.2...
I freely admit that it does really not make much sense, but i have tested it - again - on a SMB 730, just for fun ![]() :
:
[Expert@seven-eleven]# ccc
/usr/bin/ccc: line 13: /etc/profile.d/CP.sh: No such file or directory
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/us
The StandAlone 700 ccc shows the external Log server IP as Management IP - but a managed 1200R ccc also shows the SMS name:
[Expert@zwelfhundertr]# ccc
/usr/bin/ccc: line 13: /etc/profile.d/CP.sh: No such file or directory
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
--------------------------------------------------v1.4--
ccc > zwelfhundertr
--------------------------------------------------------
System: Firewall Gateway
Appliance / Server: CP 1200R
Version: Check Point GAiA Embedded R77.20
Uptime: 10 days
Gateway managed by: SMS7520 (IP: 172.2...
The StandAlone 700 ccc shows the external Log server IP as Management IP - but a managed 1200R ccc also shows the SMS name:
[Expert@zwelfhundertr]# ccc
/usr/bin/ccc: line 13: /etc/profile.d/CP.sh: No such file or directory
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not found
/usr/bin/ccc: line 31: tput: command not
Yes i do know that Embedde GAiA is not supported - i have explained that it does really not make much sense to run it there... I just wanted to check some of the used commands that do make sense in that environment ![]() .
.
Danny I see some strange behavior when trying v1.6.
If I understood the environment expressions correctly, it should just check if CP.sh file is present on the device. But even with CP.sh present, it shows "Unsupported Environment" on MDS.
On MDS R77.30 + JHA_266:
[Expert@MDS:0]# ls -l /usr/bin/ccc
-rwxr-x--- 1 admin root 26609 Apr 11 08:22 /usr/bin/ccc
[Expert@MDS:0]# ls -l /etc/profile.d/CP.sh
-rwxr-xr-x 1 admin root 90 Dec 1 2014 /etc/profile.d/CP.sh
[Expert@MDS:0]#cat /etc/profile.d/CP.sh
if [ -r /opt/CPshrd-R77/tmp/.CPprofile.sh ]; then
. /opt/CPshrd-R77/tmp/.CPprofile.sh
fi
[Expert@MDS:0]# ccc
zcat: stdin: unexpected end of file
Unsupported Environment
[Expert@MDS:0]#
On FW R77.20:
[Expert@FW:0]# ls -l /usr/bin/ccc
-rwxr-x--- 1 admin root 26609 Apr 11 08:22 /usr/bin/ccc
[Expert@FW:0]# ls -l /etc/profile.d/CP.sh
-rwxr-xr-x 1 admin root 90 Aug 9 2014 /etc/profile.d/CP.sh
[Expert@FW:0]# cat /etc/profile.d/CP.sh
if [ -r /opt/CPshrd-R77/tmp/.CPprofile.sh ]; then
. /opt/CPshrd-R77/tmp/.CPprofile.sh
fi
[Expert@FW:0]# ccc
zcat: stdin: unexpected end of file
/usr/bin/ccc: line 47: test: too many arguments
/usr/bin/ccc: line 48: test: too many arguments
--------------------------------------------------v1.6--
ccc > FW
--------------------------------------------------------
System: Firewall Cluster Node (HA) - Standby
Appliance / Server: Check Point 12400
Version: Check Point Gaia R77.20
Uptime: 188 days
Gateway managed by: CMA (IP: 1.1.2.3)
--------------------------------------------------------
[ MAIN MENU ]
Firewall-Management & Gateway >
Firewall-Management >
Firewall Gateway >
ClusterXL Troubleshooting >
ClusterXL Troubleshooting >
Multi-Core Performance Tuning >
VSX Troubleshooting >
MDS Troubleshooting >
Standalone Firewall & Management >
Threat Emulation >
Threat Extraction >
Also, "Usage: ..." is not displayed for me. Should it be visible?
Danny I see some strange behavior when trying v1.6.
If I understood the environment expressions correctly, it should just check if CP.sh file is present on the device. But even with CP.sh present, it shows "Unsupported Environment" on MDS.
On MDS R77.30 + JHA_266:
[Expert@MDS:0]# ls -l /usr/bin/ccc
-rwxr-x--- 1 admin root 26609 Apr 11 08:22 /usr/bin/ccc
[Expert@MDS:0]# ls -l /etc/profile.d/CP.sh
-rwxr-xr-x 1 admin root 90 Dec 1 2014 /etc/profile.d/CP.sh
[Expert@MDS:0]#cat /etc/pro
...;On R77.30 1.6 is working real fine ![]() - but my R80.10 SMS gives:
- but my R80.10 SMS gives:
[Expert@SMS8010:0]# ccc
Unsupported Environment
[Expert@SMS8010:0]# cat /etc/profile.d/CP.sh
if [ -r /opt/CPshrd-R80/tmp/.CPprofile.sh ]; then
. /opt/CPshrd-R80/tmp/.CPprofile.sh
fi
On R77.30 1.6 is working real fine ![]() - but my R80.10 SMS gives:
- but my R80.10 SMS gives:
;
[Expert@SMS8010:0]# ccc
Unsupported Environment
[Expert@SMS8010:0]# cat /etc/profile.d/CP.sh
if [ -r /opt/CPshrd-R80/tmp/.CPprofile.sh ]; then
. /opt/CPshrd-R80/tmp/.CPprofile.sh
fi
This script has really evolved very much during the last weeks ![]() ! My SMS now again likes it, but last line seems not alright:
! My SMS now again likes it, but last line seems not alright:
ccc > SMS8010
--------------------------------------------------------
System: SmartEvent Server
Appliance / Server: VMware Virtual Platform
Version: Check Point Gaia R80.10
Uptime: 28 days
Gateway managed by: localhost (IP: )
This is a SMS with enabled SmartEvent only.
This script has really evolved very much during the last weeks ![]() ! My SMS now again likes it, but last line seems not alright:
! My SMS now again likes it, but last line seems not alright:
ccc > SMS8010
--------------------------------------------------------
System: SmartEvent Server
Appliance / Server: VMware Virtual Platform
Version: Check Point Gaia R80.10
Uptime: 28 days
Gateway managed by: localhost (IP: )
This is a SMS with enabled SmartEvent only.
;I'm aware of this. I'll develop a better checking routine to clearly identify which type of system the script is actually running on. Neither Check Point's Healthcheck script nor CPview utility do it any better at the moment.
I'm aware of this. I'll develop a better checking routine to clearly identify which type of system the script is actually running on. Neither Check Point's Healthcheck script nor CPview utility do it any better at the moment.
;Yes, i know 😞 Looks like only many greps on $CPDIR/registry/HKLM_registry.data will provide all information.
Another nice but barely documented command also could help here:
cpprod_util FwIsFirewallModule
cpprod_util FwIsActiveManagement
Only that the following does not work as i did expect it to:
cpprod_util FwIsReportingServerMgmt
cpprod_util FwIsLogConsolidatorMgmt
cpprod_util FwIsLogServer
as it all gives 0 on my SMS. I wonder if we could somehow learn about the string arguments for
cpprod_util CPPROD_CheckProduct ....
Another nice but barely documented command also could help here:
cpprod_util FwIsFirewallModule
cpprod_util FwIsActiveManagement
Only that the following does not work as i did expect it to:
cpprod_util FwIsReportingServerMgmt
cpprod_util FwIsLogConsolidatorMgmt
cpprod_util FwIsLogServer
as it all gives 0 on my SMS. I wonder if we could somehow learn about the string arguments for
cpprod_util CPPROD_CheckProduct ....;
I found another way:
[Expert@SMS8010:0]# cpprod_util CPPROD_GetKeyValues Products 0
IDA
KAV
CPFC
FW1
SecurePlatform
CPinfo
DIAG
SmartPortal
Reporting Module
CPuepm
VSEC
SmartLog
MGMTAPI
R7520CMP
R7540CMP
R7540VSCMP
R76CMP
SFWR77CMP
R77CMP
R75CMP
NGXCMP
EdgeCmp
SFWCMP
FLICMP
SFWR75CMP
CPUpdates
[Expert@GW_80.10:0]# cpprod_util CPPROD_GetKeyValues Products 0
IDA
CPFC
FW1
SecurePlatform
CPinfo
DIAG
PPACK
CVPN
CPUpdates
I found another way:
[Expert@SMS8010:0]# cpprod_util CPPROD_GetKeyValues Products 0;
IDA
KAV
CPFC
FW1
SecurePlatform
CPinfo
DIAG
SmartPortal
Reporting Module
CPuepm
VSEC
SmartLog
MGMTAPI
R7520CMP
R7540CMP
R7540VSCMP
R76CMP
SFWR77CMP
R77CMP
R75CMP
NGXCMP
EdgeCmp
SFWCMP
FLICMP
SFWR75CMP
CPUpdates
[Expert@GW_80.10:0]# cpprod_util CPPROD_GetKeyValues Products 0
IDA
CPFC
FW1
SecurePlatform
CPinfo
DIAG
PPACK
CVPN
CPUpdates
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle.crt https://dannyjung.de/ccc|zcat > /usr/bin/ccc && chmod +x /usr/bin/ccc;. ~/.bashrc
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
