- Products
- Learn
- Local User Groups
- Partners
- More
Policy Insights and Policy Auditor in Action
19 November @ 5pm CET / 11am ET
Access Control and Threat Prevention Best Practices
Watch HereOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
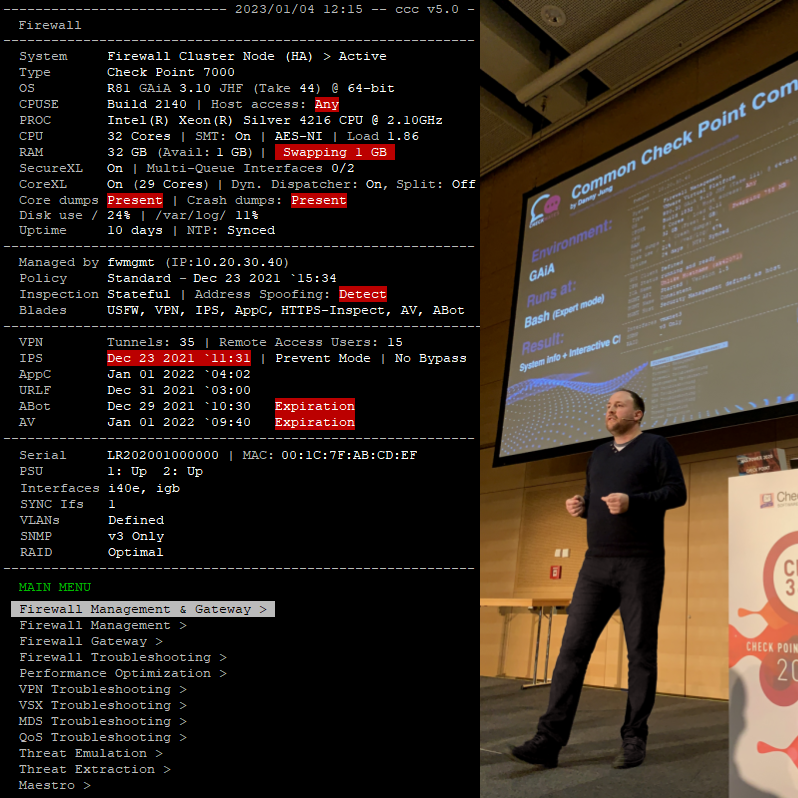
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle.crt https://dannyjung.de/ccc|zcat > /usr/bin/ccc && chmod +x /usr/bin/ccc;. ~/.bashrc
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle
Hi there, I don't see an actual download for the script, can I just save the text in notepad and save it as ccc.sh, move it to my gateway and execute it by ./ccc.sh?
Thanks in advance and excellent job on the script and great collaboration between everyone!
Hi there, I don't see an actual download for the script, can I just save the text in notepad and save it as ccc.sh, move it to my gateway and execute it by ./ccc.sh?
Thanks in advance and excellent job on the script and great collaboration between everyone!
;On R80.30 I see some problems.
1. last -20 -w Show last 20 logins by name
[Executing:]# last -20 -w
last: invalid option -- w
Usage: last [-num | -n num] [-f file] [-t YYYYMMDDHHMMSS] [-R] [-x] [-o] [username..] [tty..]
Done.
2. tail $FGDIR/log/fgd.elg Show last 10 entries in QoS log
[Executing:]# tail /opt/CPsuite-R80.30/fg1/log/fgd.elg
tail: cannot open `/opt/CPsuite-R80.30/fg1/log/fgd.elg' for reading: No such file or directory
Done.
On R80.30 I see some problems.
1. last -20 -w Show last 20 logins by name
[Executing:]# last -20 -w
last: invalid option -- w
Usage: last [-num | -n num] [-f file] [-t YYYYMMDDHHMMSS] [-R] [-x] [-o] [username..] [tty..]
Done.
2. tail $FGDIR/log/fgd.elg Show last 10 entries in QoS log
[Executing:]# tail /opt/CPsuite-R80.30/fg1/log/fgd.elg
tail: cannot open `/opt/CPsuite-R80.30/fg1/log/fgd.elg' for reading: No such file or directory
Done.
;
Maybe you can also add treesize, a script I have on all the MDS servers I manage. It looks like this (I picked this one up a while back):
-----------
du -k --max-depth=1 | sort -nr | awk '
BEGIN {
split("KB,MB,GB,TB", Units, ",");
}
{
u = 1;
while ($1 >= 1024) {
$1 = $1 / 1024;
u += 1
}
$1 = sprintf("%.1f %s", $1, Units[u]);
print $0;
}
'
---------
Maybe you can also add treesize, a script I have on all the MDS servers I manage. It looks like this (I picked this one up a while back):
-----------
du -k --max-depth=1 | sort -nr | awk '
BEGIN {
split("KB,MB,GB,TB", Units, ",");
}
{
u = 1;
while ($1 >= 1024) {
$1 = $1 / 1024;
u += 1
}
$1 = sprintf("%.1f %s", $1, Units[u]);
print $0;
}
'
---------
;I love the new colors - great job!
At the moment the script shows all commands an all devices even if there are no relevant blades active on the device where you are executing the script.
For example: with "enabled_blades" you can check if vpn is active or not. If not you do not need th offer vpn relevant commands.
The same I can imagine with ips, threatemulation etc...
BTW: I am missing threatemulation commands. Do you need some? ![]()
Further it would be helpful to identify when the script starts if the system where the script is running on is a management, a log server or a gateway.
If it is a gateway: is it a cluster, is it vsx and which blades are active?
With this set of information you can choose which commands you will show in the menu.
Maybe I can build some code on the weekend.
Cheers
Sven
I love the new colors - great job!
At the moment the script shows all commands an all devices even if there are no relevant blades active on the device where you are executing the script.
For example: with "enabled_blades" you can check if vpn is active or not. If not you do not need th offer vpn relevant commands.
The same I can imagine with ips, threatemulation etc...
BTW: I am missing threatemulation commands. Do you need some? ![]()
Further it would be helpful to identif
...;As we are stepping into color era now, I would suggest to mark "dangerous" commands in red or orange color.
25 - fwaccel off - Disable SecureXL acceleration"
30 - fw unloadlocal; fw stat - Unload security policy on localhost"
36 - fw amw unload; fw stat -b AMW - Disable Threat Prevention"
47 - clusterXL_admin down - Create ClusterXL faildevice"
70 - mdsstop - Stop Multi-Domain Server"
72 - mdsstop_customer <DMS_ID or DMS_IP or DMS_Name> - Stop specific DMS
74 - cpwd_admin stop -name FWM -path "FWDIR/bin/fw" -command "fw kill fwm" - Stop Firewall Management only"
Another possibility is to use green color for commands that enable/turn on something. So, there could be several types of commands - informational (cyan), turn off / stop (red), and turn on / start (green).
As we are stepping into color era now, I would suggest to mark "dangerous" commands in red or orange color.
...;25 - fwaccel off - Disable SecureXL acceleration"
30 - fw unloadlocal; fw stat - Unload security policy on localhost"
36 - fw amw unload; fw stat -b AMW - Disable Threat Prevention"
47 - clusterXL_admin down - Create ClusterXL faildevice"
70 - mdsstop - Stop Multi-Domain Server"
72 - mdsstop_customer <DMS_ID or DMS_IP or DMS_Name> - Stop specific DMS
74 - cpwd_admin stop -name FWM -
echo " ${BOLD}76${NORM} - ${WARN}cpwd_admin stop -name FWM -path "$FWDIR/bin/fw" -command "fw kill fwm"${NORM} - Stop Firewall Management only"
you have "$FWDIR/bin/fw" ...missing the "m" on the end?
I like the system information when you start the script and added a litte improvement:
# Variables
...
MGMTIP=$(cat $CPDIR/registry/HKLM_registry.data | grep ICAip | awk '{print $2}')
...
and in the system output section:
echo "-------------------------------------------------"
echo " ${BOLD}Common Check Point Commands (ccc) v1.1${NORM}"
echo "-------------------------------------------------"
echo " System: ${BOLD}${SYSTEM}${NORM}"
echo " Appliance / Server: ${BOLD}${TYPE}${NORM}"
echo " Version: ${BOLD}${VERSION}${NORM}"
echo " Uptime: ${BOLD}${UPTIME}${NORM}"
if [[ $($CPDIR/bin/cpprod_util FwIsFirewallModule 2> /dev/null) == *"1"* ]]; then echo " Gateway managed by: $MGMT (IP: ${MGMTIP:1:${#MGMTIP}-2})"
elif [[ $($CPDIR/bin/cpprod_util FwIsVSX 2> /dev/null) == *"1"* ]]; then echo " Gateway managed by: $MGMT (IP: ${MGMTIP:1:${#MGMTIP}-2})"
fi
echo "-------------------------------------------------"
the command above shows you the management name and ip address of a gateway/VSX.
I like the system information when you start the script and added a litte improvement:
# Variables
...
MGMTIP=$(cat $CPDIR/registry/HKLM_registry.data | grep ICAip | awk '{print $2}')
...
and in the system output section:
echo "-------------------------------------------------"
echo " ${BOLD}Common Check Point Commands (ccc) v1.1${NORM}"
echo "-------------------------------------------------"
echo " System: ${BOLD}${SYSTEM}${NORM}"
Hmmm - tried it on my SMS:
----------
[Expert@SMS8010:0]# ccc
cat: /opt/CPsuite-R80/fw1/conf/masters: No such file or directory
grep: /opt/CPsuite-R80/fw1/state/local/AMW/local.IPS.set: No such file or directory
date: invalid date `@'
--------------------------------------------------v1.2--
ccc > SMS8010
--------------------------------------------------------
System: SmartEvent Server
Appliance / Server: VMware Virtual Platform
Version: Check Point Gaia R80.10
Uptime: 1 day
--------------------------------------------------------
[ MAIN MENU ]
---------
I find the error message on start rather confusing - but strangest phenomenon is
System: SmartEvent Server
In SMS object, SmartEvent Server and Correlation Unit are disabled, evconfig also shows everything disabled... Still, $CPDIR/bin/cpprod_util RtIsRt gives 1, same as $CPDIR/bin/cpprod_util FwIsFirewallMgmt.
Hmmm - tried it on my SMS:
----------
[Expert@SMS8010:0]# ccc
cat: /opt/CPsuite-R80/fw1/conf/masters: No such file or directory
grep: /opt/CPsuite-R80/fw1/state/local/AMW/local.IPS.set: No such file or directory
date: invalid date `@'
--------------------------------------------------v1.2--
ccc > SMS8010
--------------------------------------------------------
System: SmartEvent Server
Appliance / Server: VMware Virtual Platform
Version: Check Point Gaia R80.10
Uptime: 1 day
----------
Implemented in version 1.3
Note: Even Check Point's cpview and healthcheck script v4.08 and cpconfig's 'Automatic start of Check Point Products' detect SmartCenter/SmartEvent Servers wrong. I fixed that by checking for the CPSEMD SmartEvent process instead.
Implemented in version 1.3
Note: Even Check Point's cpview and healthcheck script v4.08 and cpconfig's 'Automatic start of Check Point Products' detect SmartCenter/SmartEvent Servers wrong. I fixed that by checking for the CPSEMD SmartEvent process instead.
;In the MDS part I did see mdsstart and mdsstart_customer, but I did not see the mdsstart -m and mdsstop -m to only stop the MDS itself, but not the domains.
Just one suggestion: In case you have enabled sandblast on your firewall, it could be useful to watch stuck files in the local Check Point postfix mail queue. I implemented this on those firewalls with a bash alias: mailq='/opt/postfix/usr/sbin/postqueue -p -c /opt/postfix/etc/postfix/' Maybe this is useful for adding to the ccc script?
Maybe a funny fact about the name of the script ccc: CCC is in Germany the acronym for the Chaos Computer Club 🙂
Just one suggestion: In case you have enabled sandblast on your firewall, it could be useful to watch stuck files in the local Check Point postfix mail queue. I implemented this on those firewalls with a bash alias: mailq='/opt/postfix/usr/sbin/postqueue -p -c /opt/postfix/etc/postfix/' Maybe this is useful for adding to the ccc script?
Maybe a funny fact about the name of the script ccc: CCC is in Germany the acronym for the Chaos Computer Club 🙂
;Hi Danny,
thanks for adding TE support.
Nummer 82 would look much nicer in this way:
echo "Global file throughput (TE+AV): $(tecli sh th m) | $(tecli sh th h) | $(tecli sh th d)"
An other nice command I like is
tecli s e e
It shows the running emulations and their states.
Additionally I would be helpful to have a command that is monitoring the mailqueune. I do not have access to my testlab, so I can not provide the relevant command, sorry...
Thanks Sven
Hi Danny,
thanks for adding TE support.
Nummer 82 would look much nicer in this way:
echo "Global file throughput (TE+AV): $(tecli sh th m) | $(tecli sh th h) | $(tecli sh th d)"
An other nice command I like is
tecli s e e
It shows the running emulations and their states.
Additionally I would be helpful to have a command that is monitoring the mailqueune. I do not have access to my testlab, so I can not provide the relevant command, sorry...
Thanks Sven
;First of all, I love this script ! Thanks a lot ![]()
Can we add another command here:
echo " ${BOLD}76${NORM} - ${WARN}cpwd_admin stop -name FWM -path "$FWDIR/bin/fw" -command "fw kill fwm"${NORM} - Stop Firewall Management only"
echo " ${BOLD}77${NORM} - ${ENAB}cpwd_admin start -name FWM -path "$FWDIR/bin/fwm" -command "fwm"${NORM} - Start Firewall Management only"
NEW echo " ${BOLD}XX${NORM} - ${WARN}cpwd_admin stop -name FWM -path "$FWDIR/bin/fw" -command "fw kill fwm"; sleep 2;cpwd_admin start -name FWM -path "$FWDIR/bin/fwm" -command "fwm"${NORM} - Restart Firewall Management only"
Thanks ![]()
First of all, I love this script ! Thanks a lot ![]()
Can we add another command here:
echo " ${BOLD}76${NORM} - ${WARN}cpwd_admin stop -name FWM -path "$FWDIR/bin/fw" -command "fw kill fwm"${NORM} - Stop Firewall Management only"
echo " ${BOLD}77${NORM} - ${ENAB}cpwd_admin start -name FWM -path "$FWDIR/bin/fwm" -command "fwm"${NORM} - Start Firewall Management only"
NEW echo " ${BOLD}XX${NORM} - ${WARN}cpwd_admin stop -name FWM -path "$FWDIR/bin/fw" -command "fw
...;Thanks for the suggestion! As you just want to run two commands after another, simply enter the relevant numbers after another. From my experience two seconds might not be enough to re-initiate the starting process after stopping it. This needs to be monitored by the admin in charge while executing such commands.
Thanks for the suggestion! As you just want to run two commands after another, simply enter the relevant numbers after another. From my experience two seconds might not be enough to re-initiate the starting process after stopping it. This needs to be monitored by the admin in charge while executing such commands.
;Hi Danny,
I checked the new Identity Awareness commands.
On dayly basis I use more often specifiy searches instead of "pep show user all" or "pdp monitor all".
What about adding some functions for more user interaction?
54 # Functions
55
56 pep_user_query () {
57 echo "Query Identity Awareness for specific"
58 echo "1) Match entries with <username>"
59 echo "2) Match entries with machine <machine name>"
60 echo "3) Match entries that were updated by the given PDP"
61 echo "4) Match entries of clients with specific Client ID"
62 echo "5) Match entries that match full or partialy the given uid"
63 echo "6) Match entries with given group"
64 echo "7) Match entries with machine group"
65 echo "8) Match entries with given compliance"
66 echo "9) Match entries with given identity role"
67
68 echo
69 echo -en "Your choise: "; read ia
70 echo -en "Searchstring: "; read search
71
72 case $ia in
73 1) pep show u q usr $search
74 ;;
75 2) pep show u q mchn $search
76 ;;
77 3) pep show u q pdp $search
78 ;;
79 4) pep show u q cid $search
80 ;;
81 5) pep show u q uid $search
82 ;;
83 6) pep show u q ugrp $search
84 ;;
85 7) pep show u q mgrp $search
86 ;;
87 8) pep show u q cmp $search
88 ;;
89 9) pep show u q role $search
90 ;;
91 esac
92
93 }94
95 pdp_monitor_query () {
96 echo "Query PDP Monitor for specific"
97 echo "1) user - print sessions filtered by user name"
98 echo "2) ip - print sessions filtered by ip"
99 echo "3) s_port - print sessions filtered by assigned source port (MUH sessions only)"
100 echo "4) machine - print sessions filtered by machine name"
101 echo "5) mad - print sessions that are from managed asset machines"
102 echo "6) client_type - print sessions filtered by client type"
103 echo "7) groups - print sessions filtered by groups (user/machine)"
104 echo "8) cv_ge - print sessions that the client version is greater (or equal) from given version"
105 echo "9) cv_le - print sessions that the client version is less (or equal) from given version"
106
107 echo
108 echo -en "Your choise: "; read ia
109 echo -en "Searchstring: "; read search
110
111 case $ia in
112 1) pdp monitor user $search
113 ;;
114 2) pdp monitor ip $search
115 ;;
116 3) pdp monitor s_port $search
117 ;;
118 4) pdp monitor machine $search
119 ;;
120 5) pdp monitor mad $search
121 ;;
122 6) pdp monitor client_type $search
123 ;;
124 7) pdp monitor groups $search
125 ;;
126 8) pdp monitor cv_ge $search
127 ;;
128 9) pdp monitor cv_le $search
129 ;;
130 esac
131 }[...]
218 echo " ${BOLD}98${NORM} - ${CYAN}pep show user QUERY{NORM} - Identity Awareness > Show specific sessions"
219 echo " ${BOLD}99${NORM} - ${CYAN}pdp monitor QUERY{NORM} - Identity Awareness > Show specific sessions"[...]
510 98) pep_user_query
511 ;;
512 99) pdp_monitor_query
513 ;;[...]
Hi Danny,
I checked the new Identity Awareness commands.
On dayly basis I use more often specifiy searches instead of "pep show user all" or "pdp monitor all".
What about adding some functions for more user interaction?
...;54 # Functions
55
56 pep_user_query () {
57 echo "Query Identity Awareness for specific"
58 echo "1) Match entries with <username>"
59 echo "2) Match entries with machine <machine name>"
60 echo "3) Match entries that were updated by the given PDP"
61
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle.crt https://dannyjung.de/ccc|zcat > /usr/bin/ccc && chmod +x /usr/bin/ccc;. ~/.bashrc
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
