- Products
- Learn
- Local User Groups
- Partners
- More
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
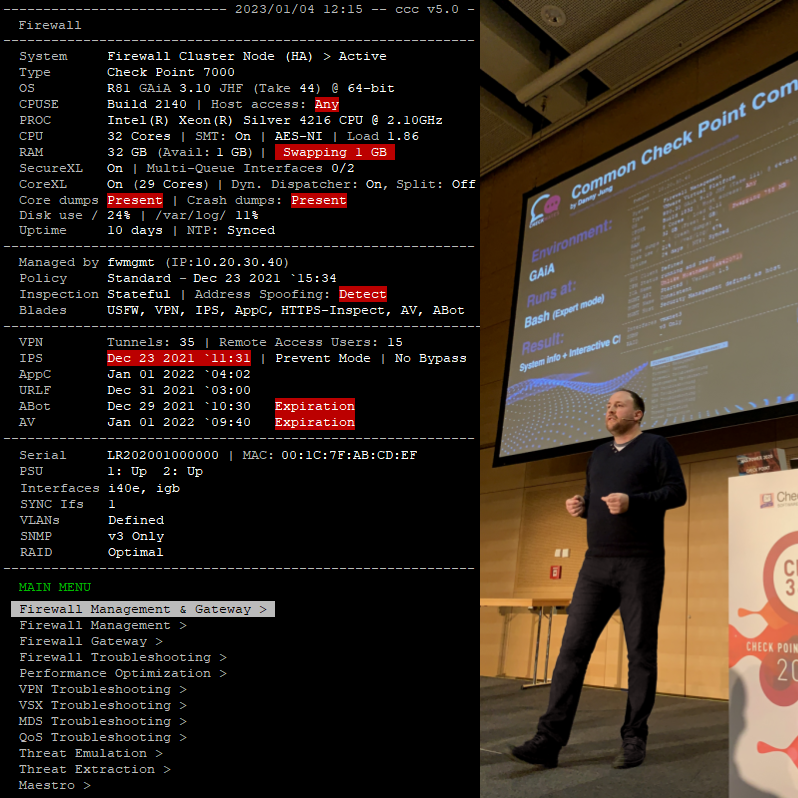
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle.crt https://dannyjung.de/ccc|zcat > /usr/bin/ccc && chmod +x /usr/bin/ccc;. ~/.bashrc
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle
![]() Thanks for this valuable feedback.
Thanks for this valuable feedback.
-> Please send me your local.set and I'll fix it asap.
![]() The anti-spoofing mode/setting is almost finished. Expect it to be released latest by tomorrow.
The anti-spoofing mode/setting is almost finished. Expect it to be released latest by tomorrow.
Hello Danny,
thank you for this great tool.
I have got a problem with ccc in a VSX environment.
I try to get the Topology from a Virtual System but always get the error " Main IP of name doesn`t match it`s management interface IP!".
The script is looking for the management IP of the VS0 in the "$FWDIR/state/local/FW1/local.set" of the VS2 in my case. There will be no positive match so that the script ends with this error.
If I comment out the check of the local.set it works without problems.
Could you change this in the next version?
Gruß,
Jan Kleinhans
Hello Danny,
thank you for this great tool.
I have got a problem with ccc in a VSX environment.
I try to get the Topology from a Virtual System but always get the error " Main IP of name doesn`t match it`s management interface IP!".
The script is looking for the management IP of the VS0 in the "$FWDIR/state/local/FW1/local.set" of the VS2 in my case. There will be no positive match so that the script ends with this error.
If I comment out the check of the local.set it works with
...;Hello Jan,
thank you for your feedback. You are referencing to my One-liner for address spoofing troubleshooting. Does the One-liner work when executed directly on VS2? Or does the error only occur when the One-liner is executed from within ccc?
Regards,
Danny
Hello Jan,
thank you for your feedback. You are referencing to my One-liner for address spoofing troubleshooting. Does the One-liner work when executed directly on VS2? Or does the error only occur when the One-liner is executed from within ccc?
Regards,
Danny
Hi Danny,
I created a one-liner that shows the VPN routing.
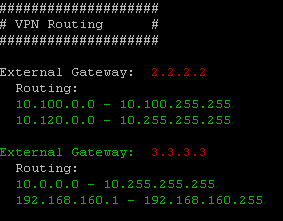
If you like, you can include this command in your script.
Regards,
Hi Danny,
I created a one-liner that shows the VPN routing.

If you like, you can include this command in your script.
Regards,
;I'm running R80.20EA in my lab and noticed the same thing. I made the following adjustment to the ccc script.
Updated:
# System info
TYPE=`cpstat os | grep "Appliance Name" | tr -s ' ' | cut -c 17-`
if [[ `echo $MDSDIR | grep mds` ]]; then SYSTEM="Multi-Domain Server (MDS)"
elif [[ `$CPDIR/bin/cpprod_util FwIsVSX 2> /dev/null` == *"1"* ]]; then SYSTEM="Virtual System Extension (VSX)"
elif [[ `$CPDIR/bin/cpprod_util FwIsStandAlone 2> /dev/null` == *"1"* ]]; then SYSTEM="Standalone Firewall & Management"
elif [[ `cpstat -f all ha | grep "HA started:" | tr -s ' '` == "HA started: yes" ]]; then MODE=`cpstat -f all ha | grep "Working mode:" | tr -s ' ' | cut -c 15,20`; STAT=`cpstat -f all ha | grep "HA state:" | tr -s ' ' | cut -c
11-`; STAT="$(tr '[:lower:]' '[:upper:]' <<< ${STAT:0:1})${STAT:1}"; SYSTEM="Firewall Cluster Node (${MODE}) - ${STAT}"
elif [[ `$CPDIR/bin/cpprod_util FwIsFirewallModule 2> /dev/null` == *"1"* ]]; then SYSTEM="Firewall Gateway"
elif [[ `$CPDIR/bin/cpprod_util FwIsFirewallMgmt 2> /dev/null` == *"1"* ]] && [[ `cpwd_admin list | grep -o CPSEMD` == "CPSEMD" ]]; then SYSTEM="Firewall Management (with Smart Event)"
elif [[ `$CPDIR/bin/cpprod_util FwIsFirewallMgmt 2> /dev/null` == *"1"* ]]; then SYSTEM="Firewall Management"
elif [[ `cpwd_admin list | grep CPSEMD | cut -c 1-6` == "CPSEMD" ]]; then SYSTEM="SmartEvent Server"
else SYSTEM="N/A"
fi
I'm running R80.20EA in my lab and noticed the same thing. I made the following adjustment to the ccc script.
Updated:
...;# System info
TYPE=`cpstat os | grep "Appliance Name" | tr -s ' ' | cut -c 17-`
if [[ `echo $MDSDIR | grep mds` ]]; then SYSTEM="Multi-Domain Server (MDS)"
elif [[ `$CPDIR/bin/cpprod_util FwIsVSX 2> /dev/null` == *"1"* ]]; then SYSTEM="Virtual System Extension (VSX)"
elif [[ `$CPDIR/bin/cpprod_util FwIsStandAlone 2> /dev/null` == *"1"* ]]; t
zcat: unexpected end of file
Below is the process that I did
STEP 01 : Download the script (ccc.gz)
STEP 02: Transfer the file to /usr/bin/ (Using WinScp)
STEP 04: Now decompress the file (zcat /usr/bin/ccc.gz > /usr/bin/ccc)
STEP 04: Now make it executable (chmod +x ccc) (chmod +x /usr/bin/ccc)
STEP 05: Now type ccc
NOTE : I am able to execute all the command but why i am getting "zcat: unexpected end of file" error while executing (ccc).
#Chinmaya Naik
zcat: unexpected end of file
Below is the process that I did
STEP 01 : Download the script (ccc.gz)
STEP 02: Transfer the file to /usr/bin/ (Using WinScp)
STEP 04: Now decompress the file (zcat /usr/bin/ccc.gz > /usr/bin/ccc)
STEP 04: Now make it executable (chmod +x ccc) (chmod +x /usr/bin/ccc)
STEP 05: Now type ccc
NOTE : I am able to execute all the command but why i am getting "zcat: unexpected end of file" error while executing (ccc).
#Chinmaya Naik
;Nice tool.
Unfortunately now we have two different Tools (sk121447) to check health state and troubleshoot the System.
I would suggest to add "fwaccel off" and "fwaccel on" when doing "ips off"
Further I would add the same for QoS:
fgate stat
fgate off
fgate on
same with fwaccel off/on
a command to show "fwkern.con" and "simkern.conf" could help, too.
I would be interested in what "PANIC MODE" and "NORMALE MODE" are doing. so perhaps add here and there some Information about the commands you use.
And - I did not test it - but perhaps add a user check before performing such Actions to make sure noone unexpectedly uses these commands.
When performing one Task of your script the Cursor is at the end of the Output but simetime you do not know if it has finished or not. so add a line "Task finished" or something similar at the end of every Task execution.
So really nice and helpful script. Go on with this good work!
Regards
Nice tool.
Unfortunately now we have two different Tools (sk121447) to check health state and troubleshoot the System.
I would suggest to add "fwaccel off" and "fwaccel on" when doing "ips off"
Further I would add the same for QoS:
fgate stat
fgate off
fgate on
same with fwaccel off/on
a command to show "fwkern.con" and "simkern.conf" could help, too.
I would be interested in what "PANIC MODE" and "NORMALE MODE" are doing. so perhaps add here and there som
...;If you like, then you can include Show bgp peers across VSX in CLI as well.
If you like, then you can include Show bgp peers across VSX in CLI as well.
;Added "cpqshape" commands as described in ATRG: Mail Transfer Agent (MTA) in version 2.9
Added "cpqshape" commands as described in ATRG: Mail Transfer Agent (MTA) in version 2.9
;I agree. You could send Check Point a Request for Enhancement (RFE) asking for this. Maybe someday Check Point will have the best Community scripts included by default.
Hmmm - R80.20 B10:
[Expert@SMS8010:0]# ccc
Starting/bin/ccc: line 21: bind: warning: line editing not enabled
.........free: invalid option -- 'o'
Usage:
free [options]
Options:
-b, --bytes show output in bytes
-k, --kilo show output in kilobytes
-m, --mega show output in megabytes
-g, --giga show output in gigabytes
--tera show output in terabytes
-h, --human show human-readable output
--si use powers of 1000 not 1024
-l, --lohi show detailed low and high memory statistics
-t, --total show total for RAM + swap
-s N, --seconds N repeat printing every N seconds
-c N, --count N repeat printing N times, then exit
-w, --wide wide output
--help display this help and exit
-V, --version output version information and exit
For more details see free(1).
..
--------------------------------------------- ccc v3.0 -
On the GW of the same version all is good:
[Expert@GW_80.10:0]# ccc
Starting................
--------------------------------------------- ccc v3.0 -
Hmmm - R80.20 B10:
[Expert@SMS8010:0]# ccc
Starting/bin/ccc: line 21: bind: warning: line editing not enabled
.........free: invalid option -- 'o'
Usage:
free [options]
Options:
-b, --bytes show output in bytes
-k, --kilo show output in kilobytes
-m, --mega show output in megabytes
-g, --giga show output in gigabytes
--tera show output in terabytes
-h, --human show human-readable output
--si use powers of 1000 not 102
Yes:
[Expert@SMS8010:0]# ccc
Starting/usr/bin/ccc: line 21: bind: warning: line editing not enabled
...........
------------------------------------------------ ccc v3.1 -
Great work Danny Jung !
@Checkpoint - give this man a medal ! ![]()
Whilst deploying the script to our devices and executing on version R77.30 , we had to change the script a little to get the correct Hotfix.
For some devices the 77.30 hotfix output is not correct when for example the CPUSE wasn't updated before installation of HFA - there is no installed_jumbo_take command. ( sk115719)
Have an extra request -> is it possible to build in a fool proof protection for critical commands like "CPSTOP" ?
Just to be sure ... - asking confirmation when running a critical command is not going to hurt anybody .
Then some additional info (bold text ) i added to the startup screen, to get a complete overview on the first screen - so administration is made a little easier .
And that gives me this output atm :
--------------------------------------------- ccc v3.0 -
Hostname
--------------------------------------------------------
System Firewall Gateway
Type Check Point 2200
Serial Number 1111B1111
Version Check Point Gaia R77.30 JHF (Take 185)
CPUSE Build 1130
CPU 2 Cores | SMT: - | Load: 0.25%
RAM 2 GB (Free: 0 GB) | Swapping: 0 GB
SecureXL On | Multi-Queue Interfaces: -
CoreXL On (2 Cores) | Dynamic Dispatcher: Off
Uptime 80 days
--------------------------------------------------------
Managed by Some_Management (IP: 192.169.1.1)
--------------------------------------------------------
Policy Some_Policy_Name
Installed Aug 21 2018 - 09:48:02
--------------------------------------------------------
Blades FW, VPN
--------------------------------------------------------
Mac Address 00:11:FF:FF:FF:FF
--------------------------------------------------------
I used following commands to collect the data :
(Command not tested yet for R80 , maybe we need to use the buildin OS verifier to check what command to use , but need more time ... )
Still need more more info when it's a VSX, come back on this later .
Regards,
Rolf
Great work Danny Jung !
@Checkpoint - give this man a medal ! ![]()
Whilst deploying the script to our devices and executing on version R77.30 , we had to change the script a little to get the correct Hotfix.
For some devices the 77.30 hotfix output is not correct when for example the CPUSE wasn't updated before installation of HFA - there is no installed_jumbo_take command. ( sk115719)
Have an extra request -> is it possible to build in a fool proof protection for critical comma
...;Added and improved in version 3.2, though I moved the CPUSE build info to the Firewall Management & Gateway submenu.
I'm not aware of any command to control Application Control / URL Filtering at the CLI. It should however be possible to change the setting for this Software Blade via dbedit and have the security policy reinstalled to the specific gateway afterwards.
I'm not aware of any command to control Application Control / URL Filtering at the CLI. It should however be possible to change the setting for this Software Blade via dbedit and have the security policy reinstalled to the specific gateway afterwards.
;About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
