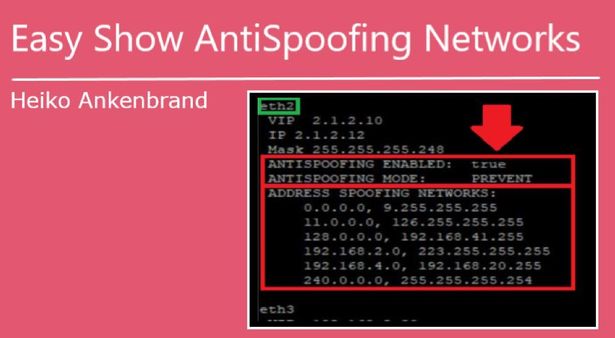
Cool command Heiko!
We build a Maestro Cluster (R80.30SP) with BGP activated between Checkpoint and Cisco switches.
The interfaces are configured to learn topology from routes and do Anti-Spoofing based on IF topology.
Routes will be exchanged correctly to and from Checkpoint VS.
When we had a configuration problem and one network was learned on two interfaces, we learned, that topology from routes are working fine because we got spoofing messages from one direction until we removed the advertisement for the second one.
Unfortunately in this configuration your command shows the AS configuration and the interface network but not the learned networks:
bond1.vvv
VIP a.b.c.148 VMAC address: 00:AA:BB:CC:DD:F6
IP a.b.c.148
Mask 255.255.255.248
ANTISPOOFING ENABLED: fo (true
ANTISPOOFING MODE: PREVENT
ANTISPOOFING TOPO: Internal
ADDRESS SPOOFING NETWORKS:
a.b.c.144, a.b.c.151
Do you see any chance to include the dynamic learned networks / anti-spoofing settings to be read out and added to this command?