- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Re: vpn-1 server could not find any certificate to...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
vpn-1 server could not find any certificate to use for IKE
Hi all,
I can't figure out what's going on and I hope someone here can help me. I have a 1570 with VPN blade active. My users are getting the following error msg "vpn-1 server could not find any certificate to use for IKE" when connecting with the checkpoint vpn client on mac or windows.
If I replace the certificate, they can connect but later get the error msg above when they reconnect.
If I reboot the router, it works fine, but then later fails with the same error on top when they reconnect.
I have 2 sites connecting to site to site and they work fine.
firmware version of the checkpoint is R81.10 (996000575)
Thanks
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
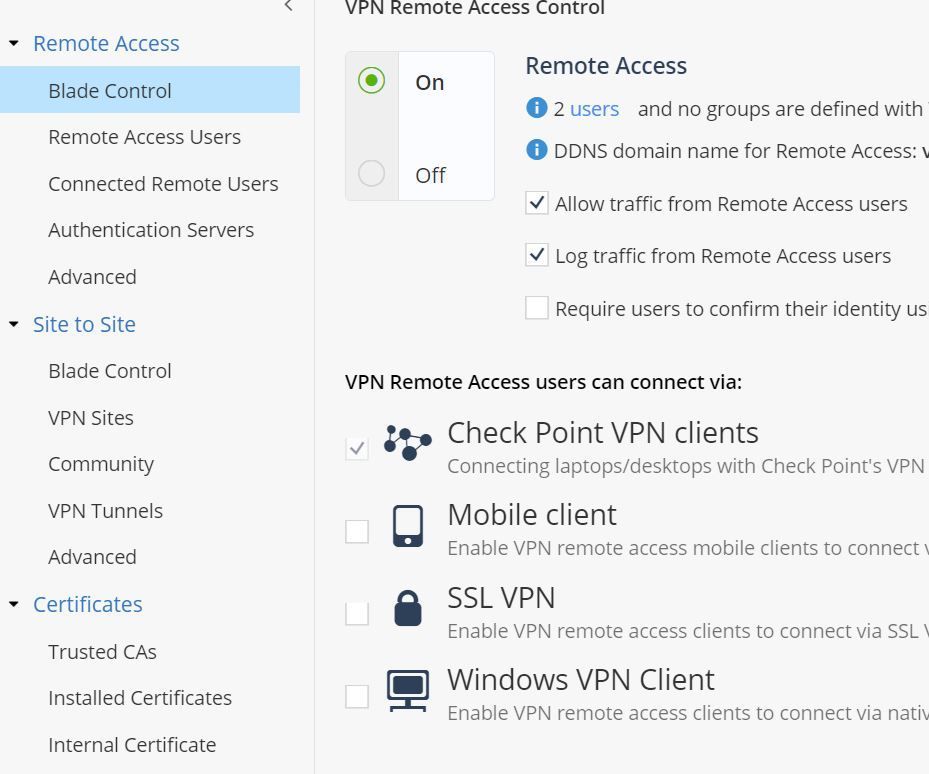
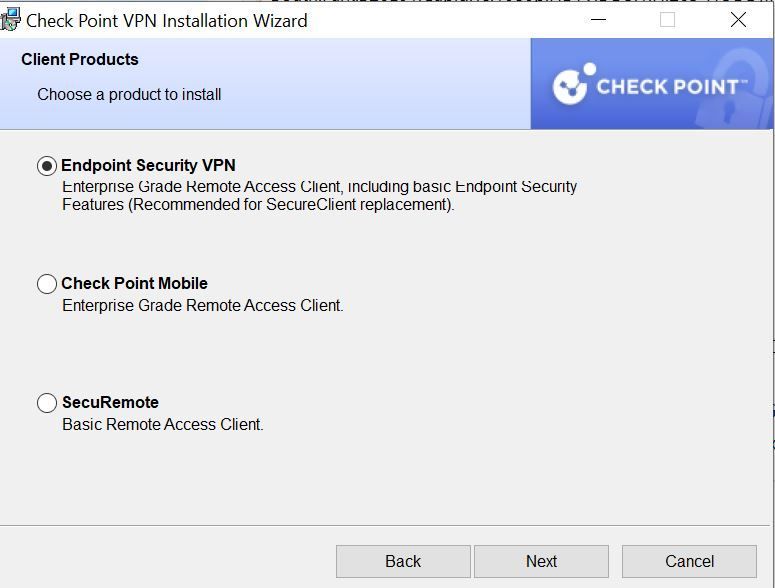
Adding more info here as I just realized something and might be onto something. When installing the client, we are proposed 3 options and the last 2 are handled differently by the firewall. This issue I'm having is with the 3rd option "SecureRemote" Basic Remote Access Client. When this connects, it connects to Mobile Access, which oddly enough is disabled on my firewall on the vpn blade but still allows me to connect. This also doesn't show me as connected in connected VPN users. Also, the ip address my client was getting was from my ISP modem 192.168.99.xxx even though the WAN port was set to PPPOE.
I uninstalled the client and reinstalled with the second option " Check point Mobile". This Version connects me to the firewall with no issues and I can see my user connected under Connected remote users. It also uses the configuration of the vpn blade for ip addressing ( 172.16.10.xxx)
@Dale_LobbWhich option did you select ?
38 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Typically this error does point to an issue with the certificates.
Out of interest which VPN client version is used here?
The newer R81.10.05 firmware (sk179797) is also worth considering if you want to exhaust options before consulting TAC.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was using 86.50 and just upgraded to 86.80 with the same issue. Interesting enough, I reinitialized the internal certificate and it works for 3 mins then fails again. If I disable and reenable the the VPN blade, it works then fails 3 mins later
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One of my customers had same issue 2 years ago and this is what TAC recommended to fix it and worked fine. IF you do this, MAKE SURE to back up everything (mgmt, gateways), just in case.
Process:
1. Open Guidbedit to network_objects -> Gateway_Object -> VPN -> isakmp.authmethods
- Change "signatures" to "pre-shared".
- Save and exit Guidbedit.
2. Open Guidbedit to network_objects -> Gateway_Object -> find certificates section
- Find defaultCert then right click and delete the cert, and save changes and close
3. Check to see if default cert is gone in SmartConsole - gateway object - IPsec VPN
- Create a new cert
- Install policy
4. Open Guidbedit to network_objects -> Gateway_Object -> VPN -> isakmp.authmethods
- Change "pre-shared" to "signatures"
- Save and exit Guidbedit.
- Install policy
5. Test VPN connection
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For context is the appliance locally or centrally managed?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Managed Locally
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nm then, process I gave wont apply, as guidbedit would not even come into place, since management part does not even exists. Personally, I would get on the phone and work with TAC, it sounds like a pretty serious issue that needs a remote session.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok Contacting TAC requires a subscription or contract support of some kind ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct, the same contract provides entitlements to software downloads / version upgrades.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats right...without it, they cant even open the case in the first place. Do you have a partner that you deal with that can open a case for you or no?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just called my partner and they will send me info to get added to their account to open TAC. In the meantime. I'm resetting factory and going to test where it messes up and post my results here as well as contacting TAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats a very good idea. Im sure if you factory reset an appliance, it will most likely work. I did some research for you before, but could not find much sadly on the issue you had. Since I dont have embedded gaia appliance to test anything myself, it would be very hard to say for sure why the issue happened in the first place.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In case you had not started reset yet, would you mind send us the screenshot of vpn certs showing in the GUI?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Reset already done 😕 I do have a backup of the device though
After resetting, I've had no issues and the clients can connect way after 3 mins.
It worth noting that I followed the link that phoneboy left in the issue I was having last Saturday which foxed that issue.
Other than that, nothing really fancy as setup wise on my end . Simple 3 vlan setup, 5 users for vpn and 2 site to site links
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Spoke to soon , it just failed again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you attach a backup, I can check tomorrow. By the way, sorry for my ignorance, Im not overly familiar with these embedded gaia appliances, but if you go to remote access vpn section, does it give a list of the vpn certs there?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good deal. Well, everyone knows phoneboy is right 99.999% of the time...only time I recall he was wrong was when he said that jumbo hotfixes are included in fw backup, other than that, cant ever remember him being wrong : -)
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
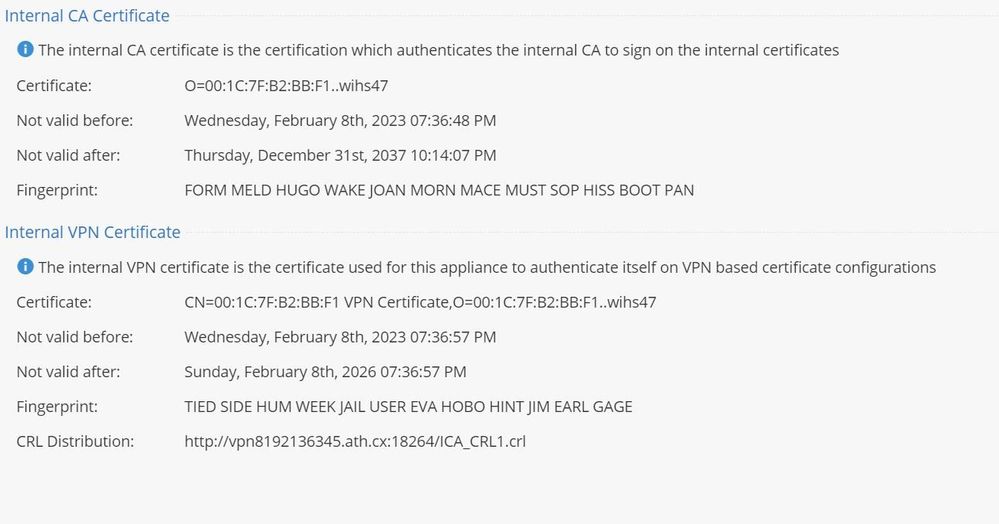
here is the capture of the vpn cert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Question...can you make sure users actually see the fingerprint when they connect to the site that matches one from the screenshot? Well, technically, they should ONLY see it the first time when creating a site before connecting.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a laptop beside me and I can confirm the thumbprint is correct
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The general fix for this issue appears to be going to Device > Certificates > Internal Certificate in the WebUI and click on Reinitialize Certificates.
That happens naturally when you factory reset the device.
I've also seen TAC cases that suggest the underlying issue may be a bug and there is a fix available.
Obviously, you can only open a TAC case if you have a support agreement (either directly or through your partner).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The fix works, but only temporary. I'm about to go back to version R80.20.15 (992001653) which is the factory defaults.
Hoping to have access to TAC soon.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since your device is locally managed, you might see if an fw_configload (from expert mode) also resolves the problem temporarily.
This is similar to what @Dale_Lobb is doing by pushing the policy from central management.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a similar issue with a pair of centrally managed 1550s running R80.20.50, operating in a ClusterXL cluster. The cluster is used for remote access for a small number of users via the Checkpoint mobile client. Every 3 to 11 days, all the clients start getting the exact same error. In my case, since the pair are centrally managed, pushing policy to them restarts the firewall daemon and resets the clock on the issue. So, we are proactively pushing policy to the cluster every three days to forestall angry users.
I had an open TAC case about the issue, which went on for several weeks before auto-closing without a resolution. The case's next steps would have me update the appliances to R81 to see if that fixes the issue, which I'm willing to do, but first have to arrange to upgrade our management system to R81, which is not quite as easy as upgrading the appliances. The fact that your appliance is already running R81 gives me some pause.
I am very much interested in what your outcome with TAC will be; please, please keep us posted on the findings. I realize our issues are not exactly alike, but hopefully there will be some cross-application. Hopefully I will get the time to upgrade our central management in the next week or two, and then i will reopen our TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would wait before applying the R81 update to the device. I just reverted back to R80.20.50 and connected to PPPOE and everything is working flawlessly. Have a look at the link I posted above about an issue that Ponyboy help me resolve for this week. Reverting back seems to have resolved my issue with my VPN client for now.
Your device is a 1550 and my older device is a 1530 and I never had that issue with VPN or my site to site. I don't have it setup in a cluster either. I will keep updates to this post should I have a desire to pursue R81
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats interesting, because Im sure if this was a known issue in R81 version, everyone who upgraded would have had this problem. Let us know what TAC says if you end up opening a case about it.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I didn't upgrade a configured checkpoint though. I started from scratch. The upgrade was done as soon as I was done the first configure stage. Who knows, but this week I wasn't impressed with it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Its is fairly new, lets hope all the bugs with it are fixed soon, we shall see : - )
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Went to bed last night feeling like a guinea pig. I troubleshot that issue all week thinking it was a Mac issue. Its not always the best to upgrade right away.
As of this morning, users are coming in with no browsing issues, and all connecting with the VPN client.
I also received my link to activate my account for TAC access and I get an error from their website site that they can't process my request. Click here to activate your account. Then it just loops with e-mails.
/facepalm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to make sure we got all the facts straight, as they say : - ). So, currently firmware is R80.20.50 and users connect to the site fine and stay connected, no issues?
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 |
Upcoming Events
Wed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter