- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Re: SMB HTTPS logging & other issues
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SMB HTTPS logging & other issues
Hello,
I'm seeing some very odd (to me) behaviour with a locally-managed 1450 appliance. I've just re-flashed it using the USB method so that it has a clean install of R77.20.87 (990173120). Although I did re-import my config after.
To begin with, I see no HTTPS logs whatsoever in the Security log. All my blades/rules have all logging enabled. I even turned on implied rule logging for a time to see if it helped but it didn't really. I saw a bunch more DNS requests and my WebUI activity.
For me to see any HTTPS logs I put a rule at the top of the rulebase disabling all access for the specific host, and then I see some generic HTTPS info at least.
For a long time now, even when HTTPS logs were working, I never get any category or URL information. Is "HTTPS Categorization" mode supposed to be able to do anything these days? I know there are SK articles about CA fixes, etc., but I wasn't sure if they would fix my issues.
I've dabbled with enabling SSL inspection but it doesn't suit my purposes right now.
There definitely seems to be an issue with my HTTPS and especially it's logging.
Thanks for your help
26 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
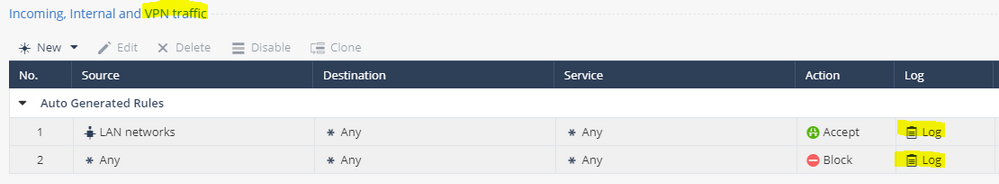
I don't see any VPN traffic either, until it's dropped traffic using the rule I mentioned above. I don't see any allowed Wireguard or OVPN traffic. But I see all of the dropped attempts.
I have licenses for all of the blades, active until 2024, if that matters.
Thanks...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
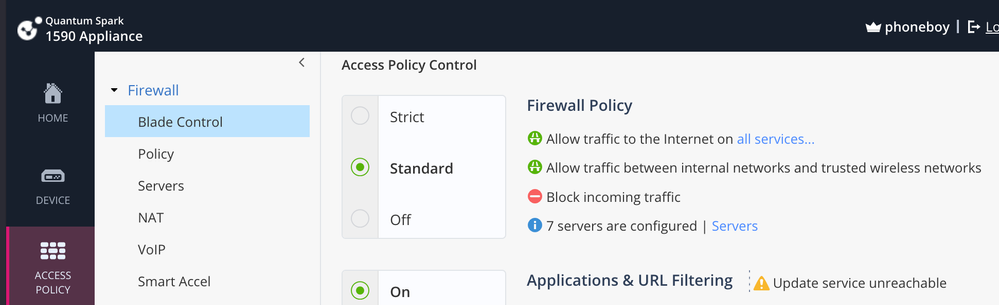
What is this setting?
And, also (on the same screen):
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Yes I have all of the expected logging settings enabled, which is why this is so perplexing. Anywhere a log can be enabled, it is.
Maybe it's an issue with how I have service/application groups nested in the rules. I'll try separating them out.
Thanks,
Nathan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your only option on the 1450 is to enable HTTPS Inspection.
HTTPS Categorization in R77.20 uses the CN of the certificate to categorize websites.
R77.20 does not support SNI-based categorization that is available in newer SMB appliances running R80.20.x or R81.10.x.
1400 Series Appliances are End of Engineering Support, meaning no further software updates are planned aside from bugfixes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That makes sense, but what about the other logging behaviour? I don't see any VPN traffic whatsoever, not even encrypted packets crossing. I only see details of these packets when I put a rule at the top of the rulebase denying the traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Note for reference a newer R77.20.87 build 990173127 is available for 700 / 1400 appliances (per sk176148 contact Check Point Support to get it).
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good advice, that can only help!
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks. Looks like a lot of good fixes in that, specifically for HTTPS. My certs expired and so I don't have access to open a request to get it anymore, so I'll have to sort something out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was able to get the mentioned fix installed. Doesn't appear to be any fix for my logging issues.
Am I not supposed to see logs for encrypted traffic? I realize I won't see what's inside, but shouldn't I still see reference that encrypted data is traversing my interfaces? I see it in packet captures.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Im fairly positive you should be able to see it. Do you not see any of those at all? Did it ever work?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As @PhoneBoy posted: Your only option on the 1450 is to enable HTTPS Inspection.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To re-clarify: I'm talking about all encrypted traffic. I don't see any logs whatsoever showing VPN encrypted traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just my personal opinion, but I could be mistaken, though, I dont see logically why you would need https inspection on for this to work. I dealt with God knows how many clients who did NOT have inspection on their firewall and this worked without any issues.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
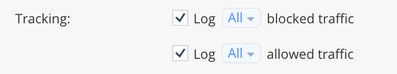
Further to @PhoneBoy earlier post you have your policy/rules set to log in the following section correct?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct. All rules are set to log. Implied rule logging is enabled. Global "log all" settings are set to YES. It's as if as soon as any encrypted traffic his an 'allow' rule, logging goes away for that connection. If I put a 'deny' rule for any of this traffic, I start seeing logs again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As an example for OpenVPN (UDP/1194) I would only expect to see an entry for the start of the long lived connection/session. Are you not seeing this or are you expecting something more here?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Chris,
I don't see any reference to the connection whatsoever. Someone unfamiliar with my environment would have no idea the connection was even taking place. I don't want to add more confusion to this discussion, but I think there is a bigger issue with my logging. Many other small things don't get log entries either, but the biggest issue is the encrypted traffic. I thought maybe I messed with some CLI global settings, which is why I factory reset the device with a new image on USB, but that didn't seem to help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
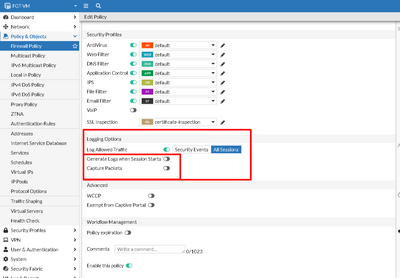
I know, for example, on Fortigates, you have an option like below, but Im fairly positive that is not there on SMB appliances (I dont have access to one to confirm):
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I haven't found any reference to a setting like this, or in the advanced settings. Maybe there are other CLI options available outside of the GUI "advanced settings". Not sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I had access to SMB appliance, I would be able to tell. Sadly, dont believe you can create VM with one of those images. Unlike Fortinet, where anyone can access free online demo appliance to check out all the fw capabilities, that does not exist on CP side, so my apologies mate Im not able to confirm that for you. Maybe someone else can verify.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are "Quantum Edge" GAiA embedded images available for ESXi moreover there is also an online Demo 1500 appliance that partner engineers can connect to (contact your SE for more info).
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Chris, did not know that. Will email couple of SE guys we deal with often and ask about the online demo, it would be useful.
Appreciate the info 🙏
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Huh, today I learned @Chris_Atkinson
If you have access to Techpoint, @the_rock, then you can fire it up yourself on demand:
See also the lab guide.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @PhoneBoy , will give it a go in a bit and see what happens.
I was hoping there was a free online demo, would be easier, but, o well : - )
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I will say it again...you are the BEST!! That was super easy, thanks again 👍👍🙌🙌
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 4 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Wed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter