- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Re: NAT and VPN Site-to-site with a managed SMB
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
NAT and VPN Site-to-site with a managed SMB
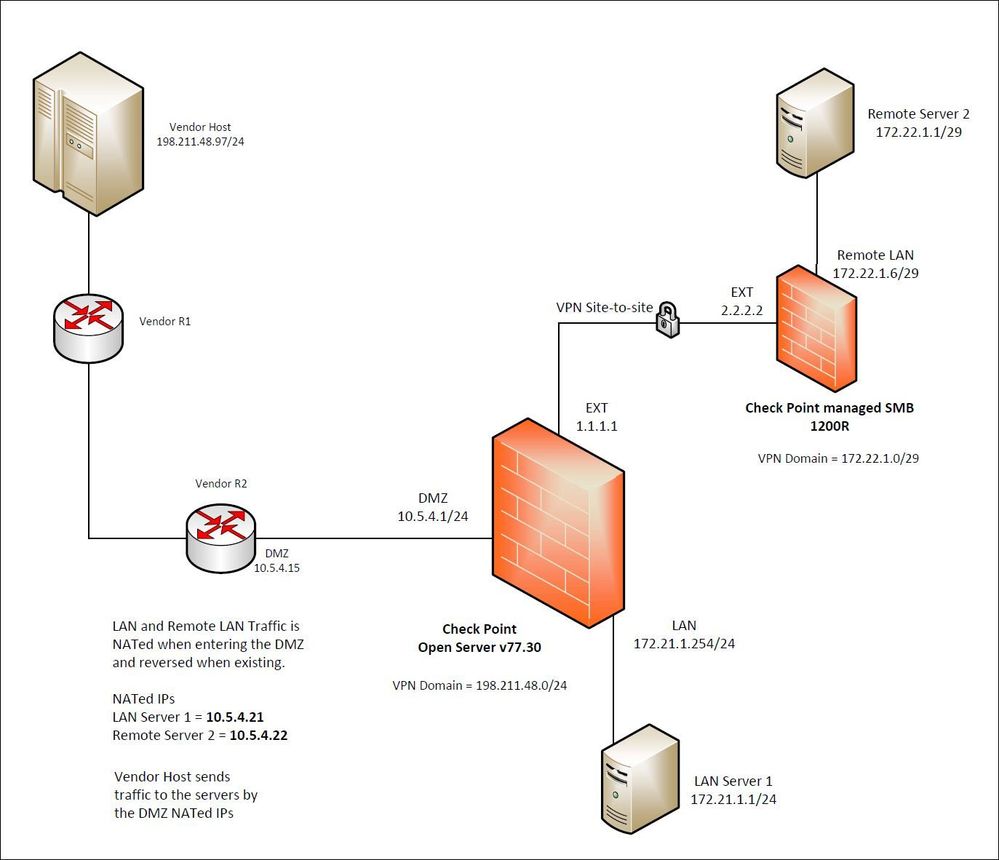
We recently got the 1200R SMB that is managed by the management server. We want to use the SMB to connect the remote site with the headend Check Point open server at the data center.
We ran into the issue that the vendor host cannot talk to the remote server 2 by the NATed IP (10.5.4.22). However, I can ping from the remote server 2 (172.22.1.1) to the vendor host (198.211.48.97). The vendor host can talk to LAN server 1 (10.5.4.21) without any issue.
I think there is an issue to NAT and VPN egress out to the remote site on the same Check Point FW.
I am not sure if I can remove the NAT and have the vendor host talks directly to the remote server 2 IP (172.22.1.1).
Can someone help me figure out what is the problem?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally, I was able to resolve the issue with tech support. It appeared the NATed address (10.5.4.22) for the remote server 2 is required to be part of the VPN domain on the remote Check Point SMB. In addition, the "Disable NAT inside the VPN community" must be unchecked in order to allow the NAT traffic reaching the destination IP.
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there,
To be able to assist you fully, could you please answer the following questions:
1) Is there a firewall rule on the Check Point Open Server that allows the vendor host to initiate traffic?
2) Have you ruled out that there are no issues with the intermediary routers before the open server (by running a traceroute or pathping)?
3) What type of traffic have you attempted to send from the vendor host to the remote server 2?
4) What do the logs show? Could you attach a couple of screenshots?
5) Is NAT disabled on the VPN or not?
6) Can the vendor host communicate with any other nodes behind the SMB gateway?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here are the answers:
1) Yes, firewall rule allows 198.211.48.0/24 from vendor
2) Yes, I saw traffic from Src:198.211.48.97 Dst: 10.5.4.22 XlateDst: 172.22.1.1 Origin: Check Point open server
3) It's TCP traffic on high port, say 2020; but doing ping ICMP traffic during the troubleshooting.
4) The log show Accepted on rule XXX and the content is listed on answer #2 above. I can do screenshots but I renamed all the IP info, so it may not too helpful.
5) In the Star Community object "Vendor-Remote", the "Disable NAT inside the VPN community" checkbox is checked
6) No, the vendor host traffic cannot reach anything on the SMB side
1) Yes, firewall rule allows 198.211.48.0/24 from vendor
2) Yes, I saw traffic from Src:198.211.48.97 Dst: 10.5.4.22 XlateDst: 172.22.1.1 Origin: Check Point open server
3) It's TCP traffic on high port, say 2020; but doing ping ICMP traffic during the troubleshooting.
4) The log show Accepted on rule XXX and the content is listed on answer #2 above. I can do screenshots but I renamed all the IP info, so it may not too helpful.
5) In the Star Community object "Vendor-Remote", the "Disable NAT inside the VPN community" checkbox is checked
6) No, the vendor host traffic cannot reach anything on the SMB side
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is client side NAT enabled?
Do you see an ARP for the NATted server? fw ctl arp
When you check the logs do you see the NAT being executed? Add the XLATED source and dest columns to your tracker view
do you have the source network in the local VPN domain of your open server gateway?
Do you use automatic NAT? (added the NAT IP on the object of that remote server?)
Do you see an ARP for the NATted server? fw ctl arp
When you check the logs do you see the NAT being executed? Add the XLATED source and dest columns to your tracker view
do you have the source network in the local VPN domain of your open server gateway?
Do you use automatic NAT? (added the NAT IP on the object of that remote server?)
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes to all the questions except the below question.
> Do you use automatic NAT? (added the NAT IP on the object of that remote server?)
No. I created a manual NAT. But since you asked, I just added the auto NAT 10.5.4.22 for the remote server 172.22.1.1.
I can currently ping from the remote server to the vendor host, I assume the manual NAT is working fine. I do know v77.30 has the NAT issue that requires adding the auto NAT prior to the manual NAT in order to make it functional.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When you use Manual NAT with R77.30 you need to create a proxy arp, that part is done automatically when you use Automatic NAT, therefore it works when you add this NAT IP to the object.
VPN Domain, ok that is how it should be.
Be aware that when you add proxy arp entries, you need to make sure in the Global Properties the setting to add the local.arp entries is ticked. After adding proxy arp entries, do not forget to push policy, as they will only be activated after a policy push.
VPN Domain, ok that is how it should be.
Be aware that when you add proxy arp entries, you need to make sure in the Global Properties the setting to add the local.arp entries is ticked. After adding proxy arp entries, do not forget to push policy, as they will only be activated after a policy push.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I have the Proxy ARP setup for both 10.5.4.21 and 10.5.4.22. Is there a way to check the local.arp?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw ctl arp
That is the command to see which Proxy ARP's are available.
PS. the best command for theProxy ARP is:
add arp proxy ipv4-address 123.123.123.121 macaddress 00:1c:7f:11:22:33 real-ip 123.123.123.123
That is the command to see which Proxy ARP's are available.
PS. the best command for theProxy ARP is:
add arp proxy ipv4-address 123.123.123.121 macaddress 00:1c:7f:11:22:33 real-ip 123.123.123.123
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ok, I already ran fw ctl arp and saw the entry for 10.5.4.22
What do you think the issue is about? I only have the one-way traffic from remote server 2 to the vendor host.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
> do you have the source network in the local VPN domain of your open server gateway?
Just to clarify for the above question, the source network of the vendor host subnet 198.211.48.0/24 is in the local VPN domain of the open server gateway as shown in the picture.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would involve TAC here - they could possibly resolve this issue in a short RAS...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I already opened a case without a resolution. I hope we have more brains here for inputs and suggestions to figure out what’s the issue. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally, I was able to resolve the issue with tech support. It appeared the NATed address (10.5.4.22) for the remote server 2 is required to be part of the VPN domain on the remote Check Point SMB. In addition, the "Disable NAT inside the VPN community" must be unchecked in order to allow the NAT traffic reaching the destination IP.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter