- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Re: IPS Bypass.
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
IPS Bypass.
Good night.
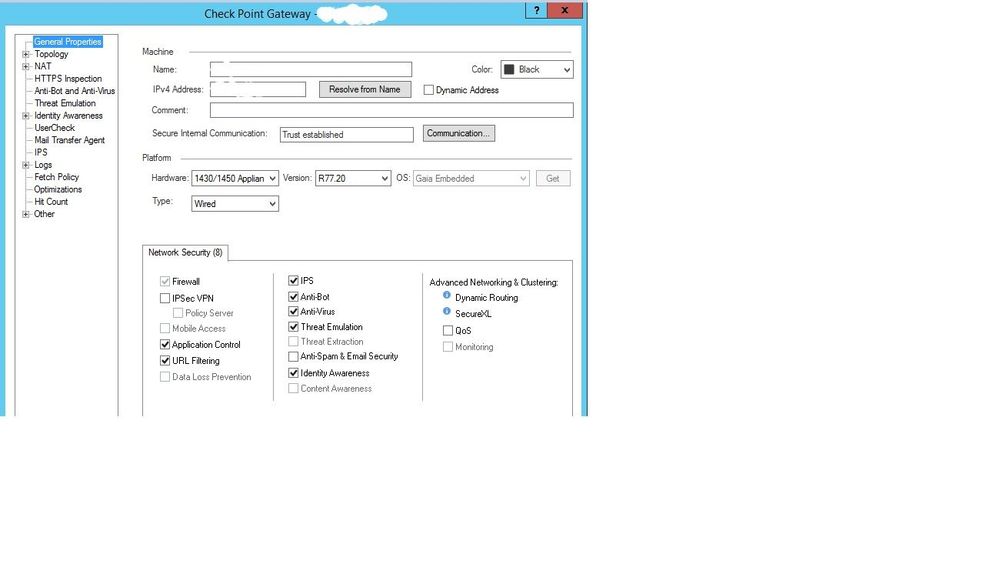
We have some branch office firewalls using R77.20.
The equipment model is 1450.
SMS uses version R80.10.
Sometimes IPS BYPASS happens and analyzing the logs is reporting high CPU consumption.
The problem is that every time I see the CPU consumption in the MONITOR CPU consumption is low.
Since the MONITORING blade is disabled on the firewall, I can not see the CPU usage history on the MONITOR.
In some research I found that the cause might be that in firewalls with more than one processor, even if the overall CPU utilization is low if one of the cores reaches a high value the firewall can activate the BYPASS IPS.
The problem may be caused by some process trapped in a particular CPU.
The problem reaches firewalls using version R77.20.
Is there any way to check CPU history via CLI?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The sar command is not available on SMB devices GAiA Embedded. I use a little script (attached) that notes every 30s the output from cat /proc/meminfo, cpstat os -f multi_cpu, top -n1 -b, ps auxf and the time of the generated output. You can change to record data in other intervals or change commands.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't believe this is possible on the SMB appliances, which do not support Monitor Blade or cpview.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Monitor blade is not disabled, it is just missing 🙂
The only way to monitor CPU usage over time is via SNMP.
If bypass happens for brief period of time there is nothing to worry about. But if it is for long time then you shall investigate it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
See if the sar command is available on embedded Gaia, if present there should be 30 days of system history including CPU utilization per core. Really don't recommend enabling the IPS Bypass feature since as you mentioned all it takes is just one CPU to exceed the high utilization water mark to disable/bypass IPS enforcement on ALL cores...
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The sar command is not available on SMB devices GAiA Embedded. I use a little script (attached) that notes every 30s the output from cat /proc/meminfo, cpstat os -f multi_cpu, top -n1 -b, ps auxf and the time of the generated output. You can change to record data in other intervals or change commands.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I also keep IPS Bypass disabled here but for different reasons. 1. Don't want to compromise security and 2. Don't think CPU usage is definitive criteria to disable it, load average is better indicator.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am having a similar problem in my lab immediately since I upgraded to r80.40 take 91. I didn't use to get IPS bypass events in take 87.
There is almost not traffic - 20 concurrent tcp sessions coming from one host I use for testing - and the cpu is idle most of the time. I see the cpu sometimes reaches 40% in cpview historic data.
I am certain the issue has to do with take 91 but I was wondering if there is a way to get more verbose logging to see how the system decides to bypass the IPS blade.
In a lab environment with almost not traffic, only one user, what % of packets is expected to go through the slow path? I have URL filtering, Anti bot , Antivirus, IPS enabled. I have disabled HTTPS inspection recently.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you talking about R80.40 JHFA 91 on your management server?
Because original post was about SMB appliance running embedded R77.20, so not likely to be relevant issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
okay
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter