- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Re: Attack detected by IPS: TCP Urgent Data Enforc...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Attack detected by IPS: TCP Urgent Data Enforcement
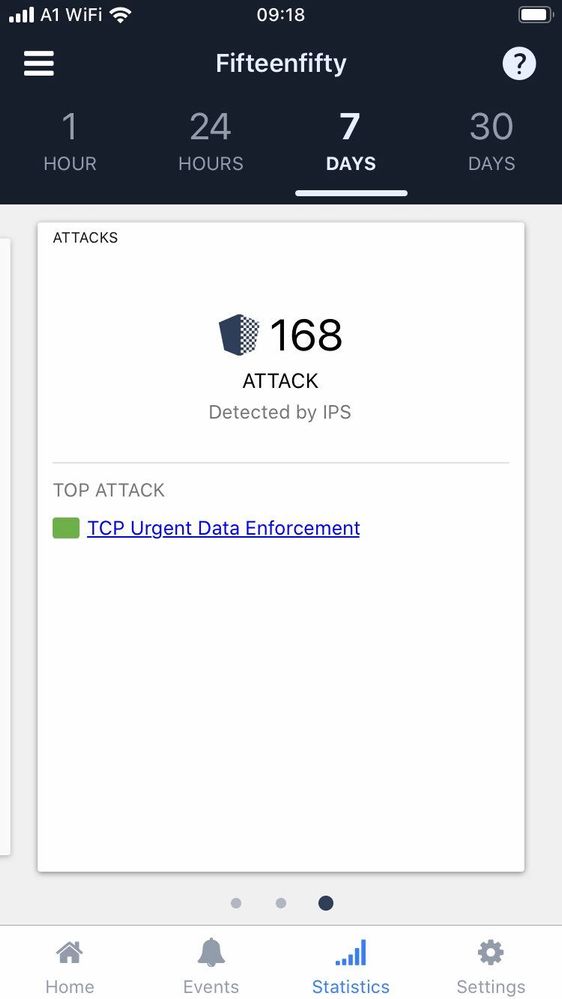
Testing the WatchTower App, Statistics page started showing a strange attack:
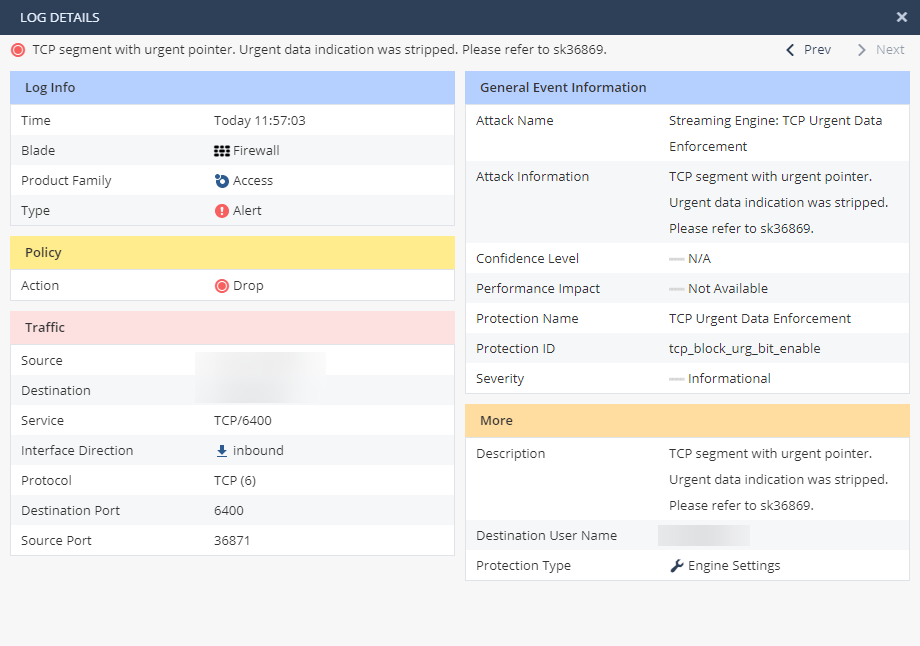
But IPS Protections do not include this attack ! But we have an SK to the rescue: sk36869 "TCP segment with urgent pointer. Urgent data indication was stripped. Please refer to sk36869." log in SmartView Tracker / SmartLog
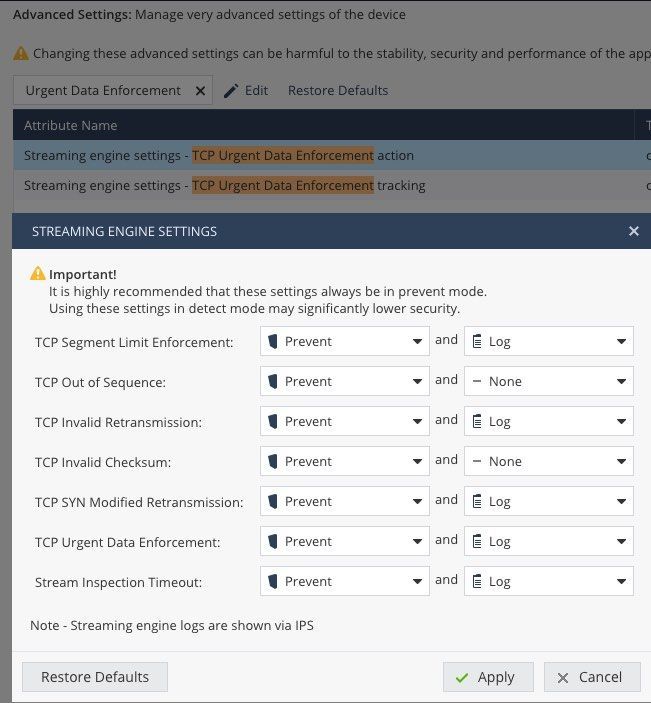
This includes a hint for Locally Managed 600 / 700 / 1100 / 1200R / 1400 appliances - and look where this is hidden:
It is the TCP streaming engine, stupid 😅 !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As you probably know, some IPS signatures are actually lower-level firewall checks.
On regular R80.x gateways, these would be in Inspection Settings or even Core Protections.
On regular R80.x gateways, these would be in Inspection Settings or even Core Protections.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm having an issue related to the "TCP segment with urgent pointer" protection, I have an app that's using the rlogin protocol on an non default port.
Does anyone knows if it's possibly make an exclusion for this core protection on the SMB firewalls? We are using an 1800 (R81.10 (996000575)), since this protection it's not directly related to the IPS blade I can't create an exception for it.
The log mentions the sksk36869, but this sk only explains how to change the fw to not strip the tcp urgent flag.
I would like to keep that protection active and make only an exception for the required flow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think in the context of locally managed devices atleast you only have the option of Detect vs Prevent here (for this protection in Advanced settings). Nothing I can find in the CLI or Web UI suggests differently unfortunately.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You should be able to apply the require change for the specific port in $FWDIR/lib/user.def on the SMB appliance for the specified port (which you say is non-standard).
The (undocumented) command fw_configload can be used to recompile the policy with this change.
For an exception that can be configured via the WebUI, this is quite likely an RFE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the information, I noticed that in the sk36869 it says:
Procedure for Locally Managed Quantum Spark appliances with Gaia Embedded OS
Connect to the Gaia Portal on the appliance.
Go to the "Device" tab.
Click "Advanced Settings".
Search for "Streaming Engine Settings".
Change the value of "TCP Urgent Data Enforcement" from "prevent" to "detect"
Despite that information I tried to configure the user.def but it didn't work, the fw still classifies the tcp port an attack.
#ifndef __user_def__ // tcp_urgent_ports_user={<6400;URGENT_DATA_INLINE>}; #endif /* __user_def__ */ |
It seems I will have to keep the global TCP Urgent Data Enforcement protection disabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you execute fw_configload after making the change and wait a few minutes before trying?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I did run the fw_configload command and the policy was loaded without any errors.
After some minutes I also changed the advanced settings " TCP Urgent Data Enforcement " from detect to prevent and the test was done after 5 minutes since the last policy change.
I'm assuming the changes made from the webgui call the fw_configload to load the policy, and the changes in the user.def are also reflected in the policy installed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, when you make changes in the WebUI that require access policy changes, they will be compiled and installed in the background.
I believe "fw stat" will actually confirm the last time the policy was compiled/installed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is not possible as it is the same Advanced Setting as above: sk36869 mentions TCP Urgent Data Enforcement - setting this to detect should be the solution, but exclusion is not possible. You can ask TAC, though...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter