- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: multiple VPN IPsec : select one tunnel in func...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
multiple VPN IPsec : select one tunnel in function of the source subnet
Hello everybody,
I have a simple question on a Checkpoint VPN functionality. If you have more than one tunnel, is it possible to select one tunnel in function of the source subnet ?
Here is the context of my request :
On my network, I have an IPsec tunnel between a Security Gateway Virtual Edition and a cluster of two Checkpoint 2200 T-110. Each member of the cluster build his own tunnel with the Security Gateway VE.
I would like to set up a new Security Gateway Virtual Edition and buid new tunnels with this VM. The need is to split trafics from different network and have them arrive on two separate platforms.
My whish is that hosts belonging to the subnet 192.168.30.0/24 use IPsec_tunnel_A and hosts from subnets 192.168.40.0/24, 10.20.0.0/16 use the new IPsec_tunnel_B.
I didn't succeed in setting up this idea. Do you know if this is possible ? All my devises works on Gaia OS 77.30.
Thank you for your help.
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I’m understanding what you’re asking, you’re trying to create two VPN tunnels to same encryption domain.
In which case, I would review the Multiple Entry Point configuration options here: VPN R77 Versions Administration Guide
If this isn’t what you are asking, please clarify by providing more details about what you’re trying to achieve and why.
A diagram showing the gateways, subnets, and desired traffic flows would also be very helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Main question here is where do the subnets live? Is subnet 192.168.30.0/24 (Indirectly) connected to the first VE and subnets 192.168.40.0/24, 10.20.0.0/16 (indirectly) connected to the second VE?
If so then there is no issue at all and you can just make sure the routing is set accordingly on the VE side and on the VPN domains you set the correct networks for the 2 VE's, (which network can I reach via which VE).
Hope this helps getting you in the right direction.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
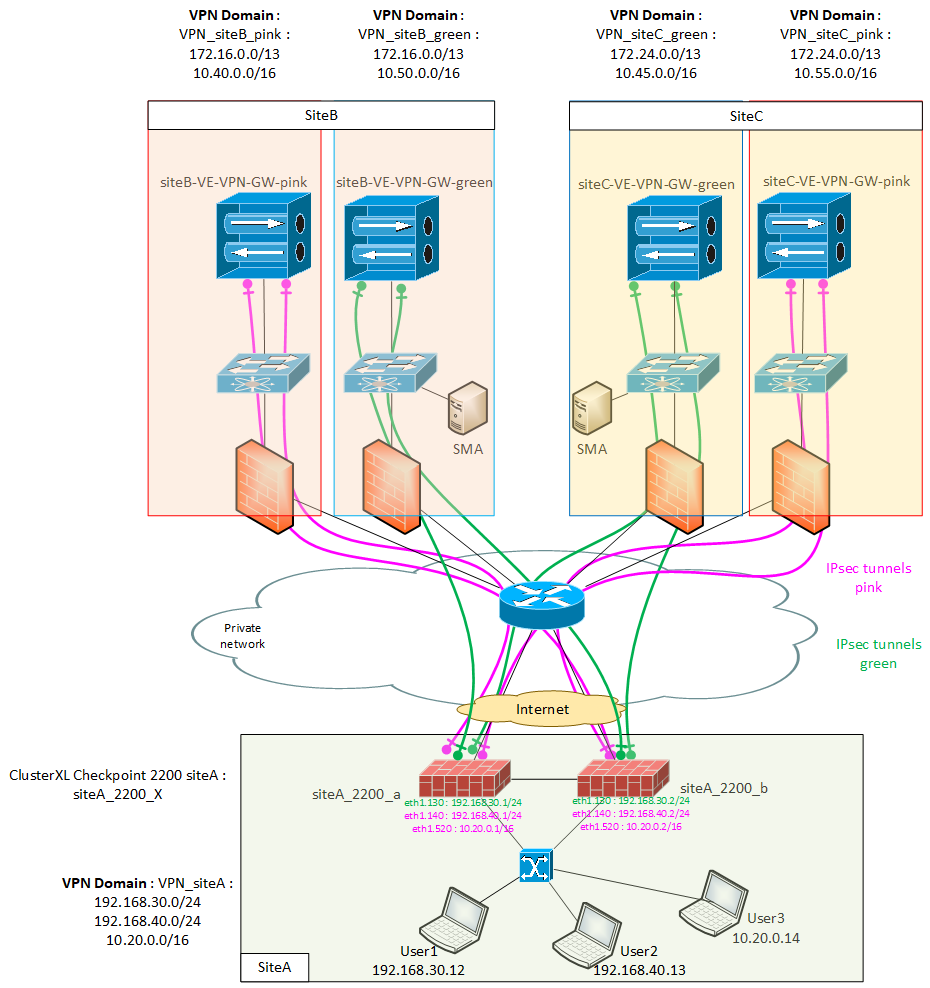
Thank you for your first answers. I attach a complete diagram of my situation (sorry for the blue stencils...).
For now I only have IPsec tunnels in green. I need to split trafic from users of SiteA.
I would like that User1 only use green tunnels whereas User2 and User3 should only use pink tunnels.
The demande comes from security department : they ask that admin users (from subnet 192.168.30.0/24) use a different VPN gateway from non-admin users (from subnets 192.168.40.0/24 and 10.20.0.0/24).
So do you think that it is possible for the cluster XXX to choose green or pink tunnel in function of the source subnet which is sending a request/reply (and in function of the destination of course) ?
For example User1 and User2 need to reach the server 172.16.0.9, can we force User1 to take green tunnel and User2 to take pink tunnel ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have partially overlapping encryption domains, which is not supported.
Specifically:
- VPN_siteB_Pink and VPN_siteB_Green share 172.16.0.0/13
- VPN_siteC_Pink and VPN_siteC_Green share 172.24.0.0/13
The encryption domains either have to fully overlap or not overlap at all.
If they don't overlap at all, you can set it up so the relevant group can use only the relevant VPN--problem solved.
If they fully overlap, then there isn't a way to force specific subnets to use a specific VPN tunnel (through MEP or any other method).
A better approach in this case would be to have admins use a Remote Access VPN client to access the desired gateway (e.g. through Mobile Access Blade or similar).
Then you can leave the encryption domains as "partially overlapping."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you again for your useful explanations and for your substitution proposal.
I understand that it is not possible to partially overlap encryption domains. And it is not possible de choose specific VPN tunnel neither.
I have notice that I could use Remote Access VPN client to access the desired gateway. In my situation, it is not an easy job considering the large amount of users involved for the heavy client installation.
I think to another possibility : is that possible to define two Virtual System on the Checkpoint 2200 to workaround ?
I would have four virtual firewalls on my site A (siteA_2200_a_vsxAdmin + siteA_2200_a_vsxNonAdmin + siteA_2200_b_vsxAdmin + siteA_2200_b_vsxNonAdmin) used to buid four IPsec tunnels to site B and four IPsec tunnels to site C. In this case I would have no limitation of encryption domains overlapping because all tunnels in destination to site B or all tunnels in destination to site C will be on different equipments. Is that correct ? If yes, do you know the license to activate VSX on 2200 models ?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I found the licences informations (they are noticed in the correponding model datasheet).
Check Point 2200 appliance : virtual system package
3 Virtual Systems package : CPSB-VS-3
3 Virtual Systems package for HA/VSLS : CPSB-VS-3-VSLS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Or you could use VSX ![]()
I would make sure you add additional RAM to your 2200 as that will obviously require a bit more RAM.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK great. I have all the information to choose a solution that meets my needs.
Thank you Dameon and Maarten for your help.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


